Ring3API 🇺🇦
@ntlmrelay
#ThreatHunting / #BlueTeam engineer. I'm just looking for traces in the logs. Reading and retweeting cool stuff.
MITRE ATT&CK Defender:CTI,SOCAsses,AE,PTM,THDE.
ID: 394156689
https://twitter.com/ 19-10-2011 17:12:20
14,14K Tweet
6,6K Takipçi
2,2K Takip Edilen




Europol and Latvian law enforcement dismantled five servers, seized 1,200 SIM box devices and 40,000 active SIM cards. The criminals were linked to over 1,700 cyber fraud cases in Austria and 1,500 in Latvia, causing losses of several million euros, including EUR 4.5 million in

I feel like Yuval Gordon's briefly mentioned new dMSA account takeover mechanism in his last blog didn't get enough attention. A new account takeover mechanism is on the horizon. I wrote a blog detailing it, releasing with a new BOF I wrote called BadTakeover specterops.io/blog/2025/10/2…




Credential Guard was supposed to end credential dumping. It didn't. Valdemar Carøe just dropped a new blog post detailing techniques for extracting credentials on fully patched Windows 11 & Server 2025 with modern protections enabled. Read for more ⤵️ ghst.ly/4qtl2rm





Forget common backdoors — a DLL hijack in Windows Narrator can grant SYSTEM-level persistence at login. In our new blog, Oddvar Moe shows how attackers abuse accessibility features and what defenders should monitor. Read now! trustedsec.com/blog/hack-cess…


AdminSDHolder: the AD security feature everyone thinks they understand but probably don't. 😬 Jim Sykora went to the source code to debunk decades of misconceptions — including ones in Microsoft's own docs. Read more ⤵️ ghst.ly/3Lpmjzv




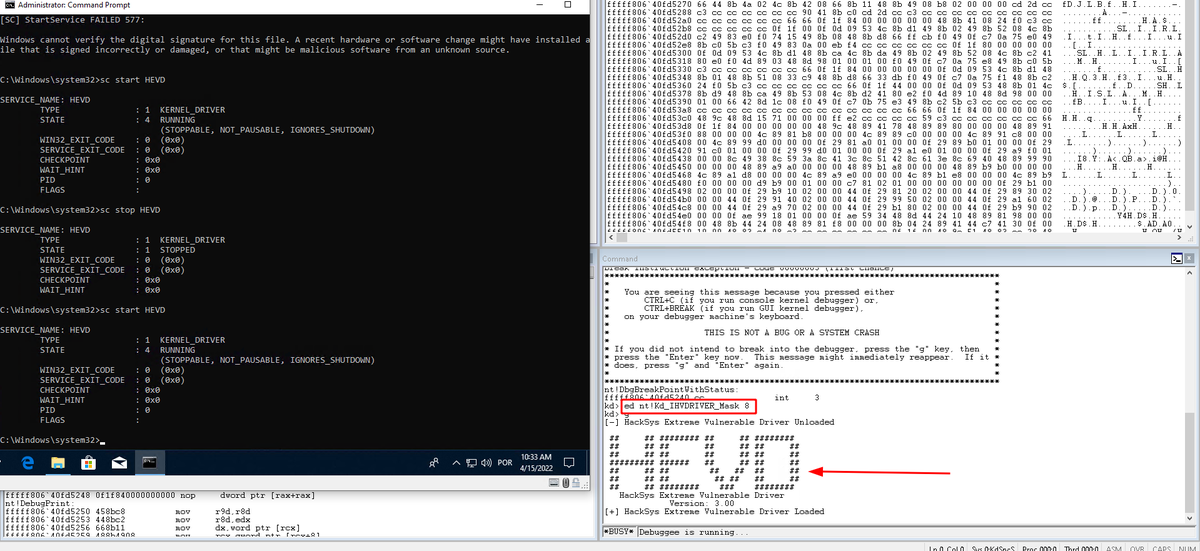
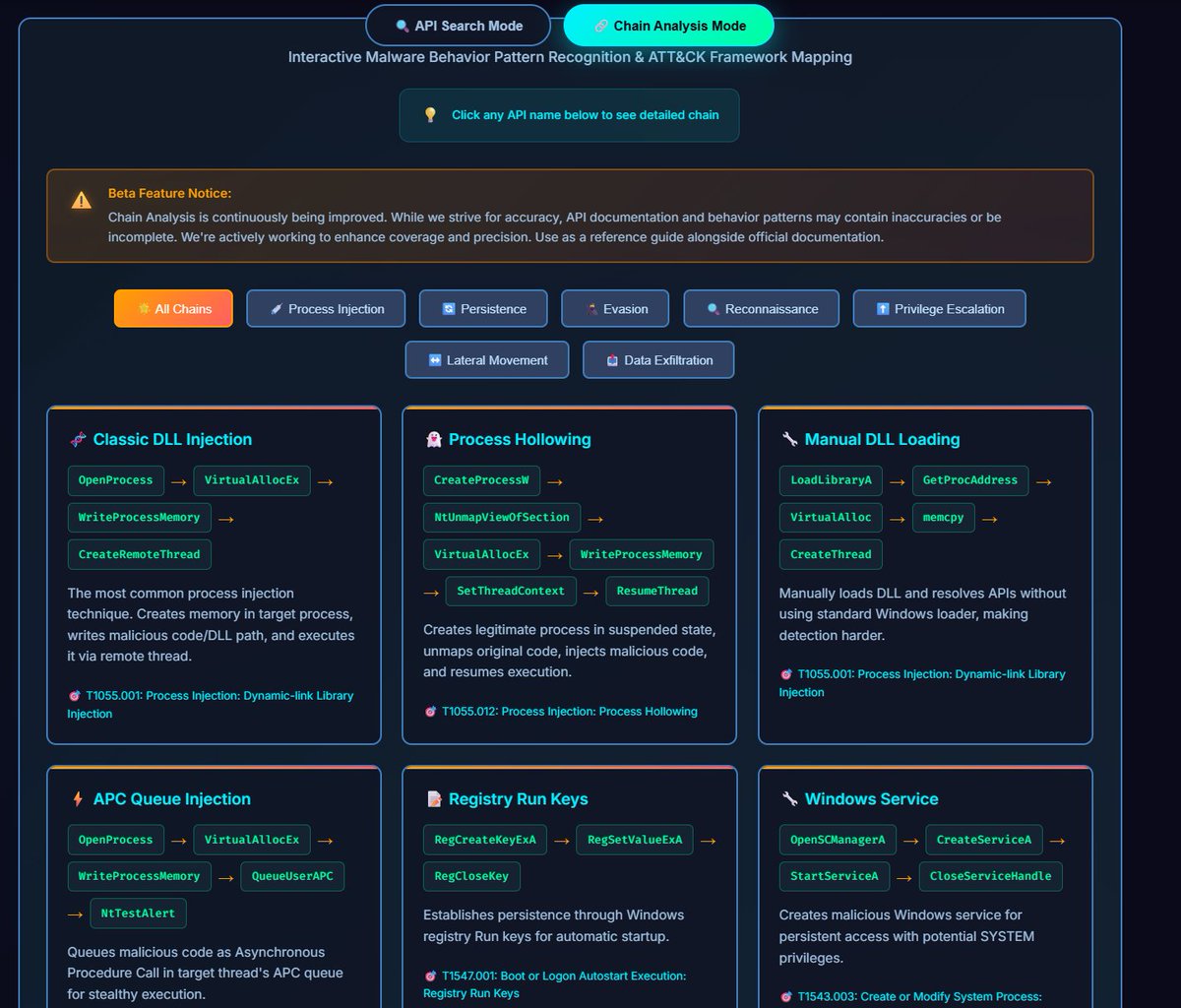
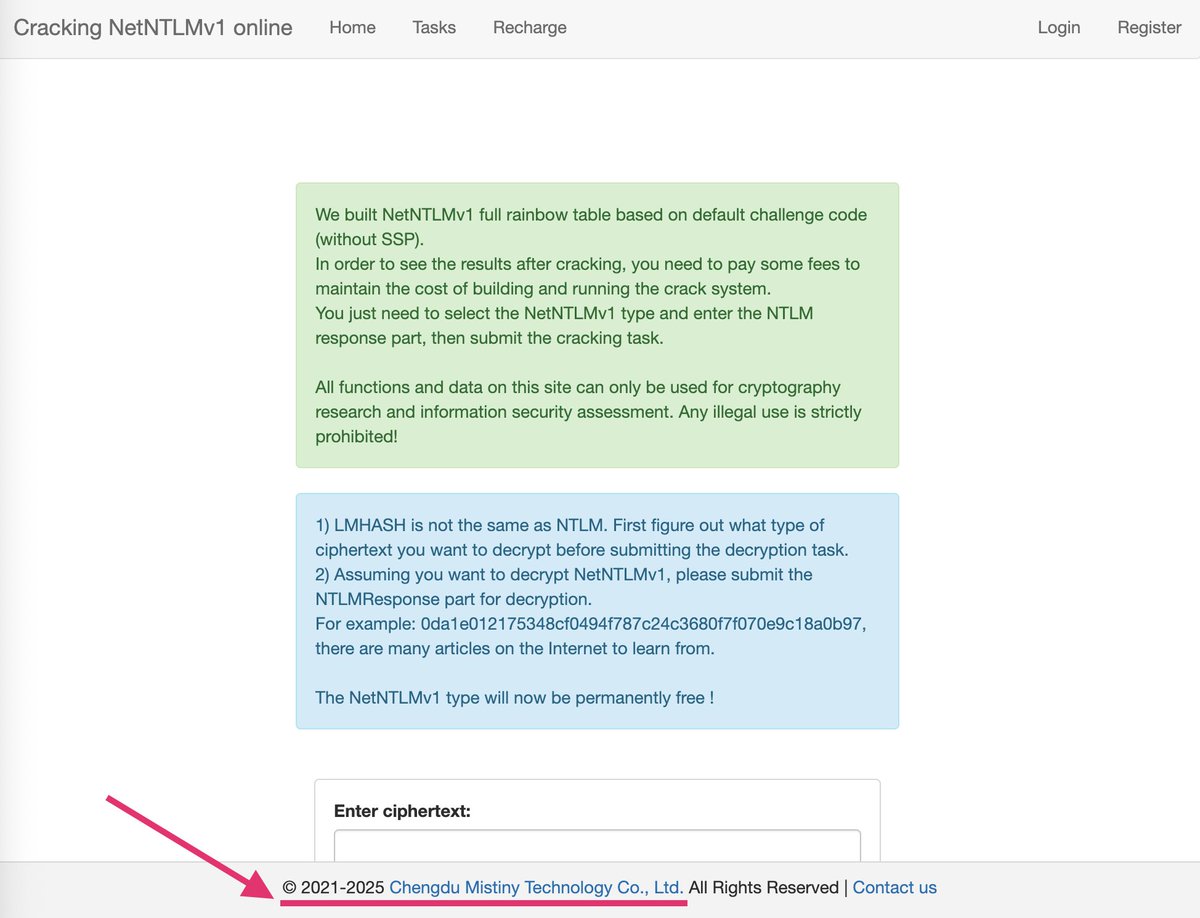
![🕳 (@sekurlsa_pw) on Twitter photo Google research created a dataset with rainbow tables for NetNTLMv1 with the 1122334455667788 challenge.
research.google/resources/data…
Dataset is available for download at:
▪️console.cloud.google.com/storage/browse… [Login required]
▪️gs://net-ntlmv1-tables Google research created a dataset with rainbow tables for NetNTLMv1 with the 1122334455667788 challenge.
research.google/resources/data…
Dataset is available for download at:
▪️console.cloud.google.com/storage/browse… [Login required]
▪️gs://net-ntlmv1-tables](https://pbs.twimg.com/media/G4B_bWxW4AAdjlR.png)