Virus Bulletin
@virusbtn
Security information portal, testing and certification body.
Organisers of the annual Virus Bulletin conference. @[email protected]
ID:118059149
https://www.virusbulletin.com/ 27-02-2010 13:27:37
25,1K Tweets
58,8K Followers
1,4K Following



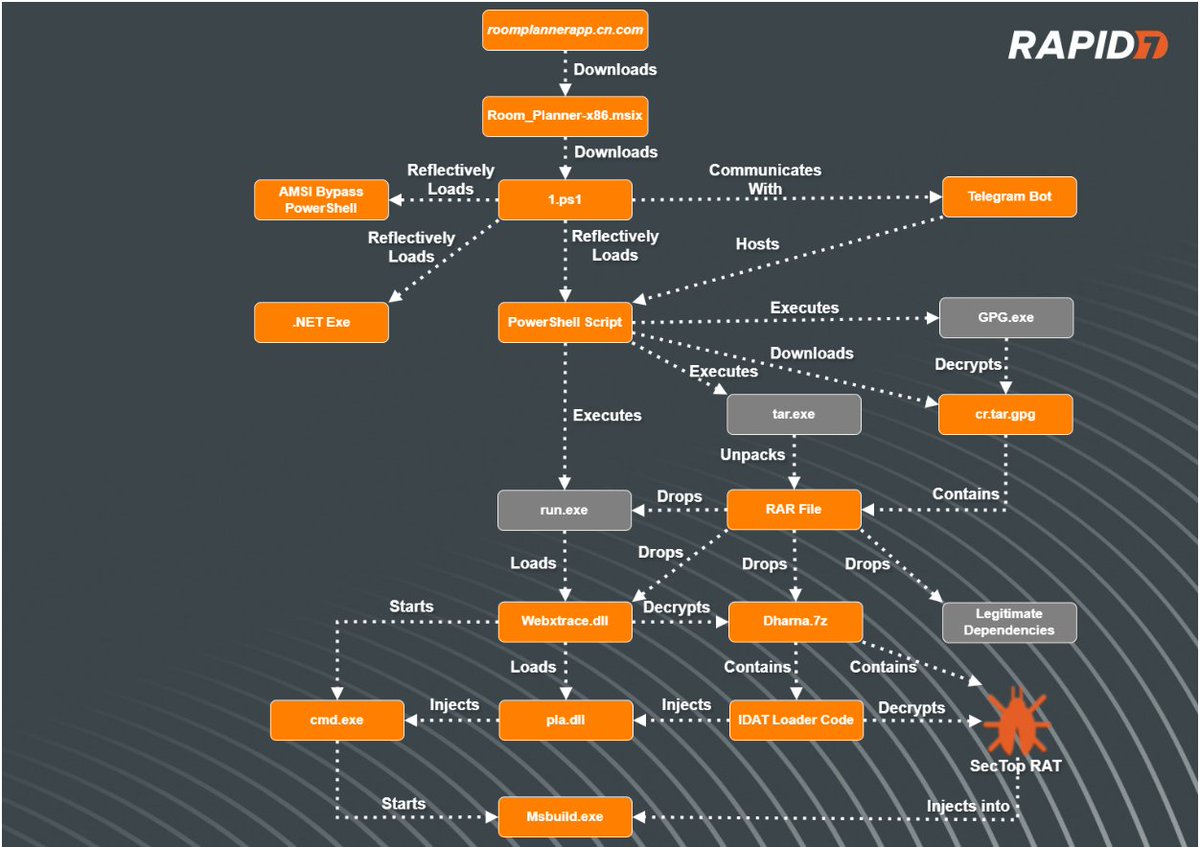
We observed cyber gangs impersonating LockBit and exploiting the group’s leaked Black builder. We also saw LockBit itself partially restore its infrastructure after Operation Cronos. Jambul Tologonov and John Fokker share the details. bit.ly/3Wd6fo7








.Cyber Threat Alliance is sponsoring 2024 Virus Bulletin Threat Intelligence Practitioners' Summit (TIPS) Track again. CFP is now open. The TIPS theme is 'Resilience Through Collaboration'
Submit abstract here: [email protected]
virusbulletin.com/conference/vb2…
#cybersecurity #VB2024








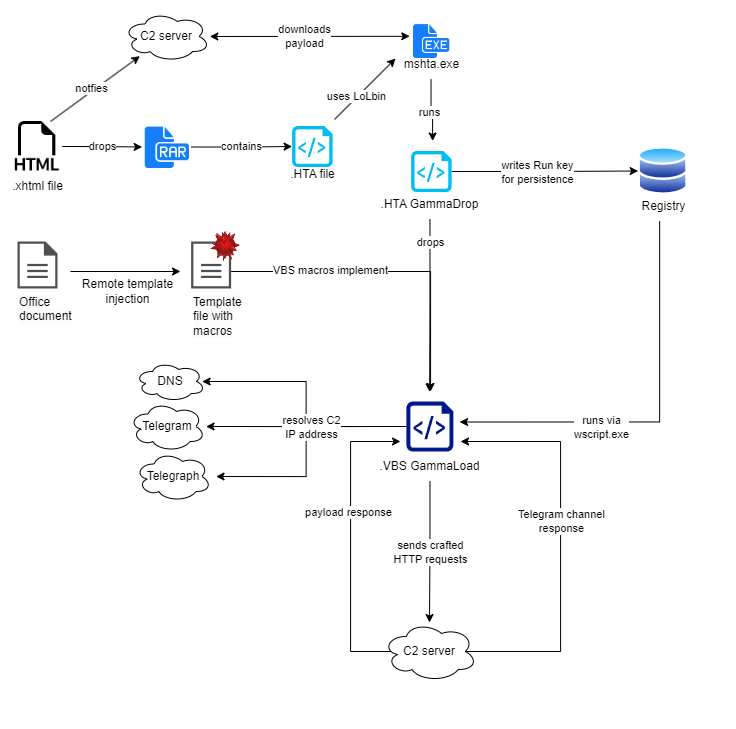
Raspberry Robin malware innovates once again using a 'new' trick to evade Windows Defender antivirus by importing specific functions to check whether its running in the Windows Defender emulator.
Find out more w/ this post by Alice Climent-Pommeret harfanglab.io/en/insidethela…
#Cybersecurity