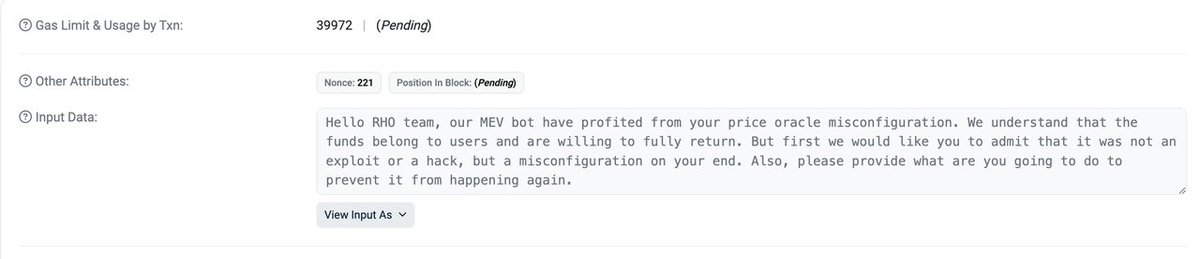
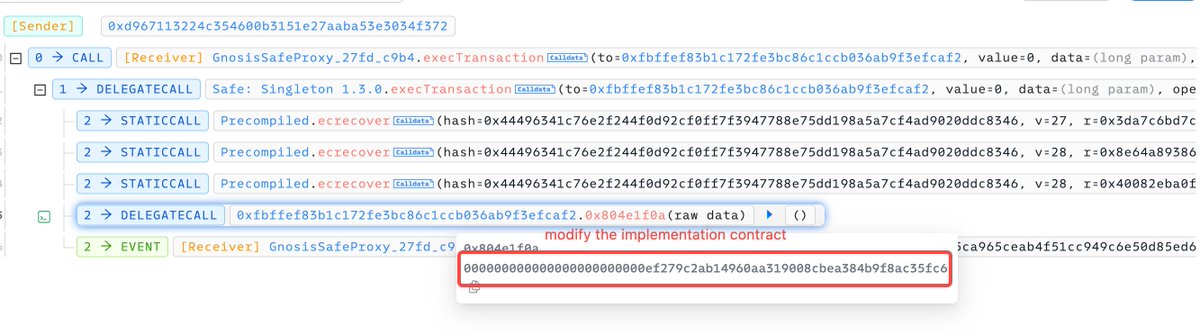
⚠️ #OKLinkSecurity The WazirX: India Ka Bitcoin Exchange experienced a significant security breach, resulting in a loss of ~$235M. The attack was made possible due to the compromise of their GnosisSafe multi-sig wallet on the #ETH. The attacker hijacked the implementation contract of the



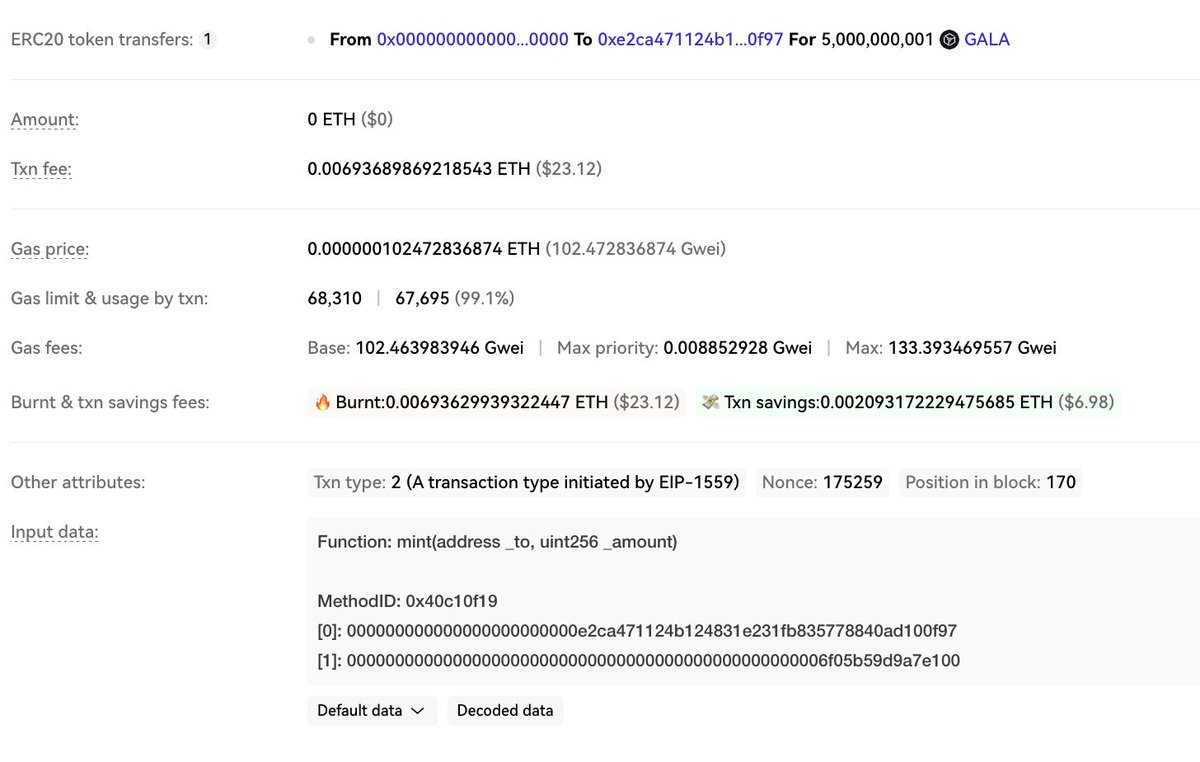
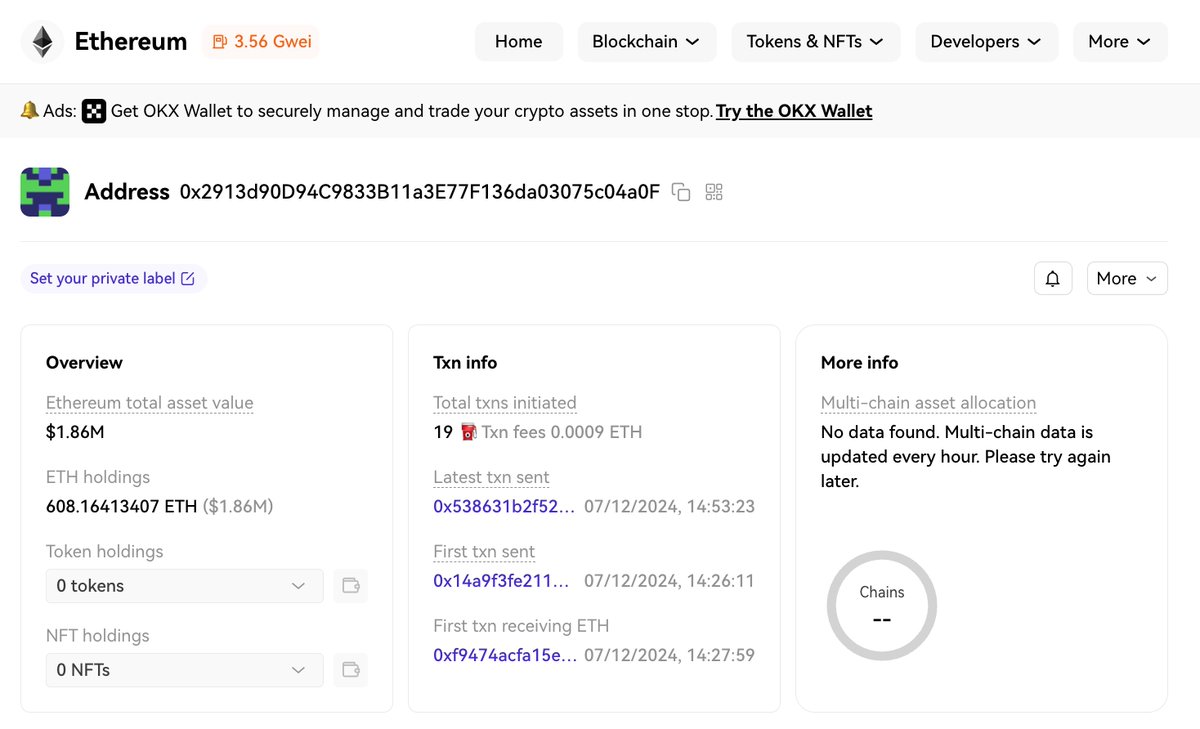
⚠️The Dough Finance experienced a significant security breach on #Ethereum, and the resulting loss exceeded $1.8M. As of now, all the stolen assets have been deposited into address 0x2913d90D94C9833B11a3E77F136da03075c04a0F. Relevant tx: oklink.com/eth/tx/0x92cdc… #OKLinkSecurity



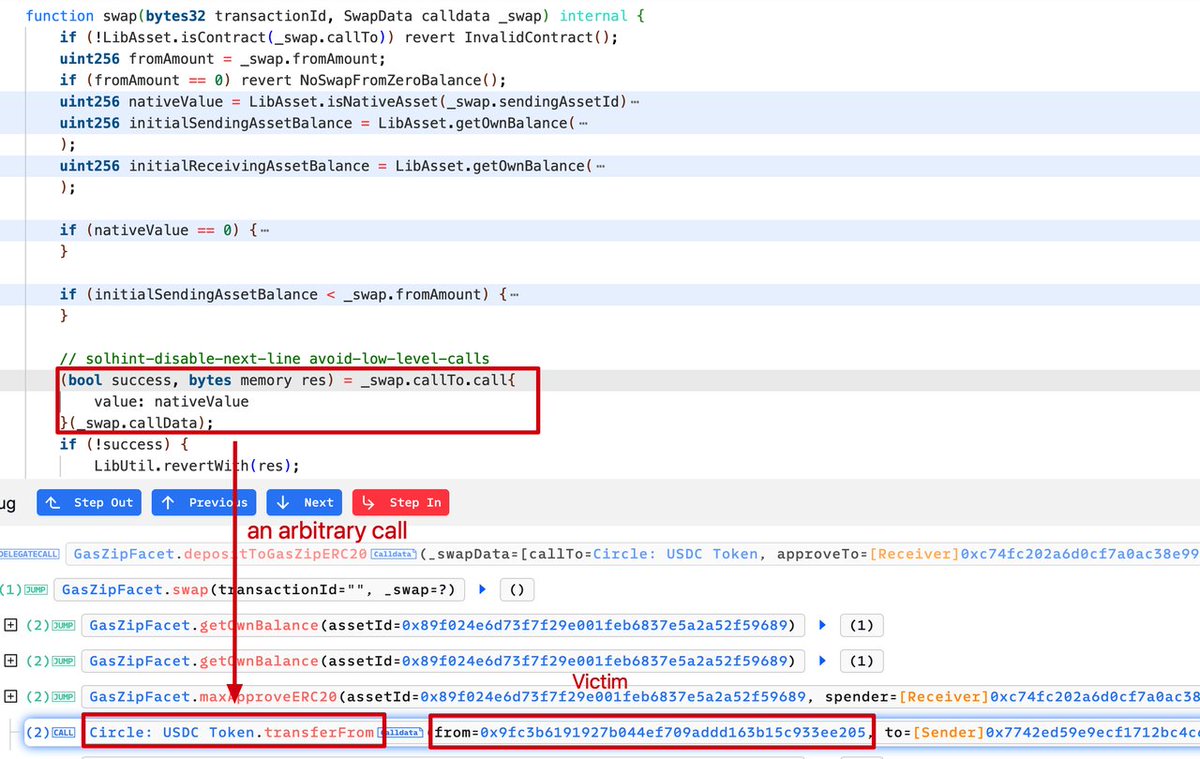
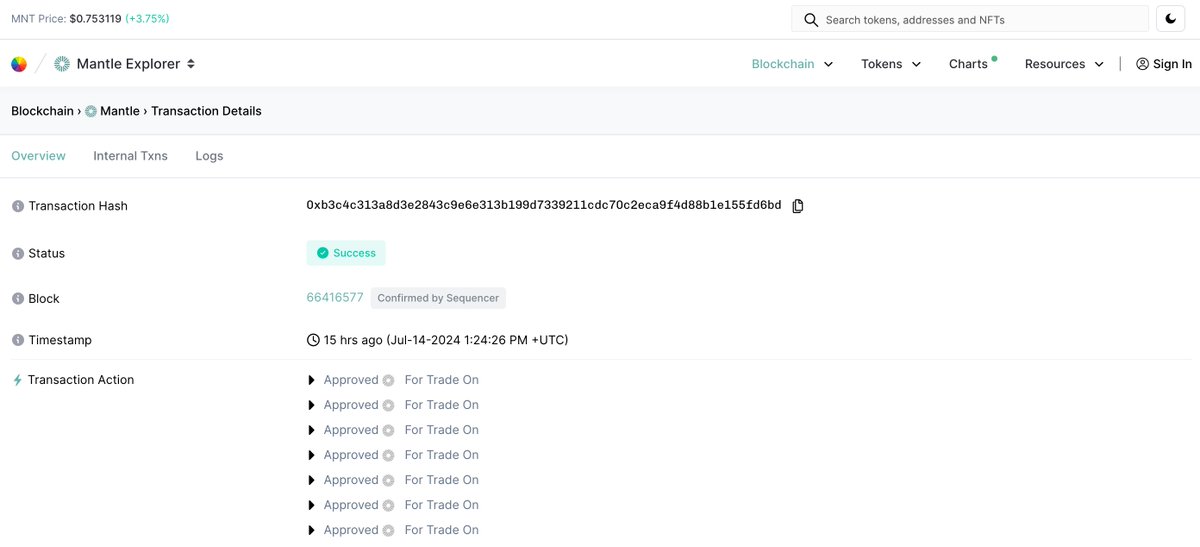
#OKLinkSecurity The Velocore | veDEX on zkSync Era / Linea ▪️ experienced a significant security breach on Linea and zkSync resulting in more than $10M in losses. The hacker has deposited all ~1,807 ETH of illicit gains into Tornado. One of the attack txns: oklink.com/linea/tx/0xe4f…