🆕Today we present you #Cybertrust365 Managed Security Service Provider. Our new #BusinessUnit dedicated to Managed Cybersecurity Services.💥
Secure your business, click here to learn more➡️ cybertrust365.com/en/
#cybersecurity #SGBox #ITSecurity #MSSP




Scammers love to send emails and try to make them look like they’re from legitimate sources.
If you’re not 100% confident that you or your team know what to keep an eye out for, then we’re always happy to help.
#CyberSecurity #Phishing #ITSecurity #Cybercrime



.Apple patched zero-click vulnerabilities in its operating system software underpinning its iPhones, iPads, watches and macOS computers. #cybersecurity #infosec #ITsecurity bit.ly/444LH1E

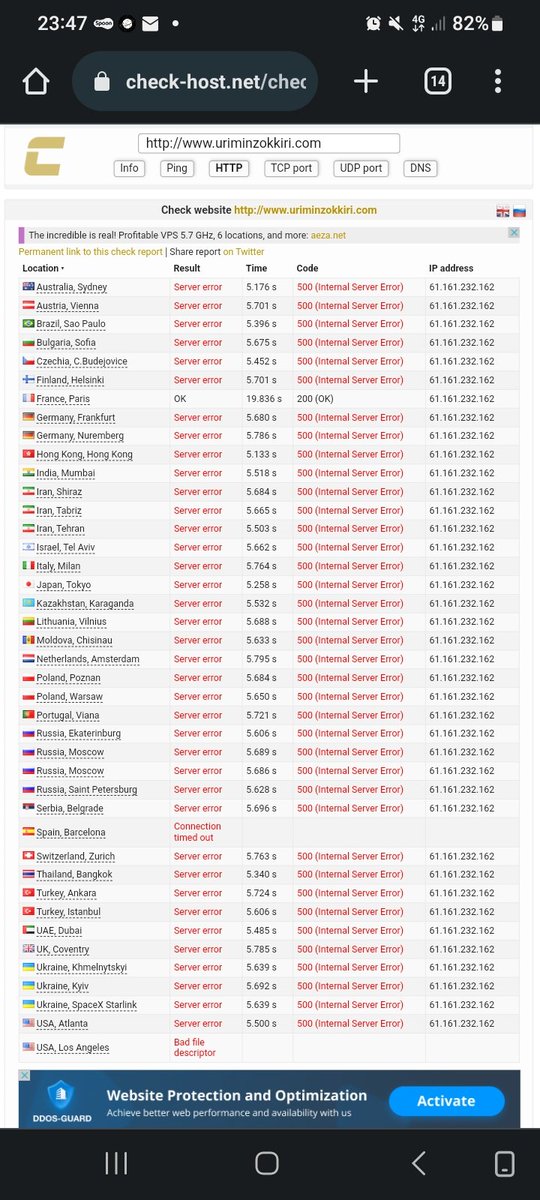
The local government of #krolwiec is going to be crushed
We are #anonymous
We are legion
We don't forgive
We don't forget
Expect us
#putler
#OpRussia
#ITSec urity
#ITSec
#CyberSecurity
#AnonOps
#DDoS
#Kakhovka
#ITArmyOfUkraine
#SaveUkraine
#SlavaUkraini
#義勇兵

IRONSCALES Brings Generative AI to Email Security #CyberSecurity #cyberthreats #hackers #darkweb #databreaches #cybercrime #cybersec #ThreatIntel #itsec urity #cyberintelligence #infosec #itsec #cyberattacks securityboulevard.com/2023/06/ironsc…

FBI seizes BreachForums after arresting its owner Pompompurin in March #CyberSecurity #cyberthreats #hackers #darkweb #databreaches #cybercrime #cybersec #ThreatIntel #itsec urity #cyberintelligence #infosec #itsec #cyberattacks bleepingcomputer.com/news/security/…

Push-bombing is a way that hackers try to circumvent multi-factor authentication. Learn what it is and how to prevent it.
#PushBombing #Cybersecurity #ITSecurity #MFA #2FA

IT Security News
Interesting reference material for a cybersecurity toolset and framework.
Stay Vigilant, Stay Secure!
ncsc.gov.uk/blog-post/new-…
#ITSecurity #Cybersecurity #Infosec #Appsec

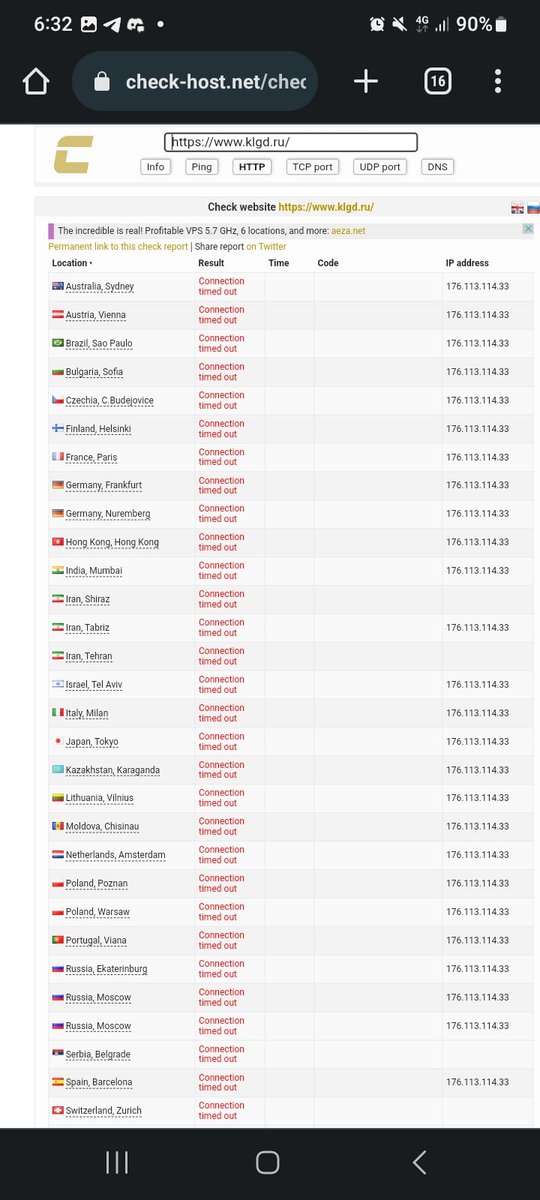
The Russian nuclear company is crushed in a few seconds.
We are #anonymous
We are legion
We don't forgive
We don't forget
Expect us
#putler
#OpRussia
#ITSec urity
#ITSec
#CyberSecurity
#AnonOps
#DDoS
#Kakhovka
#ITArmyOfUkraine
#SaveUkraine
#SlavaUkraini
#義勇兵


Multi-layered email security is critical for your business!
Check out this infographic to find out the top business ransomware defense strategies😀👇
#ransomware #cybersecurityawareness #infosec #emailsecurity #itsecurity #infographic


alen velagić Wenn wir ganz von vorn anfangen: wer postet Screens von seinem Online-Banking? Da läuten doch sofort die Fake-Alarm-Glocken. Also nornalerweise.


Redefine your security posture, safeguard your critical business systems, information, and keep your employees’ awareness high regarding phishing & social engineering with our robust cybersecurity services.
#cyber security #leelajaytechnologies #cyber attack #ITSecurity #cyber




5 Tips for Modernizing Your #Security Operations Center Strategy - buff.ly/3WYsI6q #SOC #cybersecurity #infosec #IT security #OT #IT #vulnerabilities