

ICI Bucharest participated, between April 23-24, 2024, in the conference 'Ideas that change Romania', an event organized by the Commission for European Affairs of the Chamber of Deputies: ici.ro/en/events/ici-…
#cybersecurity #cyberthreats #research #collaboration


Trust Wallet a well-known crypto wallet site has faced a #DDoS attack by a Bangladeshi Hacktivist Group.
#TrustWallet #cti #Cyberthreats #crypto


SMBs are prime targets for #CyberThreats . Our blog addresses these challenges, emphasizing #CyberSecurity 's importance and providing insights into common threats. We simplify selecting cybersecurity solutions, ensuring effective defense.
Read more: bit.ly/3Rq6ckt


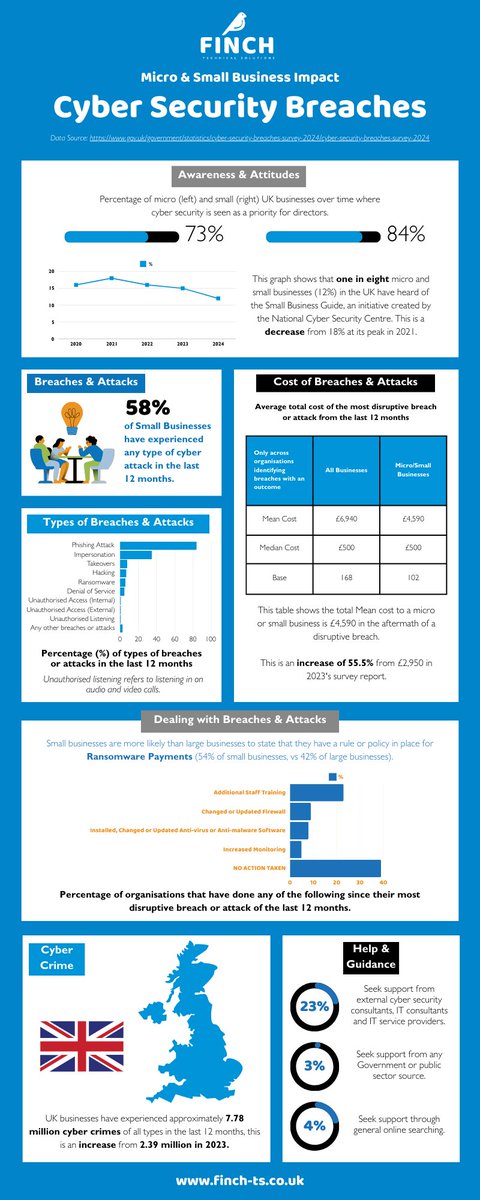
Shocking Insights Unveiled: Cyber Security Breaches Survey 2024 Reveals Impact on UK Small and Micro Businesses 🚨
Read more in our infographic below 👇
#CyberCrime #CyberSecurity #CyberRisk #CyberThreats #CostOfCyberAttack

Top 6 #fintech facts about the influence of fintech on the #banking and #finance sector: buff.ly/33PLFM4
#cybersecurity #AI #ArtificialIntelligence #DigitalSkills #DigitalTransformation #cyberthreats #startups



Happy to announce our partnership with Versasec, a global leader in identity and access #managementsolutions ! Together we're empowering organizations to fortify their defenses against evolving #cyberthreats with a customer centric approach and ease of management.


86% of #Cyberthreats are concealed in encrypted traffic—and there’s been a 185% surge in encrypted attacks on #Government . Learn how #ZeroTrust architecture can reduce your reliance on legacy technology and strengthen your #Security . FedTech Magazine dy.si/32nK7S2


From #databreaches to ransomware attacks, #cybercrime knows no bounds. Discover how #internalauditors navigate the intricacies of #cyberthreats with their expertise and ensure the resilience of #enterprises . Read more: bit.ly/3WegYhU
#aurex #digitalthreat #security #blog


Revolutionise your organisation's cybersecurity with Microsolve's #CyberRiskReview . Book now to stay ahead of cyber threats: eu1.hubs.ly/H08MzBb0
#CyberSecurity #Microsolve #CyberThreats



The New Frontiers Of Cyber #Fraud >> Adapting To The Age Of #AI And #Deepfakes
buff.ly/3Ud5acX
Forbes @DataSoftGroup #business #leadership #regtech #fintech #tech #regulation #compliance #CISO #CIO #CTO #CEO #data #genAI #generativeAI #cybercrime #cyberthreats


This week saw a surge in Ransomware attacks, with 57 companies targeted across the United States, the United Kingdom, France, Brazil, and Italy.
↘️
Follow us for weekly updates on #Ransomware attacks and daily updates on #cyberthreats .


Check out the Top 5 Most Active Threat Actors in Q1 2024 Identified by Threatlynx's Cyber Threat Intelligence Tool!
#cti #cyberthreats #threatactor


Join our webinar ‘How to transition to ISO 27001:2022 and maintain certification’
🗓️ Tuesday, 7 May 2024 @ 3pm GMT
👉 Sign up: ow.ly/9Y6a50R9nZS
#ISO27001 #cybersecurity #webinar #informationsecurity #cyberthreats


🌐 Embrace the #DigitalForensics revolution with Kali Linux 2024.1. Your ally in unmasking #CyberThreats and securing networks. #CyberDefense bit.ly/kali20241

#CyberThreats are surging with the digitization of connected cars. Our research emphasizes the importance of managing operational technology (OT) security.
Discover proactive strategies for manufacturers to mitigate these risks. Click here to read more: bit.ly/41M7HhY


Beware Shadow IT in your network—unauthorized software risks data security. From third-party apps to unsanctioned downloads, it bypasses security, leaving your network exposed. #ShadowIT #DataSecurity #CyberThreats #RiskAwareness


The new Kristel branding is unveiled!
#KristelCommunication #Cybersecurity #CyberThreats #Rebrand #Nairobi #Kenya #Africa
Kristel



