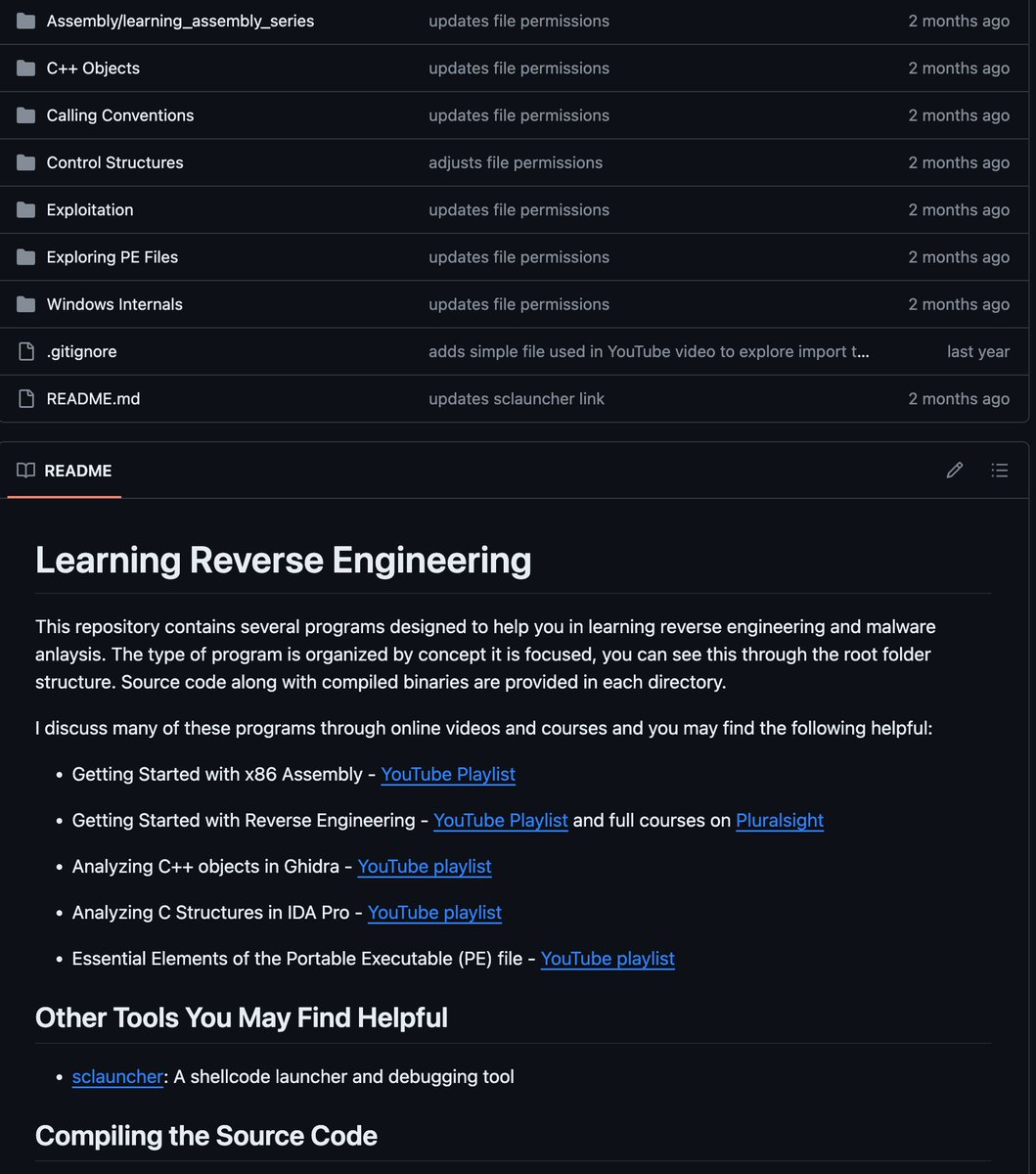
Josh Stroschein | The Cyber Yeti
@jstrosch
Reverse engineer at FLARE/@Google | @pluralsight author | 700K+ views on YT 😱 Find FREE resources below👇
ID:53809084
https://thecyberyeti.com 05-07-2009 01:40:42
3,9K Tweets
8,3K Followers
998 Following





🚨 icymi - you can catch the replay of the first #MalwareMondays ! This series will help build core #malware #analysis and #reverse #engineering skills! Episode 0x01 looks at analyzing #procmon data 👇
youtube.com/live/b5_PUMmpw…
Artifacts at:
thecyberyeti.com/malware-mondays




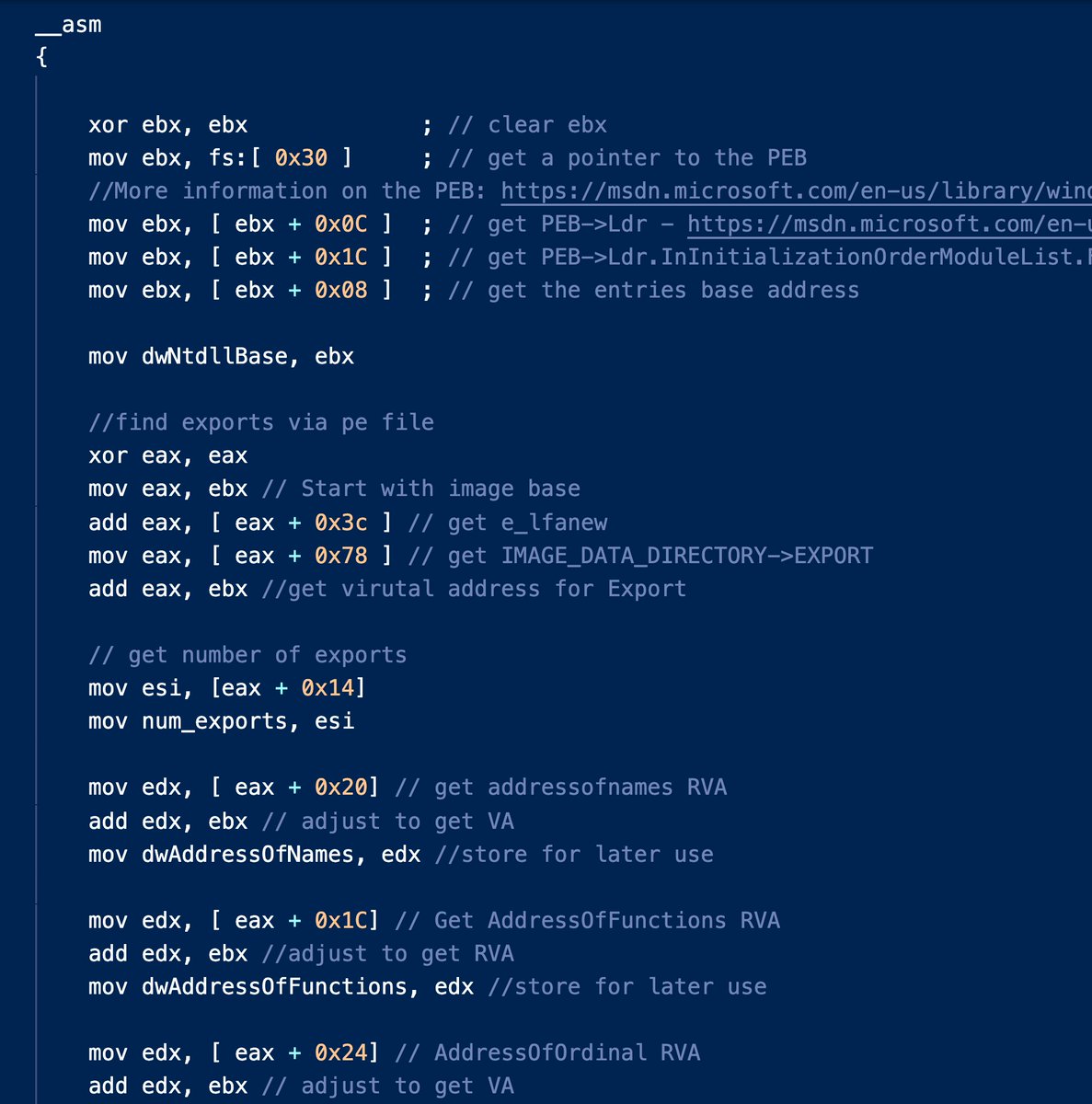
Reverse engineering binary code is a core skill for software security, malware analysts and penetration testers. Check out my course on Pluralsight, we'll study everything from assembly basics (intel x86) to working with debuggers and disassemblers!
👉 pluralsight.com/courses/revers…