MSec Operations
@msecops
ID: 1817972951314202624
http://www.msecops.de 29-07-2024 17:19:09
15 Tweet
957 Followers
1 Following

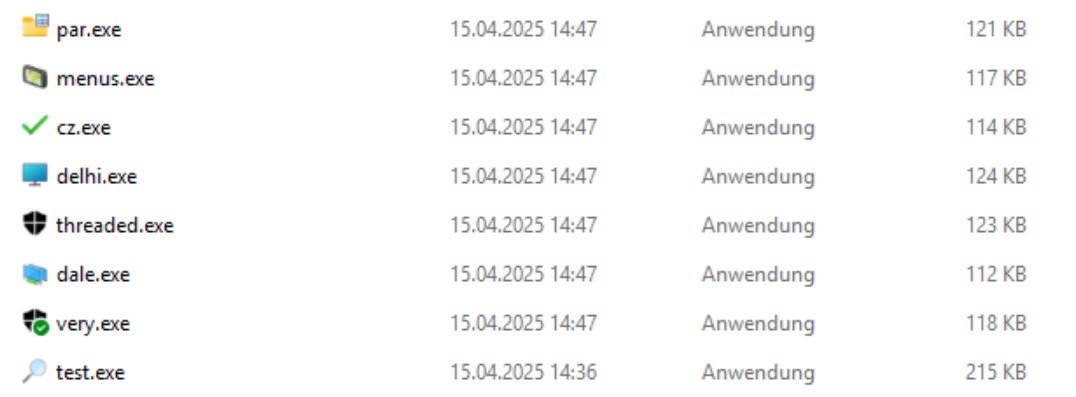
Definitely recommend this! I used the NimSyscallPackerand by S3cur3Th1sSh1t and it was a game-changer. Imagine what the Rust one can do! Let’s back the underdogs instead of those big bucks tools! 👇 x.com/MSecOps/status…