Invoke RE
@invokereversing
Malware analysis can be hard, but learning it shouldn't be.
ID: 1482714674516930565
https://training.invokere.com 16-01-2022 14:02:15
182 Tweet
1,1K Followers
87 Following

In case you missed it, check out the “Supper is served” technical blog by Tony/Humpty on the Supper backdoor c-b.io/2025-06-29+-+S… it’s well written and provides a great overview of its functionality!




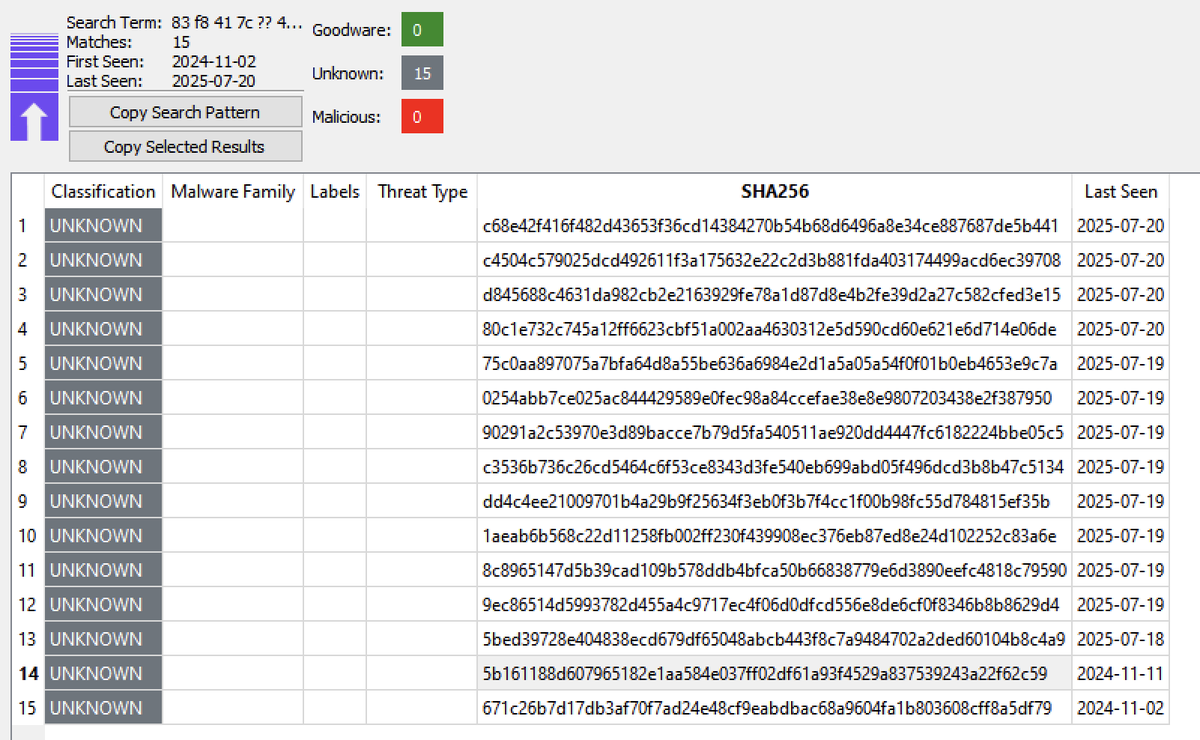
Cedric Brisson (Tony/Humpty), in collaboration with Invoke RE's Josh Reynolds (Josh Reynolds (jmag)), analysed the "Scavenger" malware distributed via a supply chain compromise involving popular NPM package es-lint-config-prettier. c-b.io/2025-07-20+-+I…






🛑 Heads-up: #num2words v0.5.15 (just dropped on PyPI) may be #compromised. Early signs probably link it to #Scavenger, the same threat actor behind previous software supply chain intrusions. Malware Utkonos Tony/Humpty Invoke RE