Josh Stroschein | The Cyber Yeti
@jstrosch
Reverse engineer at FLARE/@Google | @pluralsight author | 700K+ views on YT 😱 Find FREE resources below👇
ID:53809084
https://thecyberyeti.com 05-07-2009 01:40:42
3,9K تغريدات
8,5K متابعون
1,0K التالية


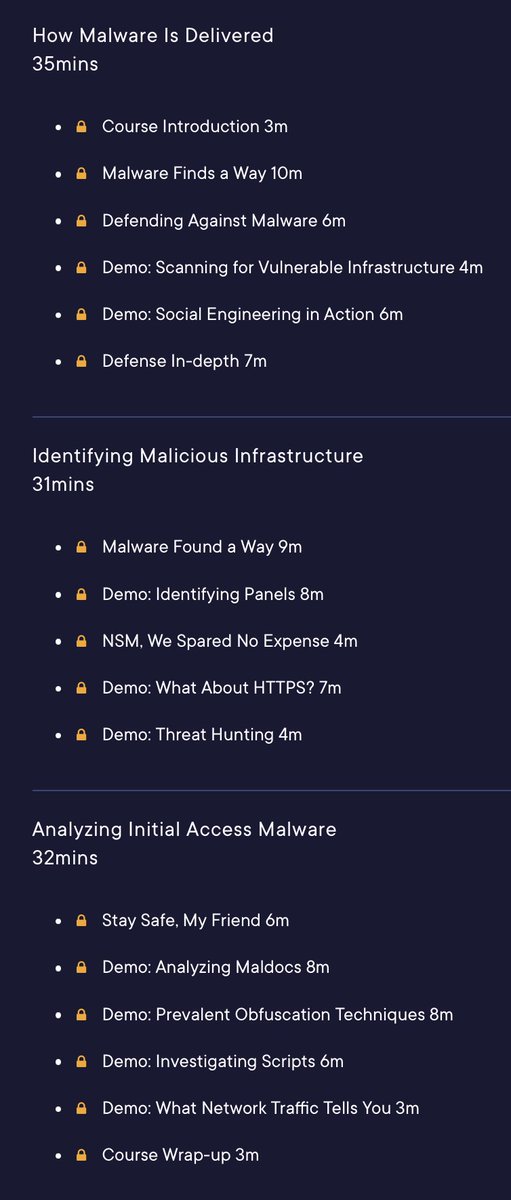
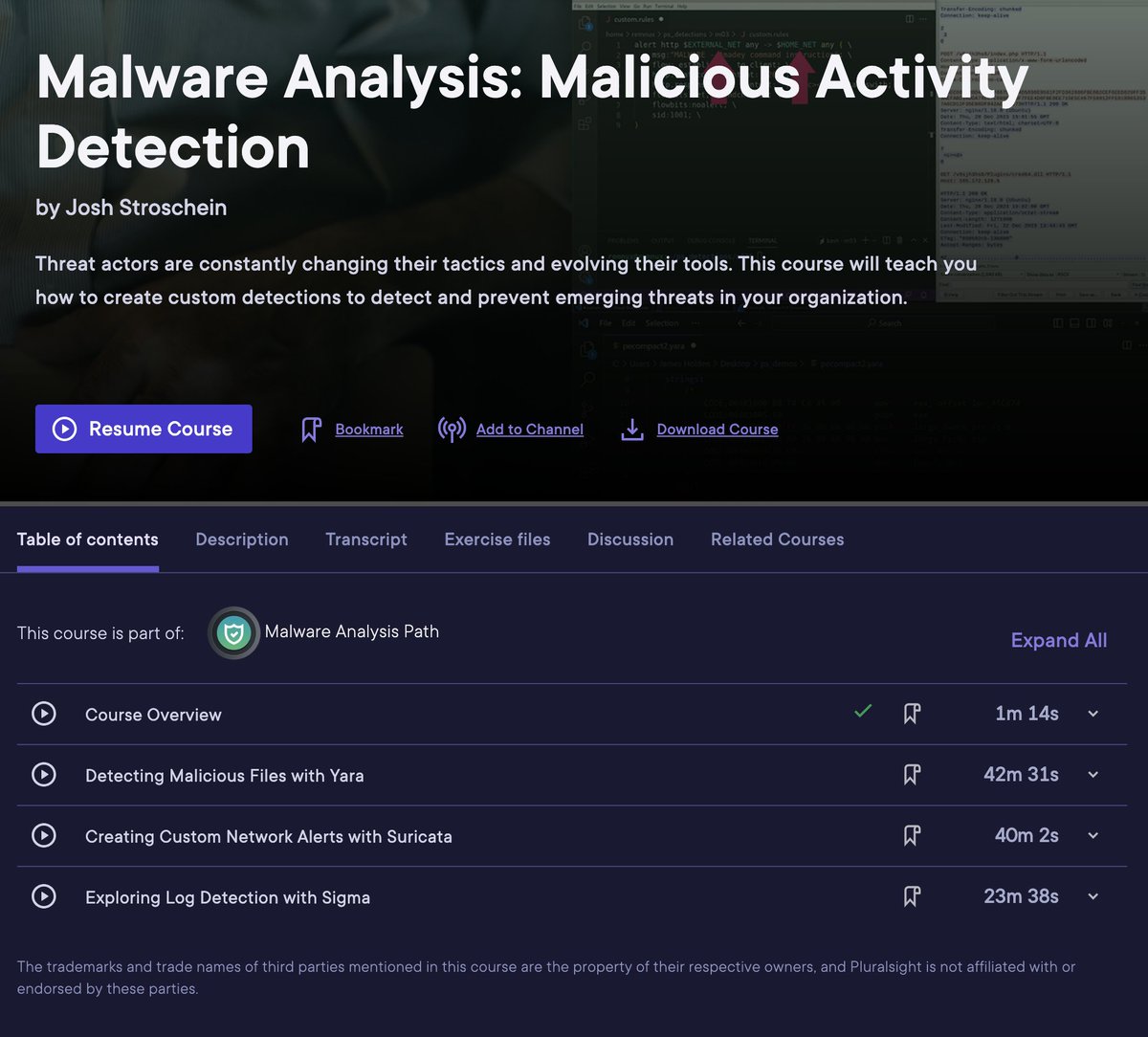
My latest Pluralsight course live! This course will introduce you to three key detection technologies - #suricata , #yara and #sigma 👇
✅ pluralsight.com/courses/malwar…
This continues the malware skill path, where you can learn triage and reversing skills
app.pluralsight.com/paths/skills/m…







Have interesting insights on Suricata? Share them at #SuriCon2024 ! Join industry, open-source, academia, and research professionals passionate about #Suricata and network threat hunting, apply today to talk at #SuriCon2024 . 📣 #CallforTalks
suricon.net/call-for-talks/


Calling all EU Threat Researchers 👀
Proofpoint's Threat Research team is hiring for a Senior APT Researcher based in the EU. 🚀 🇪🇺
Bonus points: I'll talk to you about Rust 🦀 whenever you want (and probably when you don't!).
proofpoint.wd5.myworkdayjobs.com/en-US/Proofpoi…





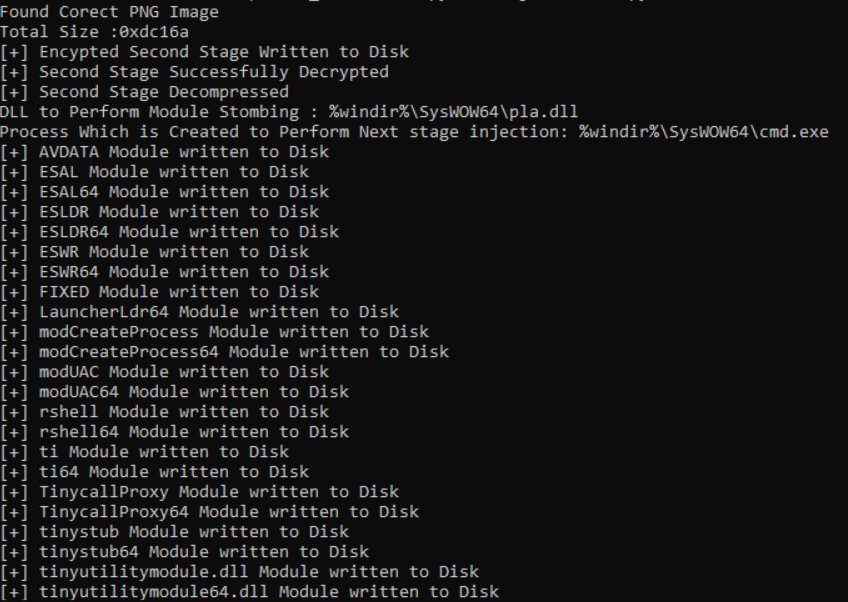
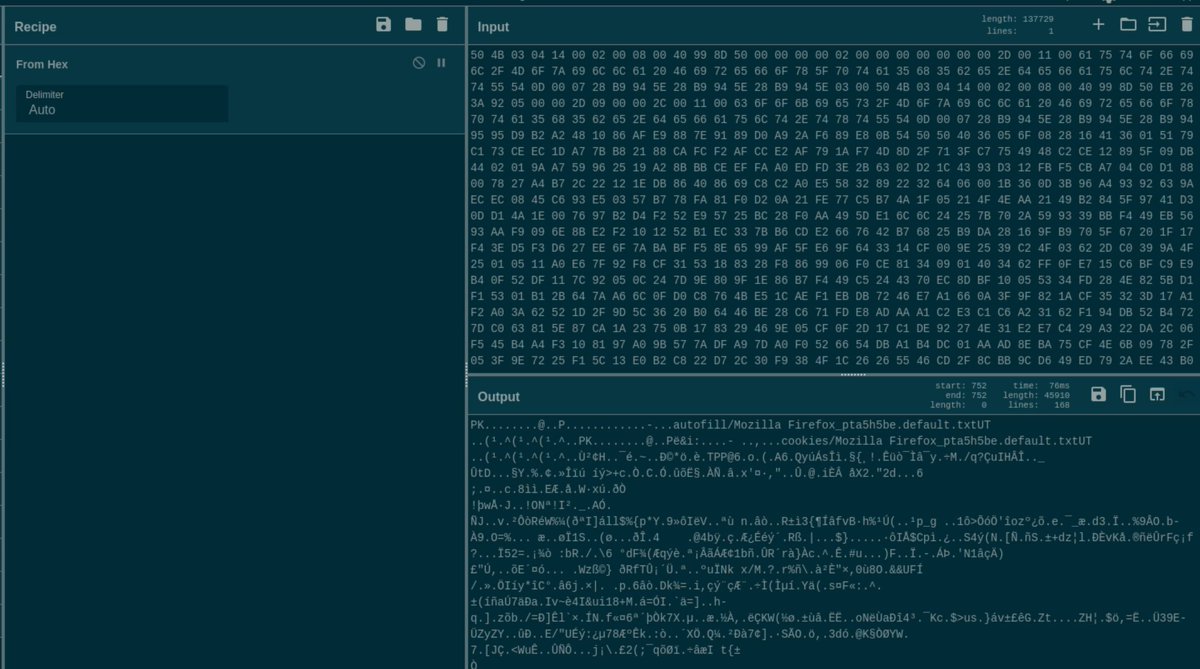
I wrote a blog about #HijackLoader . It Discussed about the new modules added, changes observed, current malware delivery, second stage loading process and a script to extract all the modules used . Please share your feedback