Gal Shpantzer
@Shpantzer
Information security and data engineering advisor. Virtual CISO with interdisciplinary skillset to solve complex business and technical problems. Not CISSP/10X
ID:21650546
23-02-2009 13:02:10
55,5K Tweets
11,1K Followers
4,9K Following











So stoked for my event with Hoff (Christofer Hoff/LastPass)
on 3/13 at 11 AM ET🤖🤘
We'll talk through the latest social engineering threats, hacks I've done recently and how they succeeded OR how I got caught, and how AI has changed the way we hack in 2024.
info.lastpass.com/Expert-Strateg…







Dave Aitel PDD Holdings denies a lot of this but researchers from Lookout further analyzed app samples and corroborated the original researchers claims.
'There is also some code that looks like it would be consistent with preventing apps from being uninstalled.'


Dave Aitel It seems the 0days were being used to steal more user data than native Android APIs would give an app access to.
They even used this elevated access to uninstall their competitors apps off the phone.
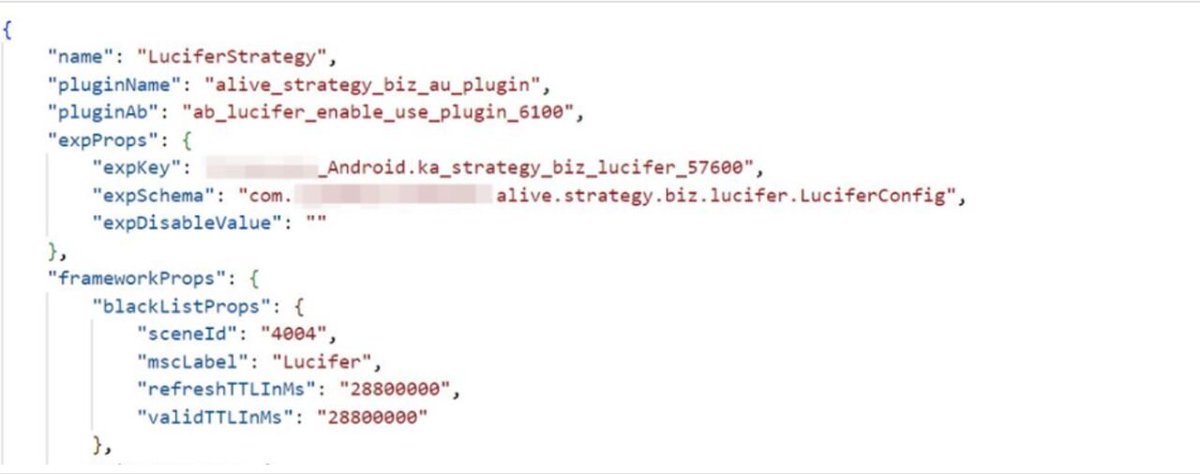

Dave Aitel Pinduoduo is an e-commerce app with 751.3 million average monthly active users.
In March 2023 it was reported that their official signed Android app contained malware and a number of Android 0days