Yakir Kadkoda
@yakirkad
🧩 Director of Security Research at @AquaSecTeam | Black Hat & DEFCON & RSA Speaker
ID: 1469759292798603266
11-12-2021 20:01:47
143 Tweet
234 Takipçi
537 Takip Edilen

📚 tl;dr sec 244 ☁️ Cloud Security Slides Nick Frichette, Seth Art, Jenko Hwong ✍️ Threat Modeling 💼 Security Program Templates Robert A. 🧑💼 Security Training Tips Phil Venables 🦈 TrailShark Yakir Kadkoda, Ofek itach tldrsec.com/p/tldr-sec-244

🦈 TrailShark: Understanding AWS API and Service Interactions A plugin that connects Wireshark with AWS CloudTrail, offering near-real-time analysis of AWS API calls → Capture and examine the internal API calls triggered by AWS services → Used by Aqua Security's Ofek itach &



Great research from Yakir Kadkoda and Ofek itach! It’s another example of AWS client tools exposing customers to attacks. You have to be careful of global namespaces like S3 😬



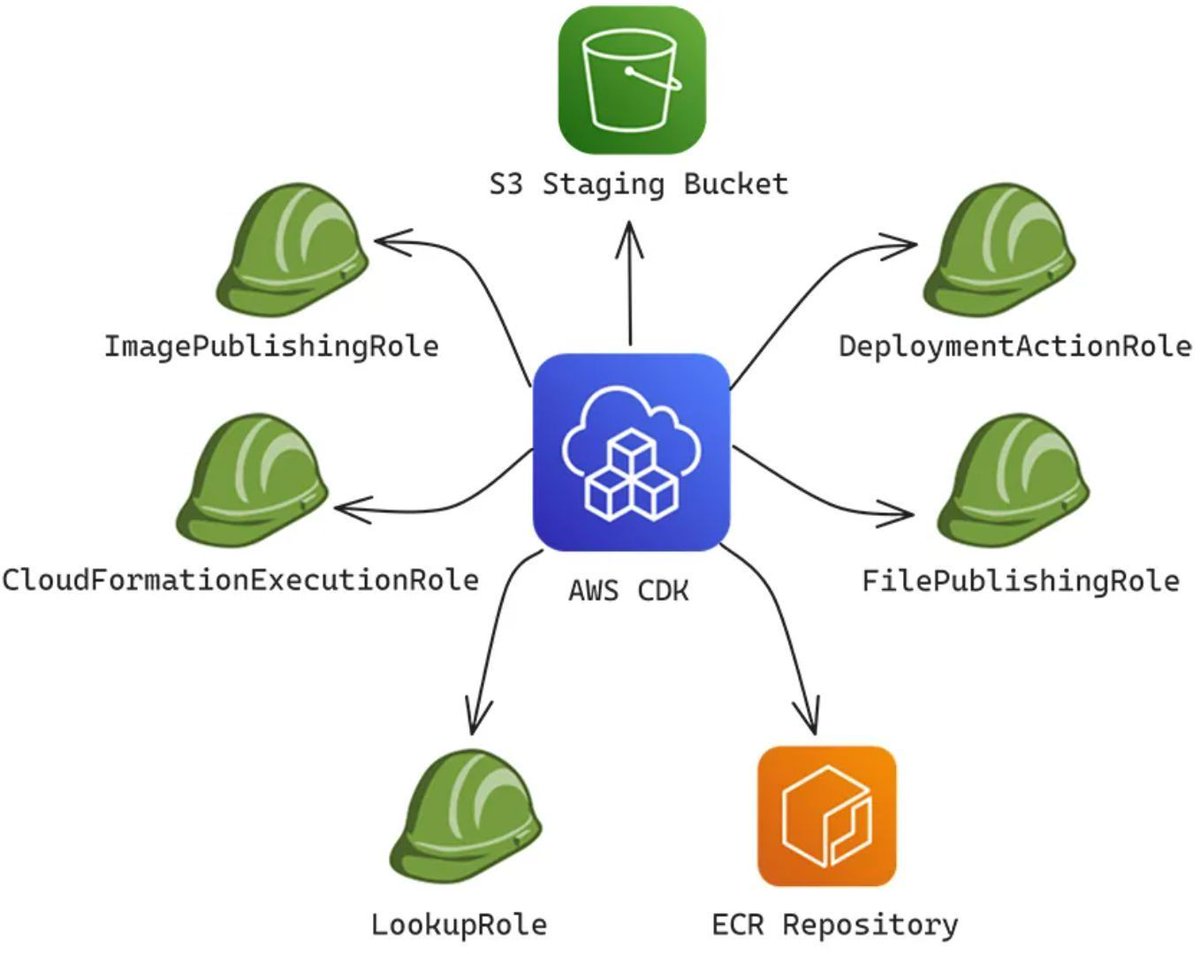
🛎️ AWS Security Digest 181 is out! 1️⃣ AWS CDK Risk: Exploiting a Missing S3 Bucket Allowed Account Takeover by Ofek itach & Yakir Kadkoda 2️⃣ Protecting Data and Preventing Ransomware: The IAM Guide to Managing and Updating Encryption for AWS Resources by Jason Kao 3️⃣ What I’ve

Believe it or not, #CVE-2024-47574 started with me not wanting to be a lousy friend. Eviatar Gerzi launched #PipeViewer, and I thought, “Am I a terrible friend if I don’t try it?” So I did—and one “that’s weird” moment later, here we are! pentera.io/blog/piping-ho…


AWS: where the shadow knows your secrets. Yakir Kadkoda & Ofek itach show you how attackers find your forgotten resources. #INTENT2024 ☁️🔓


Heading to Black Hat Europe 2024 in London this week? Don’t miss the Aqua Security Research Team - Team Nautilus at our Arsenal Talks, where we’ll showcase tools and techniques to uncover hidden vulnerabilities, trace system events, and analyze AWS API calls and service








🎉 Excited to welcome Yakir Kadkoda to Cloud Village @DEFCON 33! 🎤 He’s presenting “The Hidden Path to Root: Shadow Resources, Roles & AWS Service Exploits” ☁️🔐 📍 Room 311, LVCC 🗓️ Aug 8 | 🕥 10:50–11:30 AM PT 🔗 cloud-village.org/dc33 #DEFCON33 #HackerSummerCamp