Clint Gibler
@clintgibler
🗡️ Head of Security Research @semgrep
📚 Creator of https://t.co/xwtIAI0CuJ newsletter
ID:720576770
https://tldrsec.com/subscribe 27-07-2012 17:49:39
8,3K Tweets
19,1K Followers
575 Following
Follow People



🛡️ Securing millions of developers through 2FA
Mike Hanley on rolling out 2FA to @GitHub users
* 95% 2FA opt-in rate
* 54% increase in adoption among all active contributors
* Automation reduced support burden
See also our chat here: youtube.com/watch?v=s95Puo…
github.blog/2024-04-24-sec…


😱 An Obscure Actions Workflow Vulnerability in Google’s Flank
Adnan Khan's write-up on finding a vuln in a Google repo that's existed for 3 years
Enjoyed the vuln hunting at scale and making make the exploit/exfiltration stealthy
adnanthekhan.co/2024/04/15/an-…

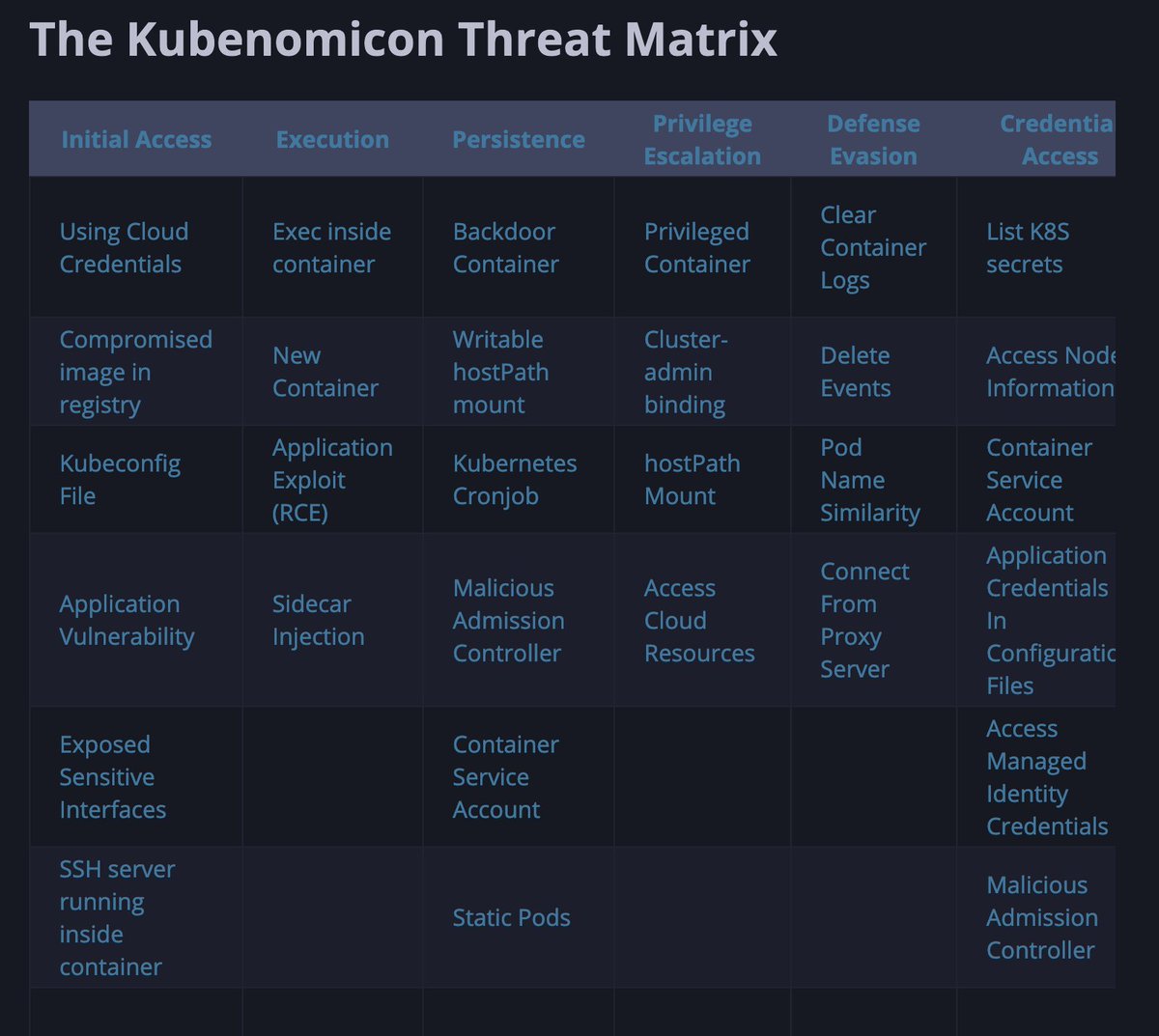
🔮 The Kubenomicon
A massive list of offensive Kubernetes security techniques and how to defend against them
Includes detailed tactical exploitation (and defense) tips
#cybersecurity
kubenomicon.com


💰 Security, Funded #140 from Return on Security is out, together with Subsalt!
returnonsecurity.com/p/security-fun…




🐳 Abusing search permissions on Docker directories for privilege escalation
How having the search bit set for “other” on /var/lib/docker and child dirs can allow a low privileged user to access other containers & escalate privileges
By WithSecure™
labs.withsecure.com/publications/a…


🪣 S3 Bucket Encryption Doesn't Work The Way You Think It Works
Daniel Grzelak on how S3 decryption works more like access control than decryption
“S3 encryption can prevent data exfiltration but is irrelevant after exfiltration.”
blog.plerion.com/s3-bucket-encr…


☁️ Matt Slack's Journey Migrating to AWS IMDSv2
With 60,000 EC2 instances across 17 AWS regions, while operating hundreds of AWS accounts
* Determine instances currently using IMDSv1
* Migrate scripts, update Terraform templates
* SCPs
* Alert on IMDSv1 use
slack.engineering/our-journey-mi…

🤖 Azure/Copilot-For-Security
Microsoft Azure has open sourced resources related to Microsoft’s Copilot for Security, including:
* Customer guides
* Logic Apps
* Plugins
* Sample prompts
* Promptbook samples
* Technical workshops
#cybersecurity
github.com/Azure/Copilot-…