CNBY Security
@clownbaby_oi
cybersecurity
ID: 1499396156635418626
03-03-2022 14:48:25
501 Tweet
35 Takipçi
367 Takip Edilen








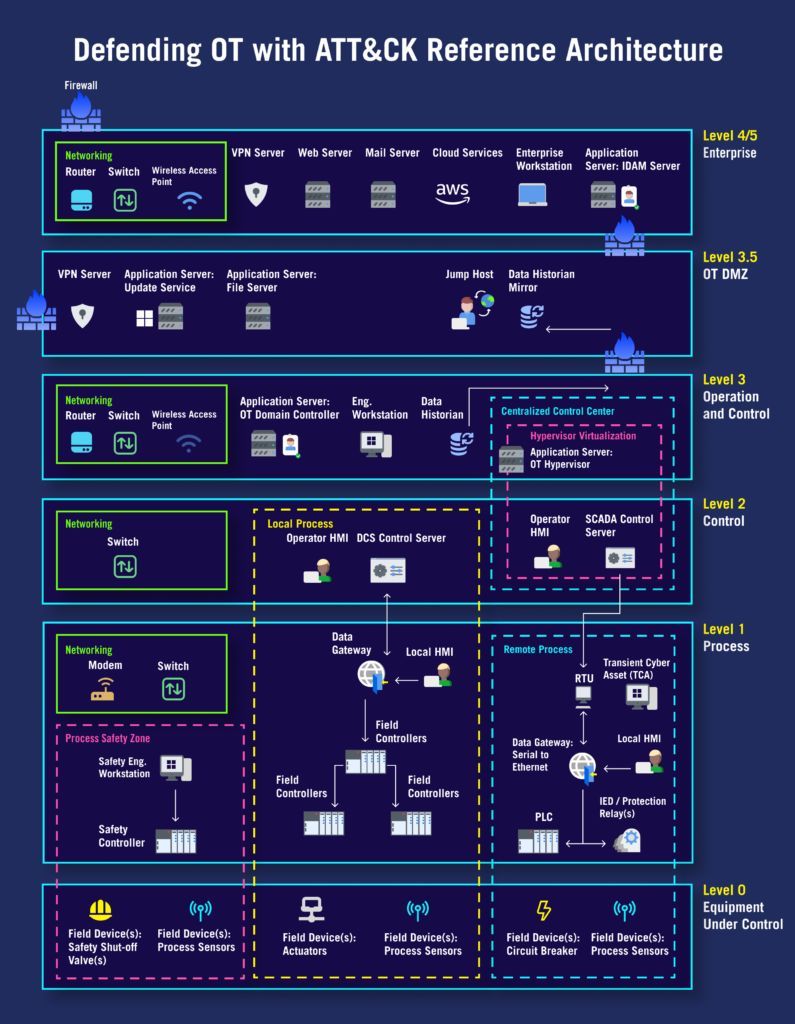
Nerds angry at Proton Mail today (yesterday?) due to internet drama (as is tradition). People are big mad. Is it a big deal? Are people overreacting? Why did normie accounts comment on the issue like they know what's going on? Phrack Zine did some silly things on the internet. They