7h3h4ckv157
@7h3h4ckv157
Reformed Hacker | Hall of Fame: Google, Apple, NASA, 𝕏 (FKA Twitter) & Many more | CVE ×4 | HTB Rank: Guru | Engineering + Research | Clandestine
ID:1277496365145133056
https://linktr.ee/7h3h4ckv157 29-06-2020 06:57:46
4,5K Tweet
18,1K Takipçi
91 Takip Edilen

Hey, Hackers! 👋🏻
Do they ask you for bug bounty methodology??
Share this ✌🏻
Made by: Coffin
#BugBounty #BugBounty Tips #moneytips #infosec #Hacking






My team at bugcrowd is hiring an Application Security Engineer in the UK!
Feel free to hit me up with questions, or apply directly at grnh.se/aa0289b71us
Remote position open to applicants located in the UK 🇬🇧
#cybersecurity #hiring #bugbounty #bugcrowd


Excited to explore new web app pentesting opportunities! I'm seeking a mid-level role where I can continue to learn and grow. Looking for fully remote positions (MST timezone). Happy to provide an updated resume and would love to chat about any opportunities! #JobSearch

Pwning the Domain: Persistence by HADESS
Read: hadess.io/pwning-the-dom…
NB: Content Sharing != Content Stealing
#Hacking #infosec urity #infosec #Pentesting #redteam #pwn #CyberSecurity #CTF #CyberSecurity #ArtificialIntelligence #CyberSecurity Awareness



Excited to share my latest blog on Medium about my recent finding on bugcrowd!
Check it out here: link.medium.com/BRdf55dbMJb
#bugbounty #Hacking time #bugcrowd #infosec #Hacking #informationsecurity #cybersecurity #EthicalHacking

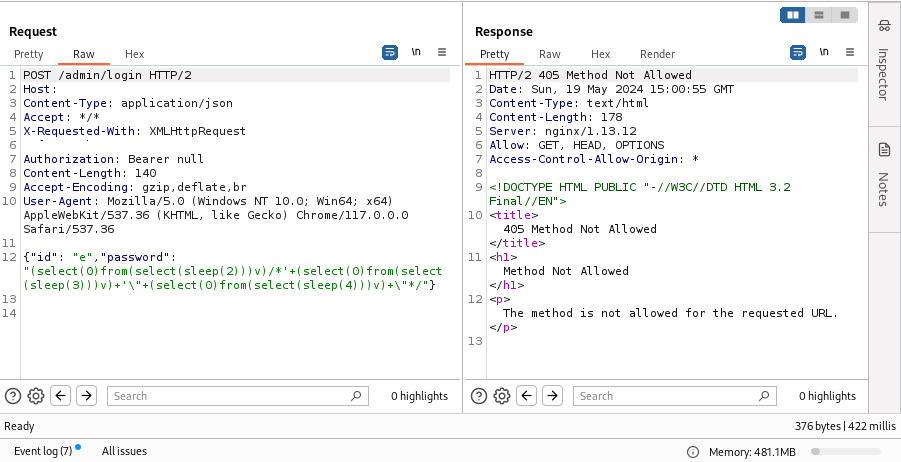
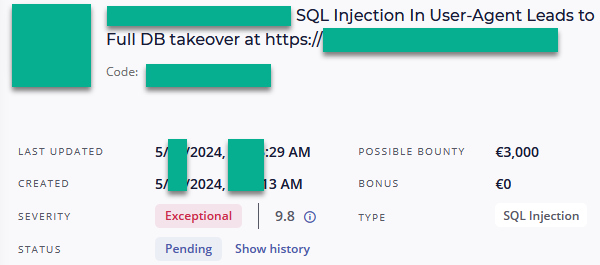
You can still find SQL injections in User-Agent/ or other request-headers; you just need a keen eye to find it.
Make sure to include SQLi testing on headers in your methodology. Developers often tend to ignore headers. #BugBounty #SQLi #SQLInjection


MOBEXLER 📍
A Mobile Application Penetration Testing Platform
github.com/enciphers-team…
NB: Content Sharing != Content Stealing
#Hacking #infosec urity #infosec #Pentesting #redteam #pwn #CyberSecurity #CTF #CyberSecurity #ArtificialIntelligence #CyberSecurity Awareness




Geogramint 🚨
OSINT tool that uses Telegram's API to find nearby users and groups.
Source: github.com/Alb-310/Geogra…
NB: Content Sharing != Content Stealing
#Hacking #infosec urity #infosec #Pentesting #redteam #pwn #CyberSecurity #CTF #CyberSecurity #ArtificialIntelligence