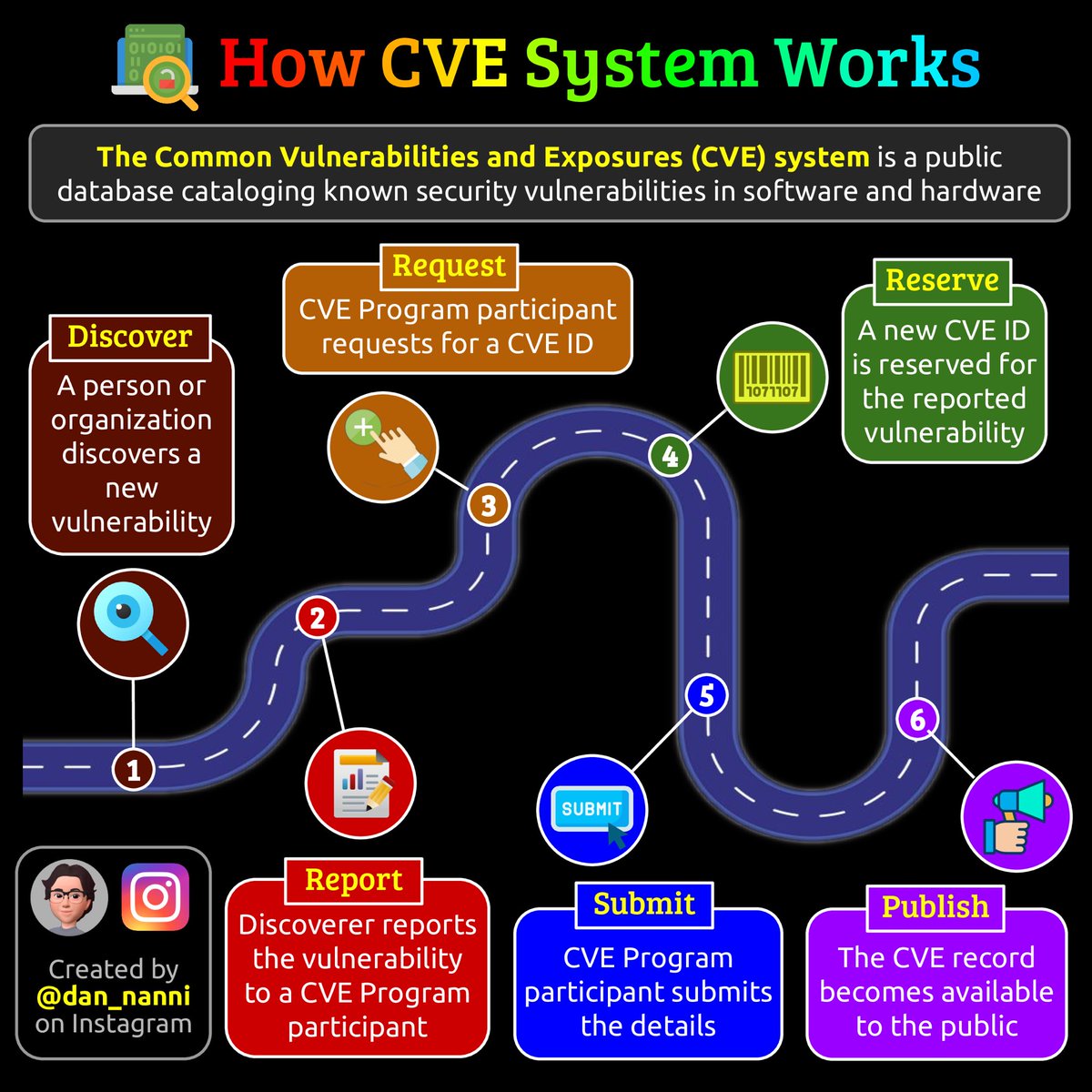
OSI Layers and Attacks
#infosec #cybersecurity #pentesting #redteam #informationsecurity #CyberSec #networking #networksecurity #infosec urity #cyberattacks #security #linux #cybersecurity awareness #bugbounty #bugbounty tips


Network Security Illustrated
#infosec #cybersecurity #pentesting #redteam #informationsecurity #CyberSec #networking #networksecurity #infosec urity #cyberattacks #security #linux #cybersecurity awareness #bugbounty #bugbounty tips


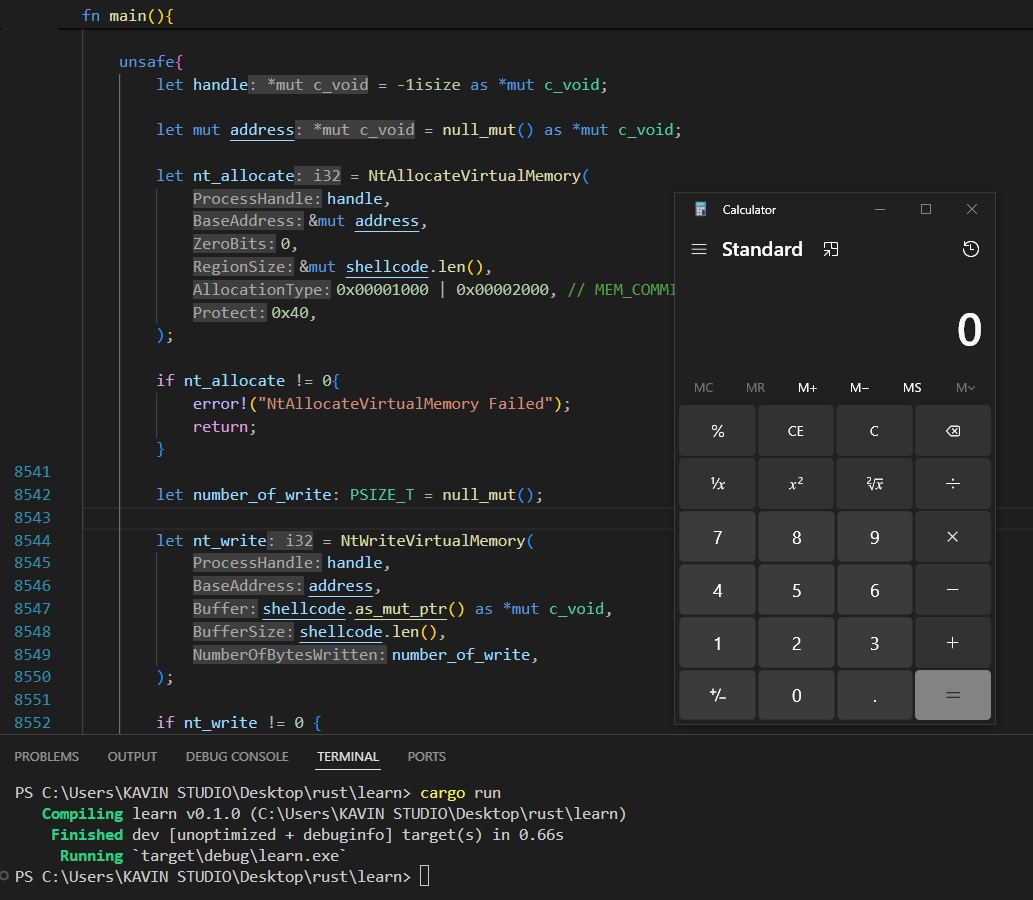
Malware Development Series
ShellExec Through Syscalls: github.com/Whitecat18/Rus…
Local Thread Hijacking: github.com/Whitecat18/Rus…
Remote Thread Hijacking: github.com/Whitecat18/Rus…
#maldev #rust #redteam #cybersecurity #infosec urity #infosec #security #thread #development

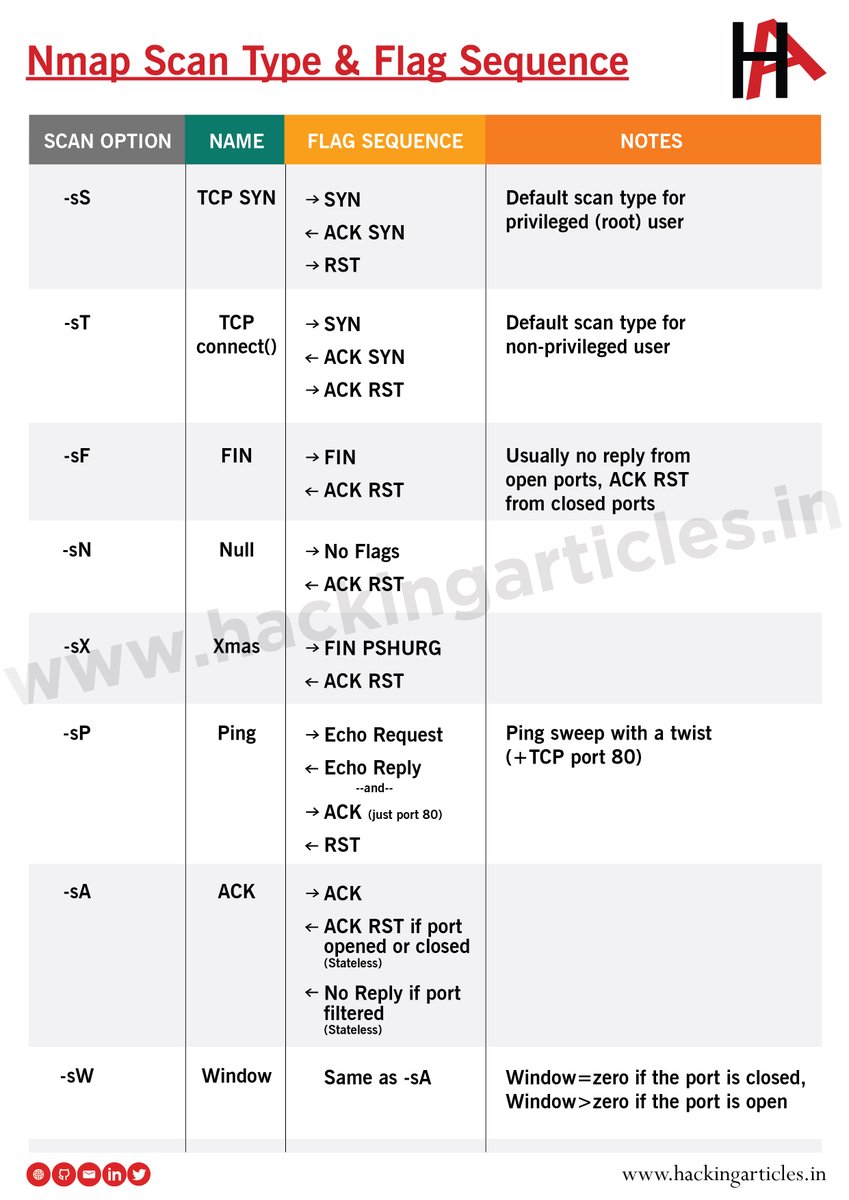
Nmap Scan Type & Flag Sequence
#infosec #cybersecurity #pentesting #redteam #informationsecurity #CyberSec #networking #networksecurity #infosec urity #cyberattacks #security #oscp #cybersecurity awareness #bugbounty #bugbounty tips


Types of Shell in Linux
#infosec #cybersecurity #pentesting #redteam #informationsecurity #CyberSec #networking #networksecurity #infosec urity #cyberattacks #security #linux #cybersecurity awareness #bugbounty #bugbounty tips



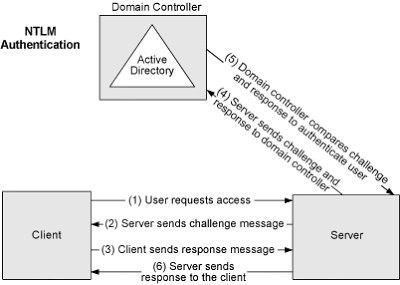
Pass the hash: Gaining access without cracking passwords 🚨‼️
Source: meriemlarouim.medium.com/pass-the-hash-…
#Hacking #infosec urity #infosec #Pentesting #redteam #pwn #CyberSecurity #CTF #CyberSecurity #cybersecuritytips #CyberSecurity Awareness

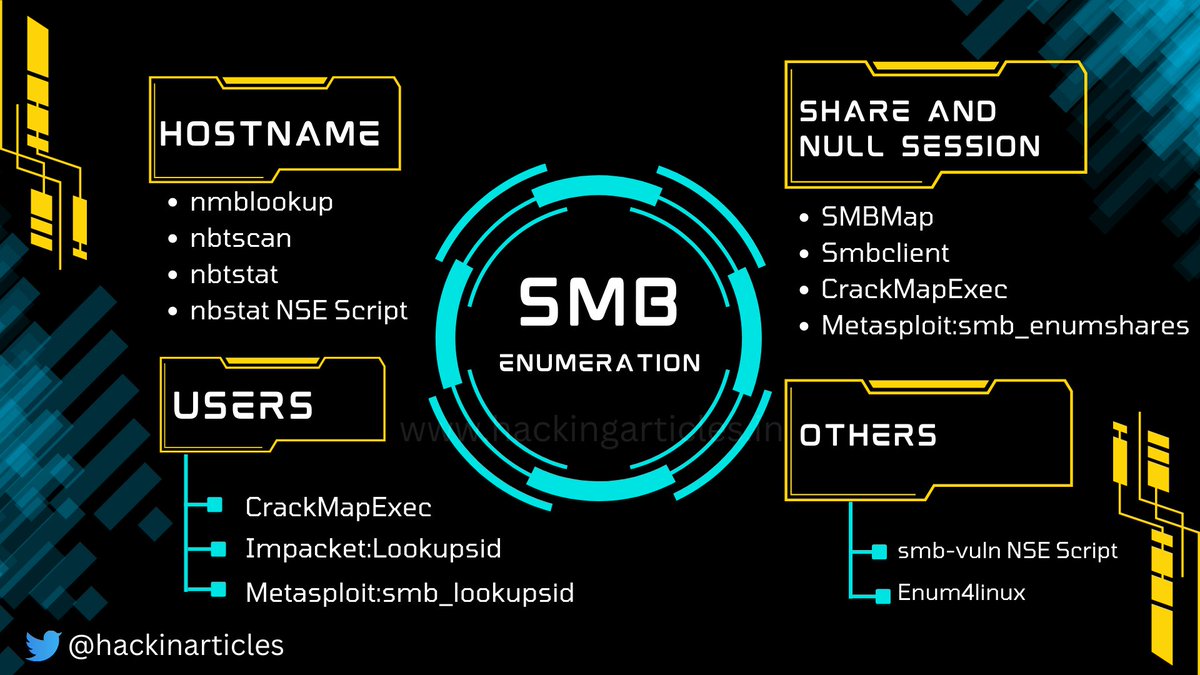
SMB Enumeration Cheat Sheet
#infosec #cybersecurity #pentesting #redteam #informationsecurity #CyberSec #networking #networksecurity #infosec urity #cyberattacks #security #oscp #cybersecurity awareness #bugbounty #bugbounty tips

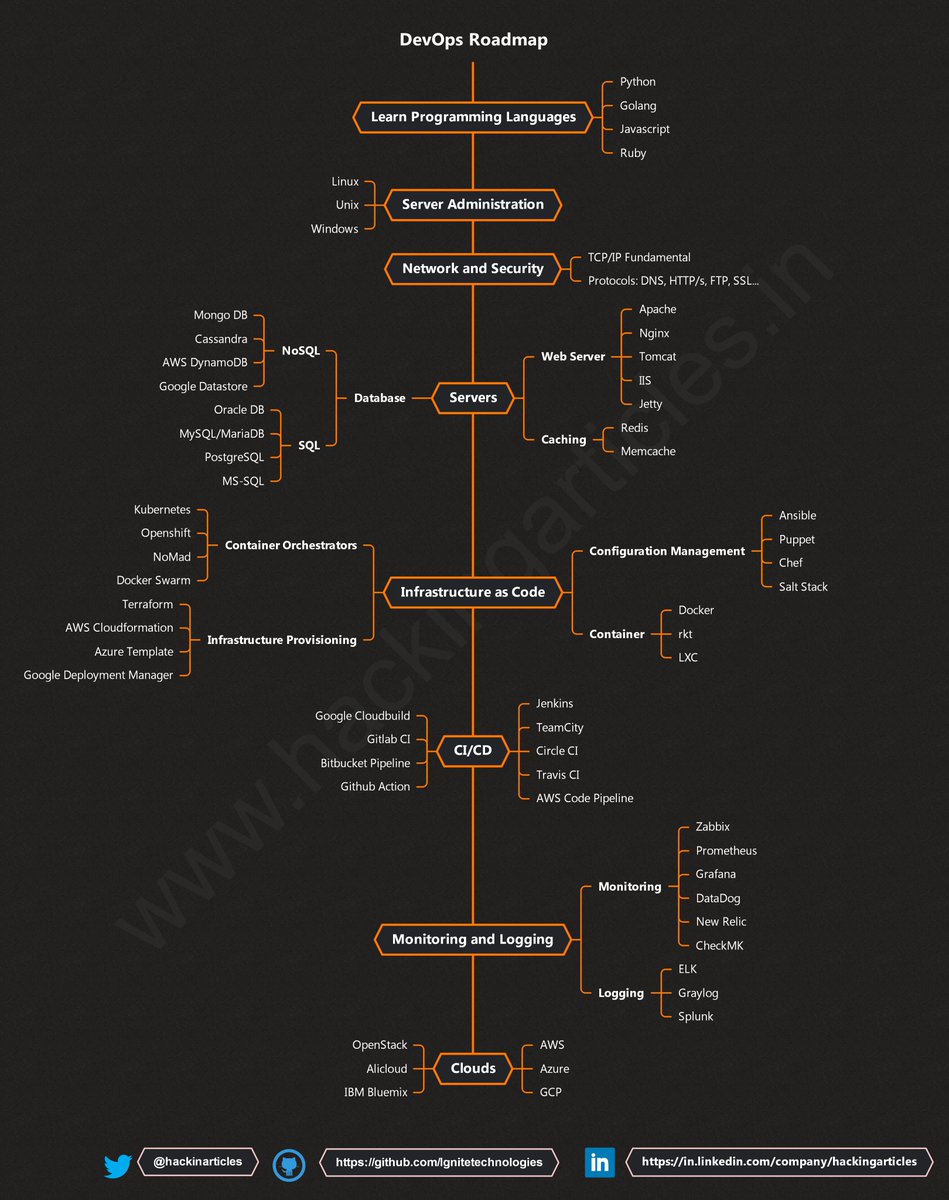
DevOPS Cheat Sheet
🔴⚫️Full HD Image: github.com/Ignitetechnolo…
#infosec #cybersecurity #pentesting #redteam #informationsecurity #CyberSec #networking #networksecurity #infosec urity #cyberattacks #security #linux #cybersecurity awareness #bugbounty #bugbounty tips


Popular Acronyms for SOC Teams
#infosec #cybersecurity #pentesting #redteam #informationsecurity #CyberSec #networking #networksecurity #infosec urity #cyberattacks #security #linux #cybersecurity awareness #bugbounty #bugbounty tips


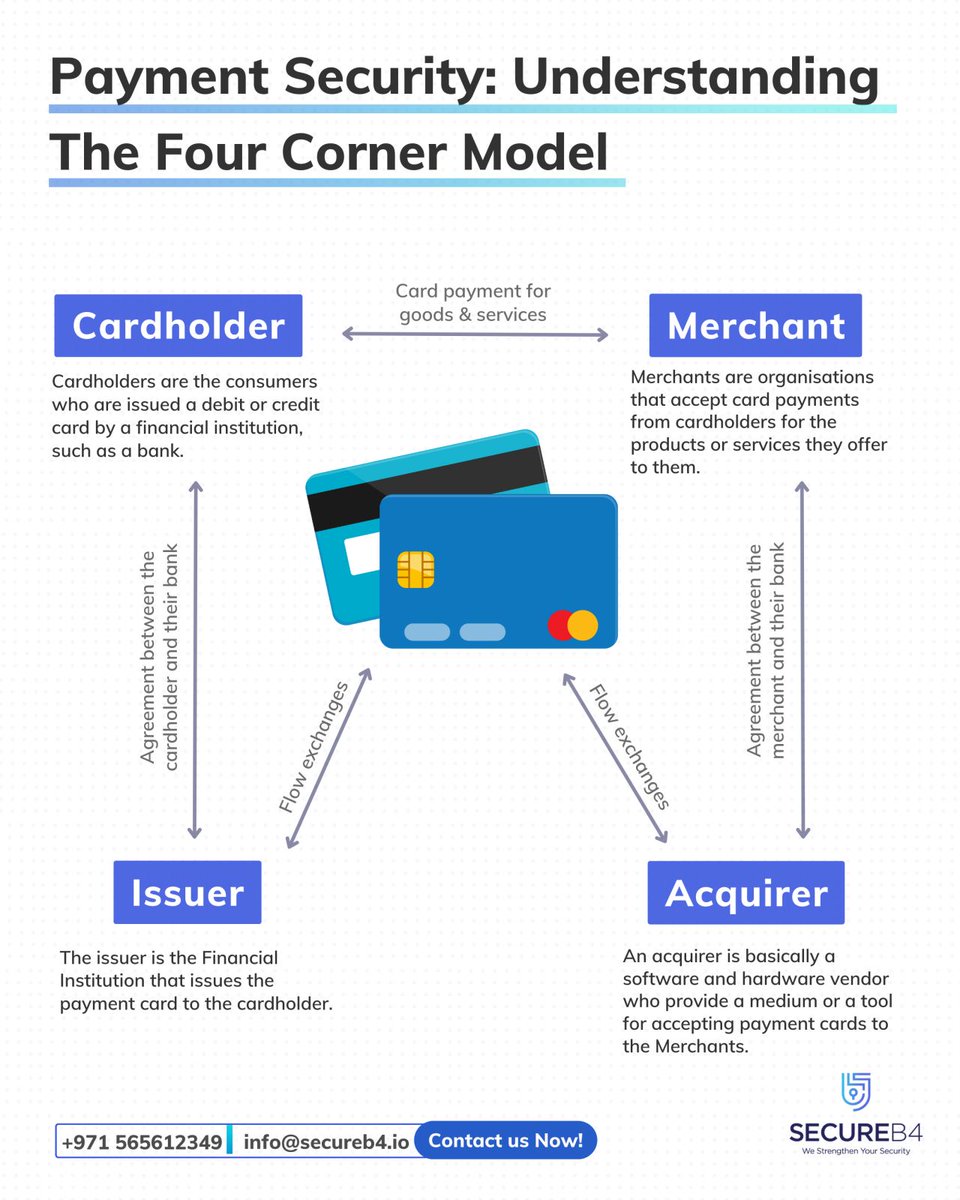
Payment Security Model
#infosec #cybersecurity #pentesting #redteam #informationsecurity #CyberSec #networking #networksecurity #infosec urity #cyberattacks #security #linux #cybersecurity awareness #bugbounty #bugbounty tips

Another useful thing that sqlmap has is the Google Dorking flag. Combine with your favorite dork increase change finding SQLi:
sqlmap -g 'site:target.com inurl:\'.php?id=1\''
#SQLi #infosecurity #cybersecurity


Hey Hackers 👋🏻
Here's the list of resources for those interested in getting started in bug bounties!
Credit: github.com/nahamsec/Resou…
#Hacking #infosec urity #infosec #Pentesting #redteam #pwn #CyberSecurity #bug #bug bountytips #CyberSecurity #cybersecuritytips #BugBounty

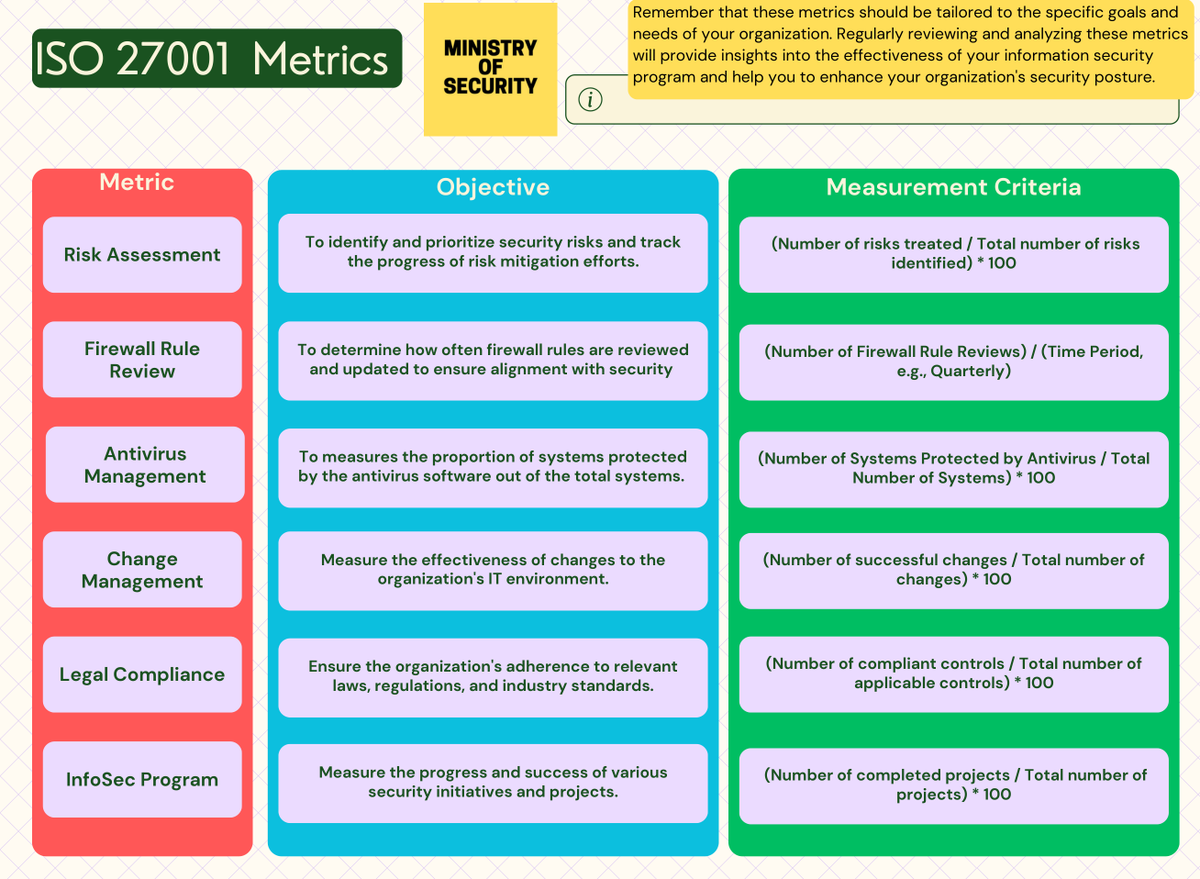
ISO 27001 Metrics
#infosec #cybersecurity #pentesting #redteam #informationsecurity #CyberSec #networking #networksecurity #infosec urity #cyberattacks #security #linux #cybersecurity awareness #bugbounty #bugbounty tips

DevOPS Cheat Sheet
#infosec #cybersecurity #pentesting #redteam #informationsecurity #CyberSec #networking #networksecurity #infosec urity #cyberattacks #security #linux #cybersecurity awareness #bugbounty #bugbounty tips