
Zero Trust Security
#ZeroTrustSecurity #Cybersecurity #Infosec #CloudSecurity #NetworkSecurity #EndpointSecurity #DataSecurity #IdentityAccessManagement #ITSecurity #EnterpriseSecurity #CyberRisks #CXOReview @CXOReview rfr.bz/t5k2uua


Cybercriminals are always looking to exploit your innocence, just like naive sheep can be easily trapped by a clever wolf.
Never trust; always verify.
A zero-trust security approach can help; reach out to learn how.
#zerotrustsecurity


Konvergenz today forces with millions around the world celebrating the Safer Internet Day - ' Together for a better Internet' ensuring a better online experience for all using reliable Zero Trust solutions.
konvergenz.co.ke
#zerotrustsecurity #saferinternetday


Wondering what #ZeroTrust Security is and why it matters? Let us break it down for you! #ZeroTrust is an approach that assumes no trust in any user or device, requiring continuous verification. It's vital because traditional #security models can't keep up with evolving threats.


Less than 24hours for our webinar on Zero Trust strategy. Reserve your seat now!!
Register using scan code or link here -> wati.com/wati-zscaler-z…
#webinar #zerotrust security #zerotrust #zerotrust webinar #cybersecurity #cybersecurity webinar


With OneClick Access, strengthen your network security by configuring a Software Defined Perimeter (SDP), ensuring that authenticated users can only access allowed resources and not the entire network:
utunnel.io/solutions/soft…
#sdp #zerotrust #zerotrust security #networksecurity


La méthodologie Zero Trust consiste à ne jamais faire confiance par défaut et à toujours tout vérifier.
buff.ly/3J0dUz1
#cybersecurite #itsecurity #dataprotection #infosec #infosec urity #zerotrust security #zerotrust


Few Reasons Why Enterprises Need #ZeroTrustSecurity | Ampcus Cyber
Why do enterprises need Zero Trust #Security ? Here are a few compelling reasons:
👉🏽 Evolving Threat Landscape
👉🏾 Protect Sensitive Data
👉🏽 Mobility and Remote Work
👉🏾 Insider Threats
#zerotrust #cybersecurity



Session on Zero Trust #citrix #cugc #cloud #deliverapps #zerotrustsecurity Citrix User Group Community (CUGC) Citrix CUGC Indy
Virtual XL

7 Biggest Trends In Data Privacy And Security:
tycoonstory.com/7-biggest-tren…
Next DLP #DataPrivacy #technology #DataSecurity #businesses #databreaches #phishing #dlp #zerotrustsecurity #cybersecurity #cloudstrategy #hybridmodel #itinfrastructure #securityprotocols


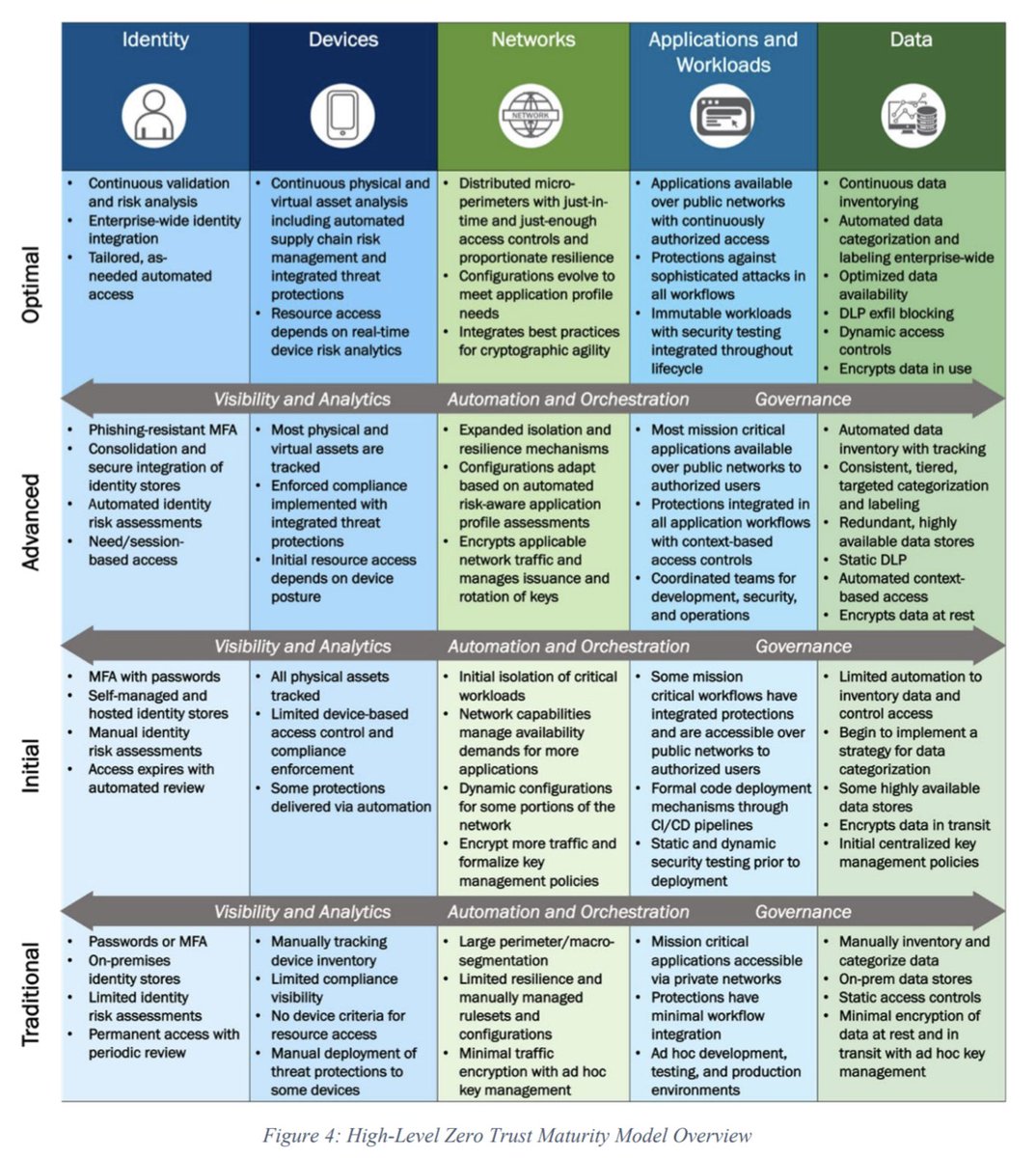
Zero Trust Security Maturity Model by CISA 👇
#ZeroTrustSecurity #CyberSecurity
cisa.gov/zero-trust-mat…

.Switch Connect & #DefensX have joined forces to offer advanced #ZeroTrustSecurity solutions. With threats on the rise, it's essential to stay protected. Let us help you achieve comprehensive protection quickly & affordably. Read the #pressrelease here - ow.ly/jQzX50OAu4a


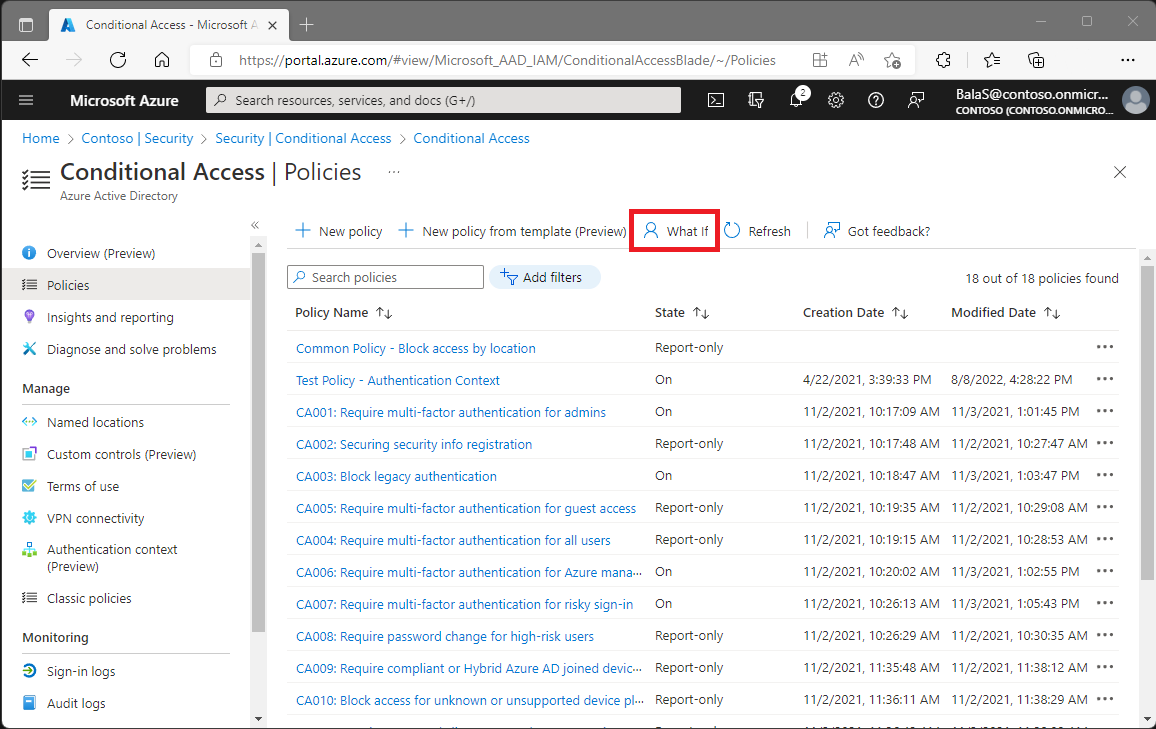
Discover the power of foresight with #Microsoft Entra's Conditional Access 'What If' tool! 🔍 Simulate policy impacts before they go live to ensure security without disrupting workflow.🌩️🔐
#BreachingAzure #BlueTeam #Microsoft Entra #ConditionalAccess #ZeroTrustSecurity #CloudSec

🔑 Keeper Security's 24-word recovery enables safer recovery of #Keeper vaults.
🔑 Keeper's platform ensures #ZeroTrustSecurity . Data is only decrypted on synchronized devices.
➡ Learn more: ow.ly/3mm750Ovees
#DataProtection #CyberSecurity #PasswordManagement


#Blog 📝 | #CyberThreats demand proactive measures. #ZeroTrust philosophy, popular due to #cloud expansion & remote work, aims to bolster security. Learn more 🔗bit.ly/3WuNUTh #WeHackYourSoftware
#appsec #cybersecurity #zerotrustsecurity #devsecops #securiytesting


Gov agencies adopt Zero Trust Security: Never assume safety, rigorously verify every access point.
The future demands vigilance and adaptation for a safer digital world. #ZeroTrustSecurity #CyberSecurity

Our latest article explores the strategic adoption of Zero Trust, offering insights into core principles, benefits, and implementation strategies for small and medium-sized businesses. #ZeroTrustSecurity #Cybersecurity #TuesdayFeeling #tuesdayvibe
hubs.lu/Q02t21150

#5GFactor Video Research Note: hosts Ron Westfall, #TheFuturumGroup & Shelly Kramer discuss the limits of Retro Metro tech, why #CloudMetro is essential for experience-first networking & @Juniper's Cloud Metro portfolio. bit.ly/41dONiv
#Juniper #zerotrustsecurity The Futurum Group

Day 12 of #CybersecurityAwarenessMonth 2023: Dive into Zero Trust Security with 7 key principles!
Fortify your network with user, device, and data security. Don't miss hands-on lessons on AppSecEngineer!
Start today: appsecengineer.com/main-menu-page…
#ZeroTrustSecurity #SecureOurWorld
