In support of the DoD’s Zero Trust Strategy, we're releasing activity-level guidance on how to use Microsoft cloud services to implement Zero Trust within the DoD and DIB. Read on: msft.it/6014YB4Oo #ZeroTrust

Today’s complex data environment requires greater granularity and multiple factors in access control decisions – beyond just identity.
Improve your security and risk posture with zero trust architecture: gtnr.it/3TQKffP
#GartnerSEC #Cybersecurity #ZeroTrust


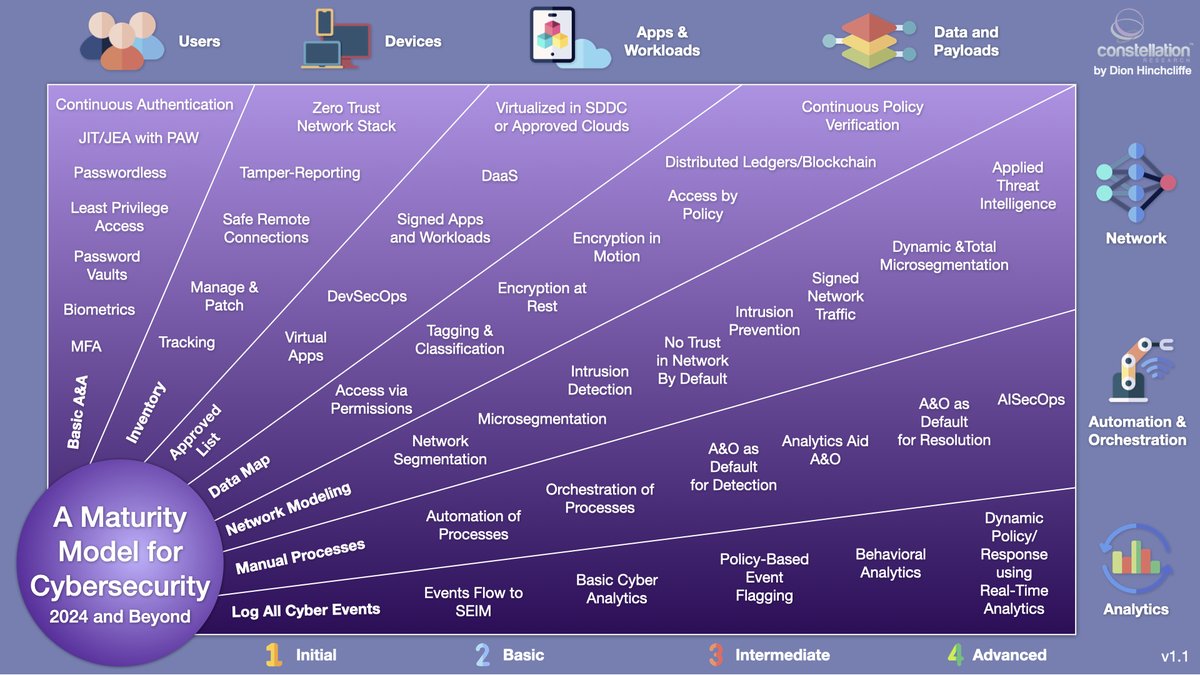
My latest updated #cybersecurity model for 2024.
Important trends:
- The move to #zerotrust
- #Microsegmentation
- Continuous authentication
- Applied threat intelligence
- Rise of #AI SecOps
#CIO #CISO #ZTA #AI


Be relentless in your attention to your defenses. Future-proof your military IT environment with Zero Trust tools, delivered by Insight Public Sector.
#InsightPublicSector #IPSDefense #Cybersecurity #ZeroTrust ms.spr.ly/6001Y6gsh

The key to a successful #ZeroTrust strategy: converged vendors and solution interoperability.
Learn the latest Zero Trust strategy priorities: ftnt.net/6013b1c3t



Think Zero Trust is enough? Not quite. 🙅♀️
Read on to hear what our CEO Camellia Chan has to say about achieving true Zero Trust environments, in this article for the Forbes Technology Council: forbes.com/sites/forbeste…
#zerotrust #security #cybersecurity #hardware #AI

Remember, AI will not replace people. People who use AI will replace people.
#ai #cybersecurity #zerotrust


Putting all the eggs in the #ZeroTrust basket. 🐣🧺
Here's why. ⤵️bit.ly/4aVUgPO The New Stack

In today's digital landscape, adopting a zero trust approach is crucial for safeguarding sensitive information and mitigating cyber risks. By prioritizing identity verification, organizations can stay one step ahead of cyber attackers. #Cybersecurity #ZeroTrust

You wouldn't act like this. But your business network might be!
Our recent blog makes it easy to understand zero trust and why it's important: marconet.co/4aBkcjE #ZeroTrust #Cybersecurity #UserAuthentication



Join us #247.tech
✅ Zero Trust Network Access
✅ Control Access to Your Network
Grant access based on strict verification, not just location, and prevent data breaches...!!!
Web: 247.tech
#zerotrust #security #networksecurity #ZeroTrustNetworkAccess



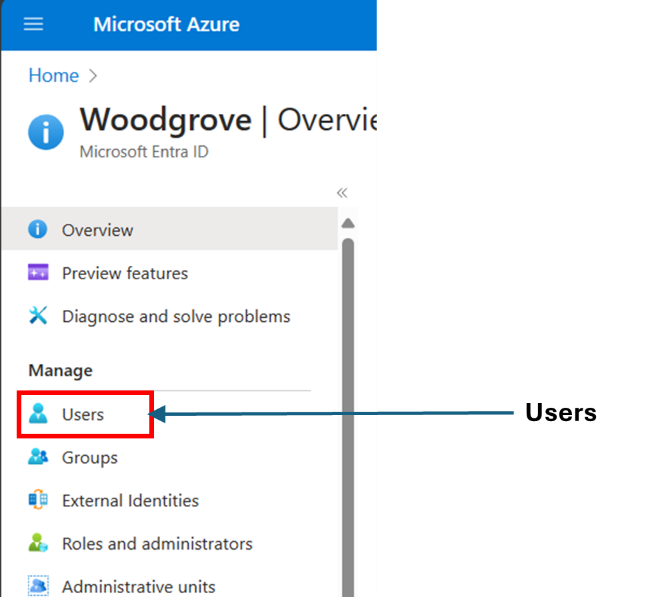
🥩🥩Mr T-Bone tip! 🔒 Introducing the new Org Branding role for #EntraID . Keep it tight, keep it zero trust with least privilege. 💪
#Cybersecurity #IAM #zerotrust
#MVPBuzz #MicrosoftTechCommunity
nuel.ink/Gkpo9C


Data loss is a thing of the past with IMS's Data Protection services. Leveraging Rubrik’s Zero Trust model, we offer financial institutions robust security across all environments. Secure, verify, recover → imscloudservices.com/data-protectio…
#DataProtection #ZeroTrust


Stop using username/password for any kind of auth! If you must allow it, make sure you use an overlay network that authenticates and authorizes incoming connections first like openziti! #zerotrust #appsec #netsec #killthevpn
blog.talosintelligence.com/large-scale-br…