
#Kapeka #Backdoor #Malware #Sandworm #APT
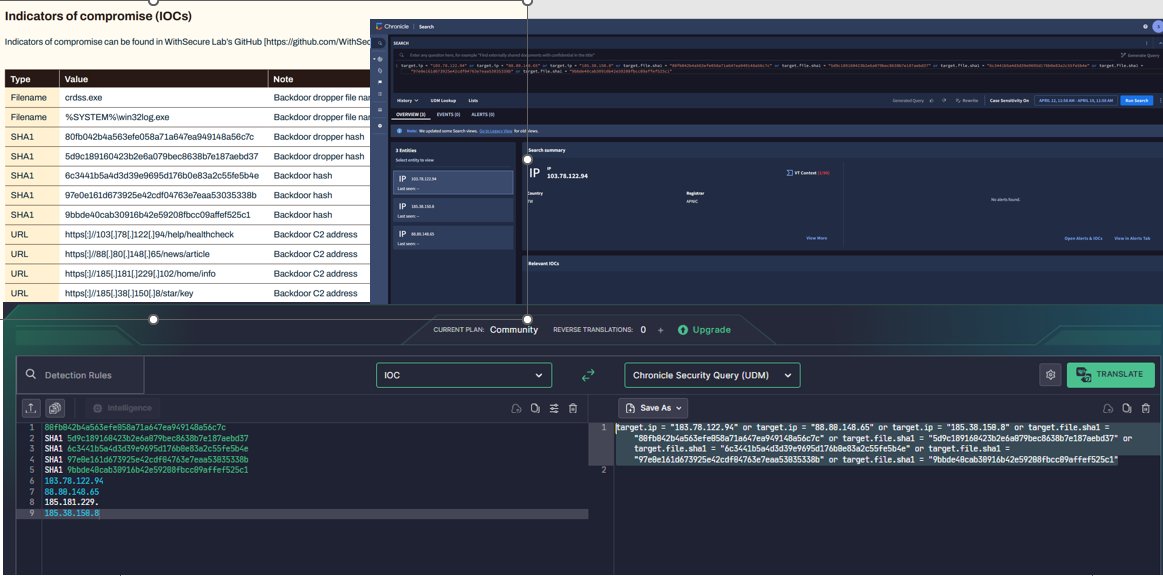
uncoder_io and @google chronicle - example of how fast you can do #threathunting with #uncoderIO and IOCs from the threat intelligence report WithSecure™ about the novel backdoor #Kapeka and translate it into SIEMs. Superfast!

Feeling lost while #pivoting 🔎and #threathunting 🎯 for adversaries 🦹?
Come to #PIVOTcon24 and learn from the best threat researchers in our field (speakers and attendees).
You will have lots of opportunities to discuss #CTI #threatintel


🗓 SAVE THE DATE | TECH TALK SERIES
Episode 3 : Jeudi 25 Avril - 11h30 GMT+1
💡 Rejoignez-nous pour un webinaire exclusif où nous explorerons les capacités de pointe de Nucleon EDR pour le #threathunting .
👉 Inscrivez-vous pour réserver votre place : events.teams.microsoft.com/event/04575b39…


#FOR577 teaches the skills to identify, analyze, & respond to attacks on #Linux platforms & how to use #threathunting techniques to find stealthy attackers
Take it with Jim - #BlackLivesMatter 🌈 at SANS Institute Rocky Mountain in June
Register here: sans.org/u/1vgv



You can use this Shodan search query http.html_hash:-1303565546 to find Palo Alto Networks GlobalProtect appliances that might be vulnerable to the recent CVE-2024-3400 RCE.
#PaloAltoNetworks #CVE20243400 #VulnerabilityScanning #ThreatHunting #InfoSec #Pentesting


Interesting one. Worth a view!
[Repo] The Threat Hunter Playbook
buff.ly/3xyNkcR
#ThreatHunting #CyberSecurity
![David das Neves (@david_das_neves) on Twitter photo 2024-04-15 06:41:01 Interesting one. Worth a view!
[Repo] The Threat Hunter Playbook
buff.ly/3xyNkcR
#ThreatHunting #CyberSecurity Interesting one. Worth a view!
[Repo] The Threat Hunter Playbook
buff.ly/3xyNkcR
#ThreatHunting #CyberSecurity](https://pbs.twimg.com/media/GLL79FNW0AAeHSO.jpg)



🚨 Just released: SANS Institute 2024 Threat Hunting Survey with Cyborg Security! Discover key insights on the evolving #cybersecurity landscape. Download now: huntwithcyb.org/3UlthHQ
#threathunting #threatintel #informationsecurity #securityprofessionals


In #cybersecurity , we often overlook behaviors, focusing instead on IOCs and artifacts. Recognizing behaviors as starting points for investigations, not just confirmatory evidence, is a missed opportunity for #security teams. Learn more: huntwithcyb.org/3UwqI65
#threathunting



Galera, sugestões de cursos sobre threat hunting/cyber threat intelligence?
#threathunting #threatintel #ctia

🚨 #EMERGINGTHREAT – CVE-2024-3400 - PALO ALTO OS COMMAND INJECTION VULNERABILITY
Full Report & Hunt Collection: huntwithcyb.org/442fsBn
#threathunting #cybersecurity #infosec #threatupdate


If you’re currently job hunting, then you may want to know all about #ResumeLooters . Find out why and what dangerous web properties may land you in hot water in: circleid.com/posts/20240322…
#cybersecurity #threatintelligence #threathunting


Threat hunting is still at an early stage, but #AI can help
buff.ly/4afJ14f
CSOonline @Censysio #tech #cybersecurity #security #CISO #CIO #CTO #threathunting #cyberthreats #cyberattacks #threatintelligence #genAI #generativeAI #automation #security automation


A good friend of mine, Deniz, put some nice Threat Hunting KQL queries out that you should not miss.
Follow the Breadcrumbs with Microsoft IR & MDI: Working Together to Fight Identity-based Attacks
buff.ly/3W2Bi5D
#CyberSecurity #ThreatHunting


Dig into Chronicle's powerful investigation views to hunt for threats. Pivot between related entities, enrich IoCs with VirusTotal intelligence, and uncover the scope of incidents. The built-in visualizations help you connect the dots faster. #ThreatHunting #IncidentInvestigation

