Who you gonna call? Elastic Security Labs has discovered GHOSTPULSE, a stealth loader that utilizes MSIX. Get all the details here → go.es.io/3FAX9YI
#ElasticSecurityLabs #malware #threatdetection


Have you prepared your environment for EAGERBEE, RUDEBIRD, and DOWNTOWN? Familiarize yourself with the three malware families and implement the YARA rules: go.es.io/3SnCVck
#ElasticSecurityLabs #malware #threatdetection

#100daysofCyberSecurity Day 71
Pyramid Of Pain - I have just completed this room! Check it out: tryhackme.com/room/pyramidof… #tryhackme #security #threathunting #threatdetection #threatresponse #pyramidofpainax via @realtryhackme
zʇunH ʎɐſ ɐsɐɟnW 🦁🦁🦁🦁 Cyber Caramel_Choco🍫

Our newest article explores how to set up an Okta threat detection lab through Elastic Security! Check out this amazing step-by-step tutorial from Terrance DeJesus: go.es.io/3V5ujZx
#ElasticSecurityLabs #securitytutorial #threatdetection

Very cool to see Permiso's research on here! threats.wiz.io/all-incidents/… Check out all our cloud threat research here -> permiso.io/blog #threatintel ligence #threatdetection #threatintel #cloudsecurity

🗞️ Your latest #cybersecurity insights including #supplychain attack detection, analysis of #ZeroDay exploits, #NIS2 & DACH #security events!
linkedin.com/pulse/cyber-fl…
#ITSecurity #ThreatDetection #NDR #NetworkSecurity #CyberAttack #CyberCrime #APT #ML #Exeon


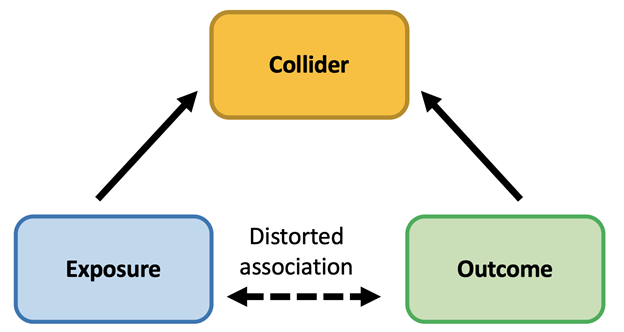
1) I've been fascinated with using and applying statistical methods for #threatdetection . Specifically, the intersection of bias x threat detection, which can really ruin an analyst's day.
I'd like to introduce one bias I frequently observe: collider bias

Uncover how AI is transforming IT infrastructure and security, boosting maintenance, strengthening threat detection, and empowering your team.
Join the evolution today!
bluesummittech.com/blog/ai-system…
#AI #ITInfrastructure #SecurityOptimization #ThreatDetection #bluesummittech


Ensure your security with CA services from Security Pact! Detect threats, mitigate compromises, and trust us to safeguard your operations.
Visit securitypact.net or email [email protected].
#CompromiseAssessment #ThreatDetection #IncidentResponse #SecurityPact




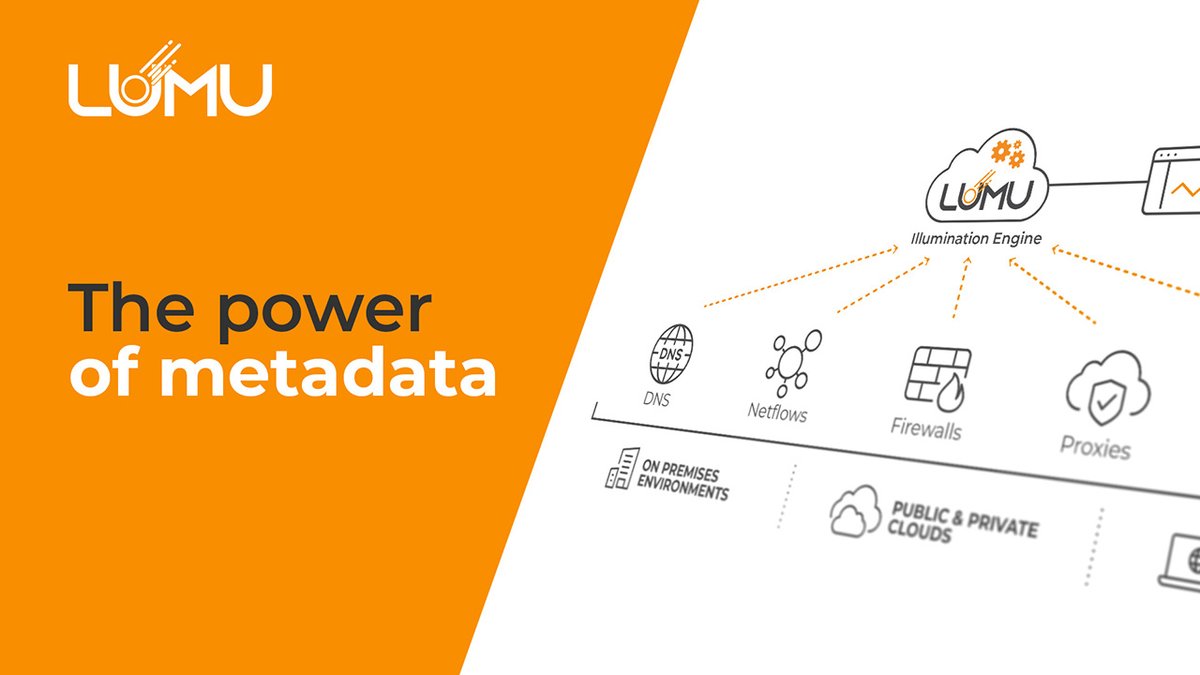
Curious about the role metadata plays in cybersecurity? Learn how Lumu’s thorough analysis of network metadata offers a comprehensive understanding of potential compromises. >> zurl.co/zgYe
#Cybersecurity #Metadata #NetworkSecurity #ThreatDetection

Excited to share our latest blog: Learn how AI is revolutionizing cybersecurity and protecting our digital world.
To Read More: bit.ly/4aEAM2f
#QBrainX #Cybersecurity #AI #ThreatDetection #SecureFuture #blogpost #ThursdayRead #QBX #digitalworld #transformingyou


Interested in the dynamics of #threatdetection ? Dr. Clay Moody will be sharing how the Secureworks Tactic Graphs Engine, coupled with innovative countermeasures, aids in early detection of threat behavior.
Register for #TISummit23 : bit.ly/3REVYi1


Liberty Defense Receives $1M Advance Payment from Viken Detection for HEXWAVE Systems
libertydefense.com/news/liberty-d…
$SCAN.V $LDDFF
#SecurityNews #AI #TouchlessScreening #SecurityScreening #ThreatDetection #AviationSecurity #EmployeeScreening

Join us for insights, networking, and golf at the @Splunk Executive Event with #MatlalaGroup
Register now: ow.ly/9Vjr50RiP8r
#Splunk #DigitalResilience #Splunk #DataAnalytics #Cybersecurity #ITSecurity #ThreatDetection #CloudComputing #SIEM #AI #Chiief #Chiief Events


Cybersecurity Automation: Threat Detection and Incident Response
meteoriqs.com/cybersecurity-…
#meteoriQs #quality thrivesUShigh #productdevelopment #agility #quality #efficiency #cybersecurity #threatdetection #protectdata #securitymeasures #cyberblog #automation #blogpost


Between annual #informationsecurity audits doesn't have to be your blindspot. baisecurity.net/network-vulner…
#vulnerabilitymanagement #vulnerabilityassessment #vulnerabilityscanning #threatdetection #ITleaders #iot #threatintelligence #cybersecurity #ITdirectors #CIOs #CISOs #CSOs