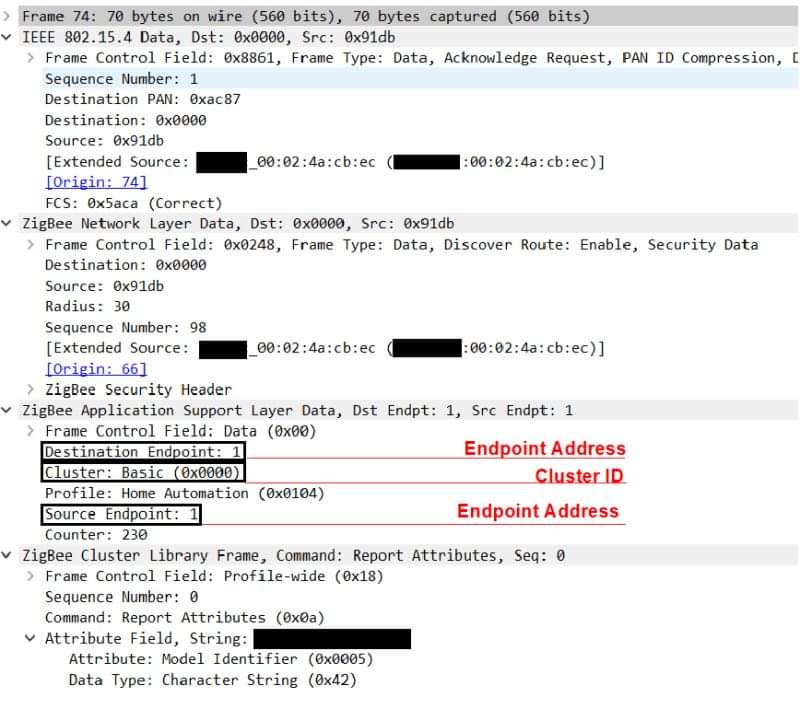
IoT Security – Part 5 (ZigBee Protocol – 101)
payatu.com/masterclass/io…
#Pentesting #IoTSecurity #Infosec




Five ways to keep industrial control systems safe from cyberattacks
via Dean Parsons
#IIoT #IoTsecurity #IndustrialIoT
technative.io/five-ways-to-k…

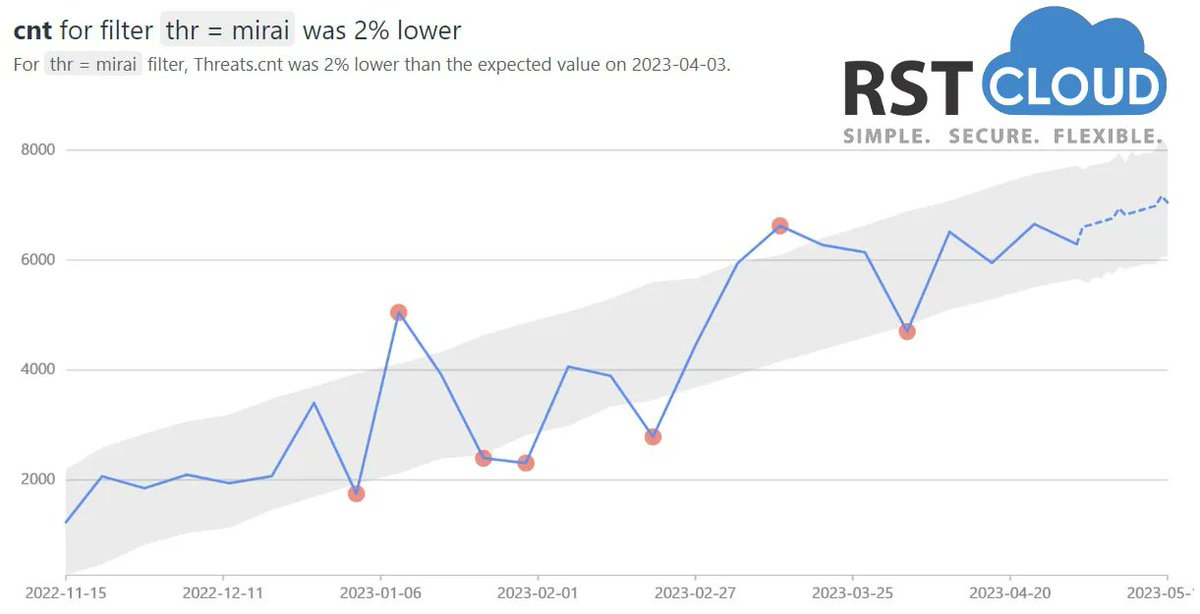
❗ Attention! The #Mirai botnet is still on the rise, confirming our earlier warnings since March. Don't let your guard down—ensure the security of your #IoT devices. Stay protected and prevent becoming part of the Mirai network. #Cybersecurity #IoT security #threatintel #rstcloud


Using the cloud on your mobile improves your security.
#Cloud security #Cloud #Cloud Computing #100DaysOfCode #Cybersecurity #Analytics #Bigdata #ITsecurity #IoT Security #MachineLearning #ArtificialIntelligence #IoT #5G #VPN #CISO
Source: Hooclass
👉hooclass.com/using-the-clou…


We are only a few short weeks away from our OT #Cybersecurity Summit in SCOTLAND! ✈️
Increase your understanding of how to use standards and conformance systems to keep #operationaltechnology safe and secure.
Pack your bags! We'll see you there!


The reason #security is so difficult in #IoT is that vendors are trying to tackle it off-device without a device presence. #EdgeComputing #IIoT #industrial #IT #iotsecurity





IoT Security – Part 5 (ZigBee Protocol – 101) payatu.com/masterclass/io… #Pentesting #IoTSecurity #Infosec


Email is the primary entry point of 94% of malware attacks.
#Cybersecurity #Infosec #Privacy #Cybercrime #IoTsecurity
#Cloudsecurity #DataSecurity


This will continue until there is improved operational visibility of the devices.
2 Years After #ColonialPipeline , US #CriticalInfrastructure Still Not Ready for #Ransomware - buff.ly/44vHzsu #OT #ICS #IIoT #industrial #iotsecurity #security #cybersecurity


We address the top 10 challenges in IoT
shorturl.at/aptAO
Overcome the hurdles and unlock the full potential of IoT
#IoT trends #iottopologies #iotsolutions #IoT #internetofthings #iotcommunity #IIoT #techblogs #technology #IoT Security #iotdata #DataPrivacy

Using the cloud on your mobile improves your security.
#Mobilesecurity #Cloud security #Cloud #Cloud Computing #VPN #100DaysOfCode #Cybersecurity #Analytics #Bigdata #ITsecurity #IoT Security #MachineLearning #ArtificialIntelligence #IoT #5G #VPN #CISO
👉hooclass.com/using-the-clou…


#AI for Successful #DigitalTransformation Strategies- #infographic
via Giuliano Liguori
CC: Office for Artificial Intelligence Artificial Intelligence Max Tegmark Artificial Intelligence Leader Carl Icahn Joscha Bach Judea Pearl Shivon Zilis
#ArtificialIntelligence #MachineLearning #ML #IoTSecurity #DataScientists #innovation #Tech



From Challenge to Solution: Navigating the Complexities of IoT Scalability
.
.
.
#kikai #kikai technologies #tech #it #iot #iot solutions #iot security #webdeveloper #websitedevelopment #development


Securing IoT Environments with the NIST Cybersecurity Framework
infocerts.com/securing-iot-e…
#IoTSecurity #CybersecurityFramework #NIST #RiskMitigation #SecureCommunication #FirmwareUpdates #IncidentResponse #DataProtection #BackupAndRecovery #CybersecurityChallenges #IoTDevices