Zach
@svch0st
Everything DFIR
@TheDFIRReport | @CuratedIntel | @XintraOrg
infosec.exchange/@svch0st
ID: 1039996215339839488
12-09-2018 21:56:34
210 Tweet
4,4K Followers
1,1K Following


Thank you to all that entered the The DFIR Report lab giveaway! Our winners are: 🎁Alberto Paco - Case #23825 🎁Dino Santic - Case #19438 🎁threathka - Case #23825 Winners - please DM me and I'll send through your lab!




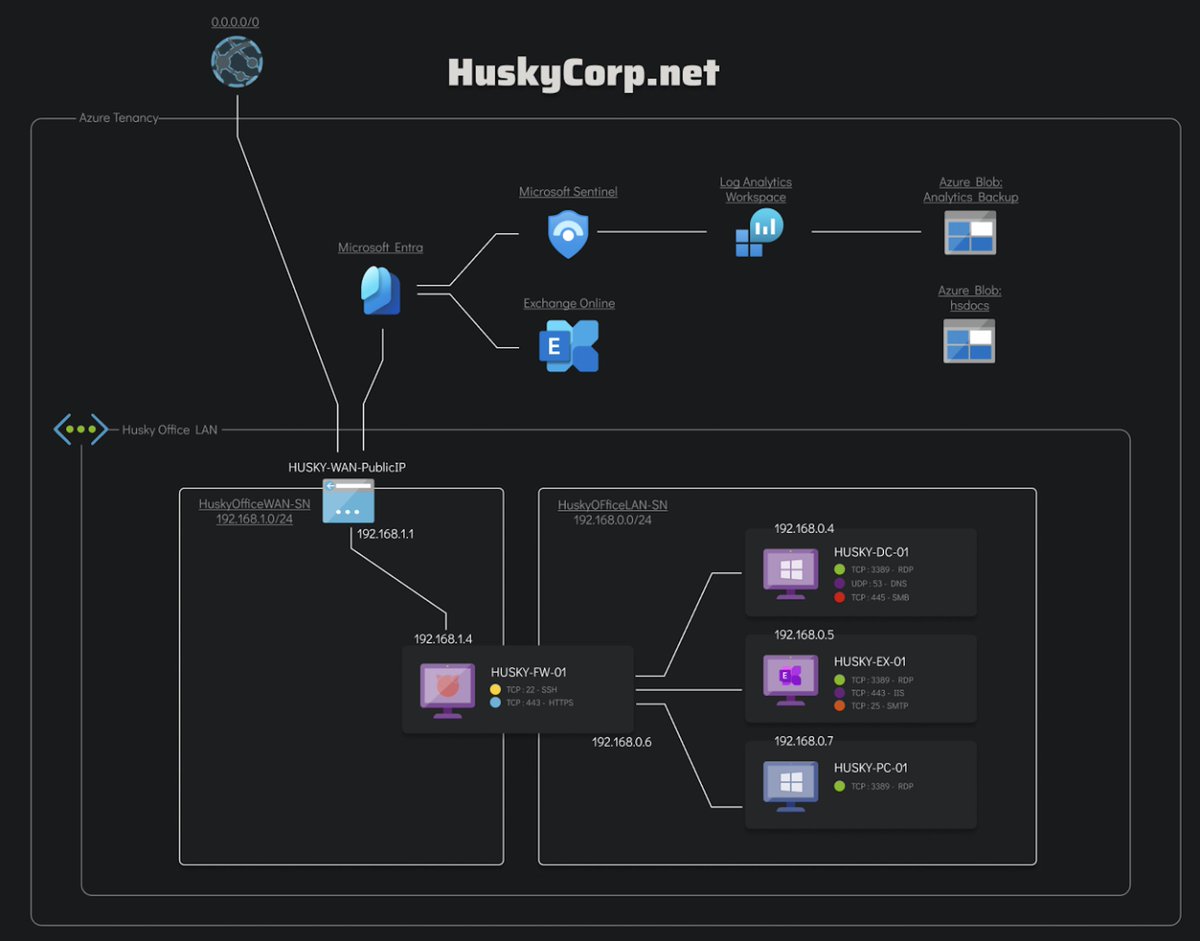
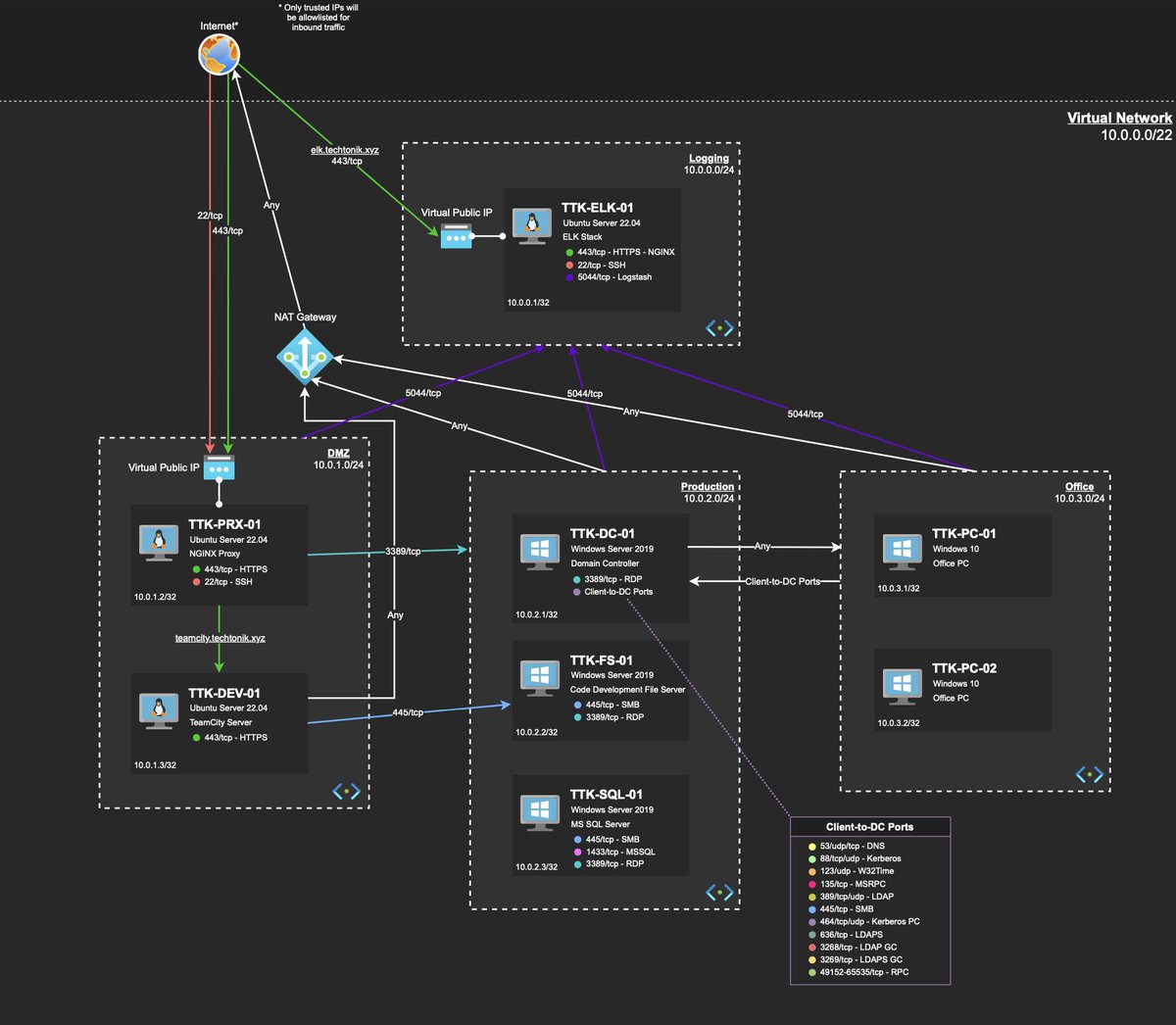
NEW LAB 🥳: WinDbg Crash Dump Analysis by DebugPrivilege Using WinDbg to analyze dumps of CVE-2024-29824 and CVE-2023-29357 exploited in the wild. 👇Solve the incident here 👇 xintra.org Test your memory forensic skills on: 👀Reflective DLL Injection