ʇɹǝɟɟns
@suffert
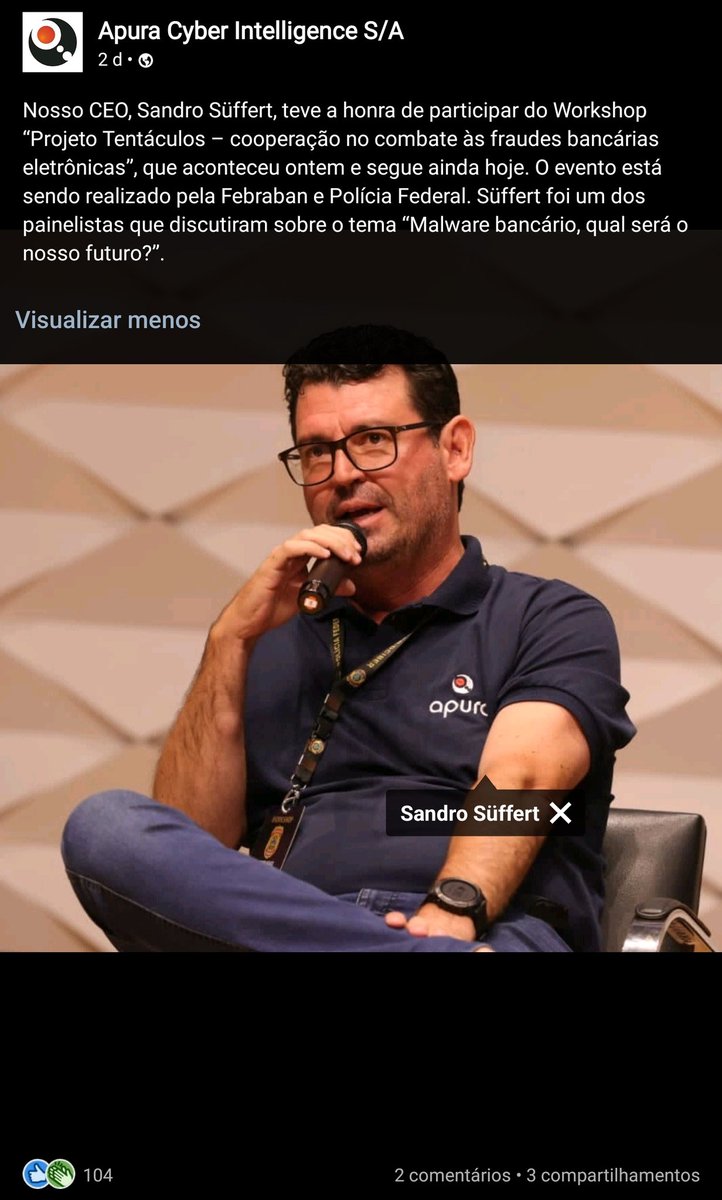
Sandro Süffert #Infosec and #DFIR Professional
CEO of APURA Cyber Intelligence S/A
ID: 89100152
http://apura.io 11-11-2009 03:47:49
24,24K Tweet
4,4K Followers
1,1K Following


Clandestine communications in cyber-denied environments - Numbers stations and radio in the 21st century (2023) doi.org/10.1080/183353… Open Access article by Tony Ingesson (Tony Ingesson) and Magnus Andersson, published in Journal of Policing Intelligence Counter Terrorism.