SecDim
@secdim
🎮 Attack & Defence Wargames: play.secdim.com 👉 The quickest and most effective way to upskill in AppSec, AISec, and more
ID: 2835553985
https://secdim.com 17-10-2014 21:51:19
298 Tweet
252 Takipçi
3 Takip Edilen









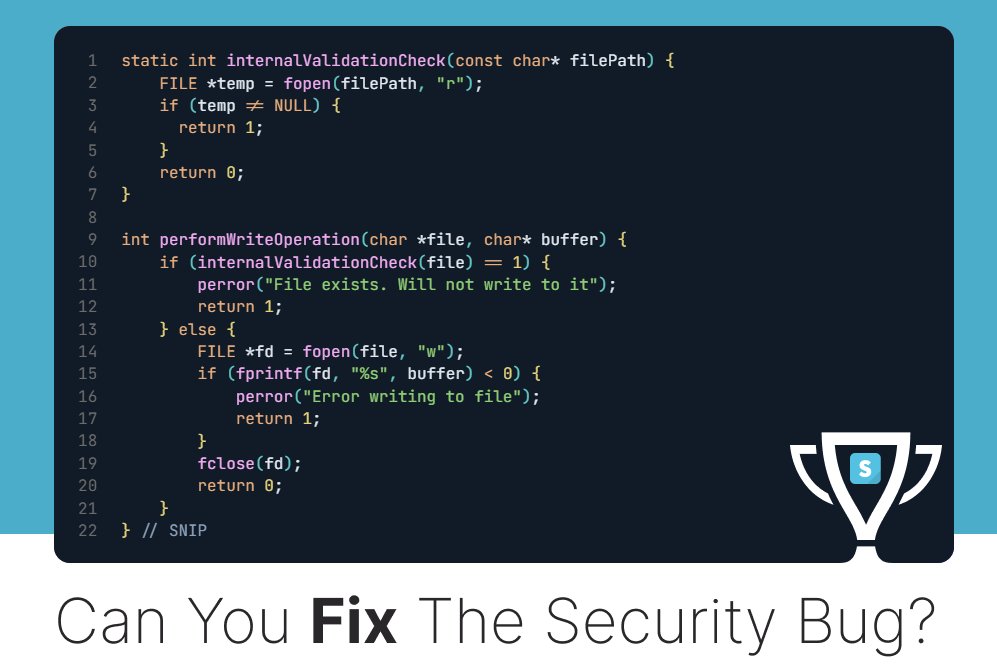
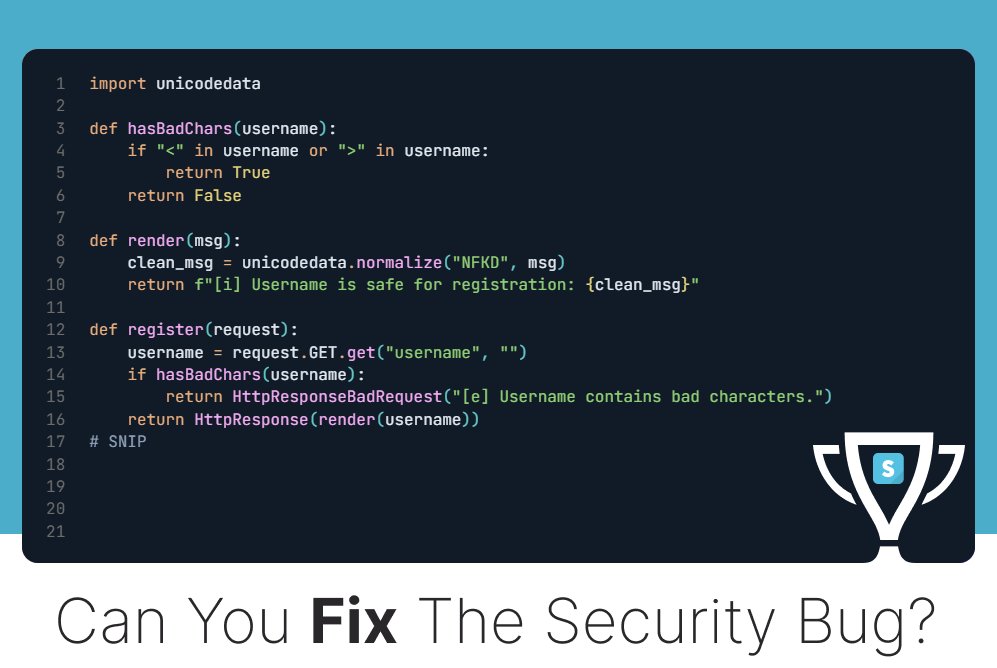
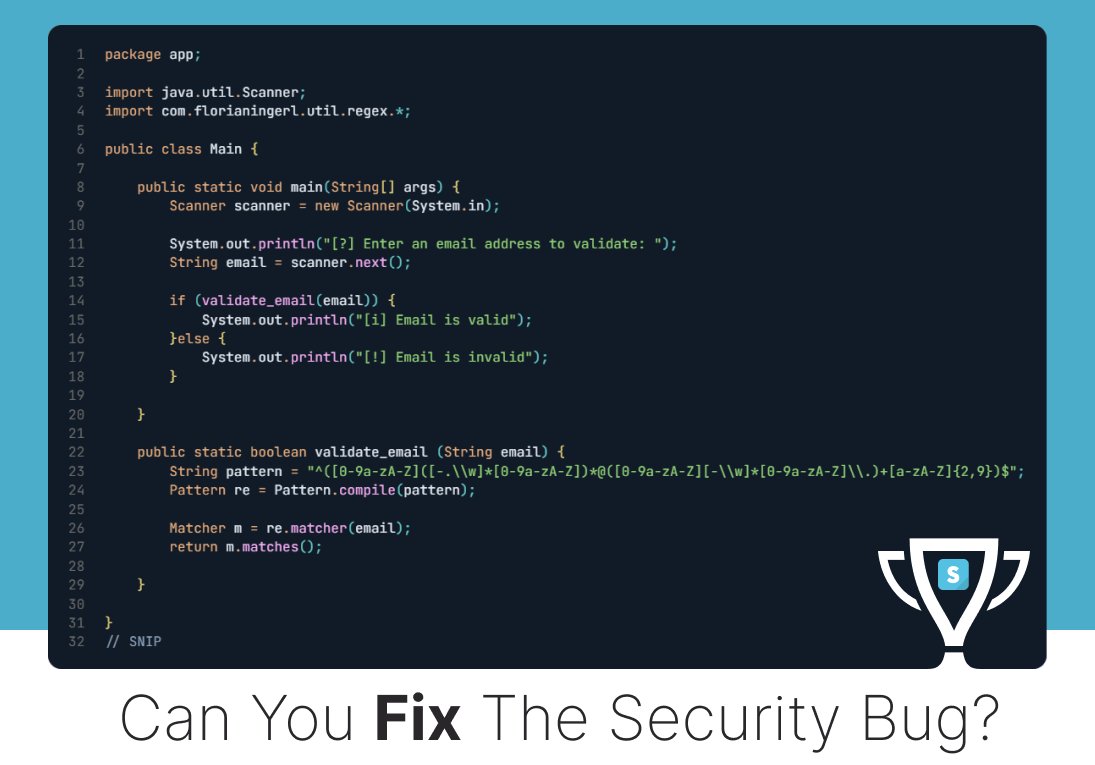
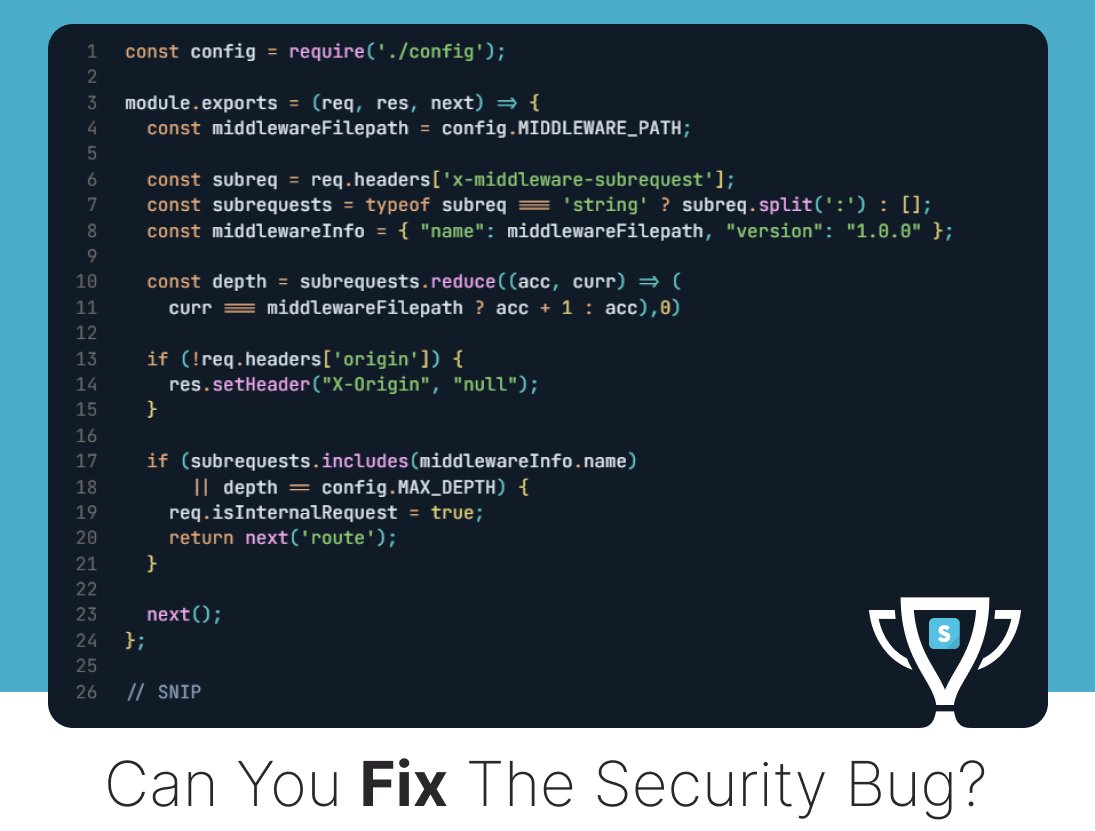
In August 2019, Felix aka [xi-tauw] & Matt Nelson reported a privilege escalation vuln in Valve's Steam client for Windows that allows arbitrary code execution with maximum system privileges. We made a challenge for this; can you fix it? 👉 bit.ly/secdimcashedup #appsec #programming
![SecDim (@secdim) on Twitter photo In August 2019, <a href="/PsiDragon/">Felix aka [xi-tauw]</a> & <a href="/enigma0x3/">Matt Nelson</a> reported a privilege escalation vuln in Valve's Steam client for Windows that allows arbitrary code execution with maximum system privileges.
We made a challenge for this; can you fix it?
👉 bit.ly/secdimcashedup
#appsec #programming In August 2019, <a href="/PsiDragon/">Felix aka [xi-tauw]</a> & <a href="/enigma0x3/">Matt Nelson</a> reported a privilege escalation vuln in Valve's Steam client for Windows that allows arbitrary code execution with maximum system privileges.
We made a challenge for this; can you fix it?
👉 bit.ly/secdimcashedup
#appsec #programming](https://pbs.twimg.com/media/Gon4tclWMAAmAog.jpg)











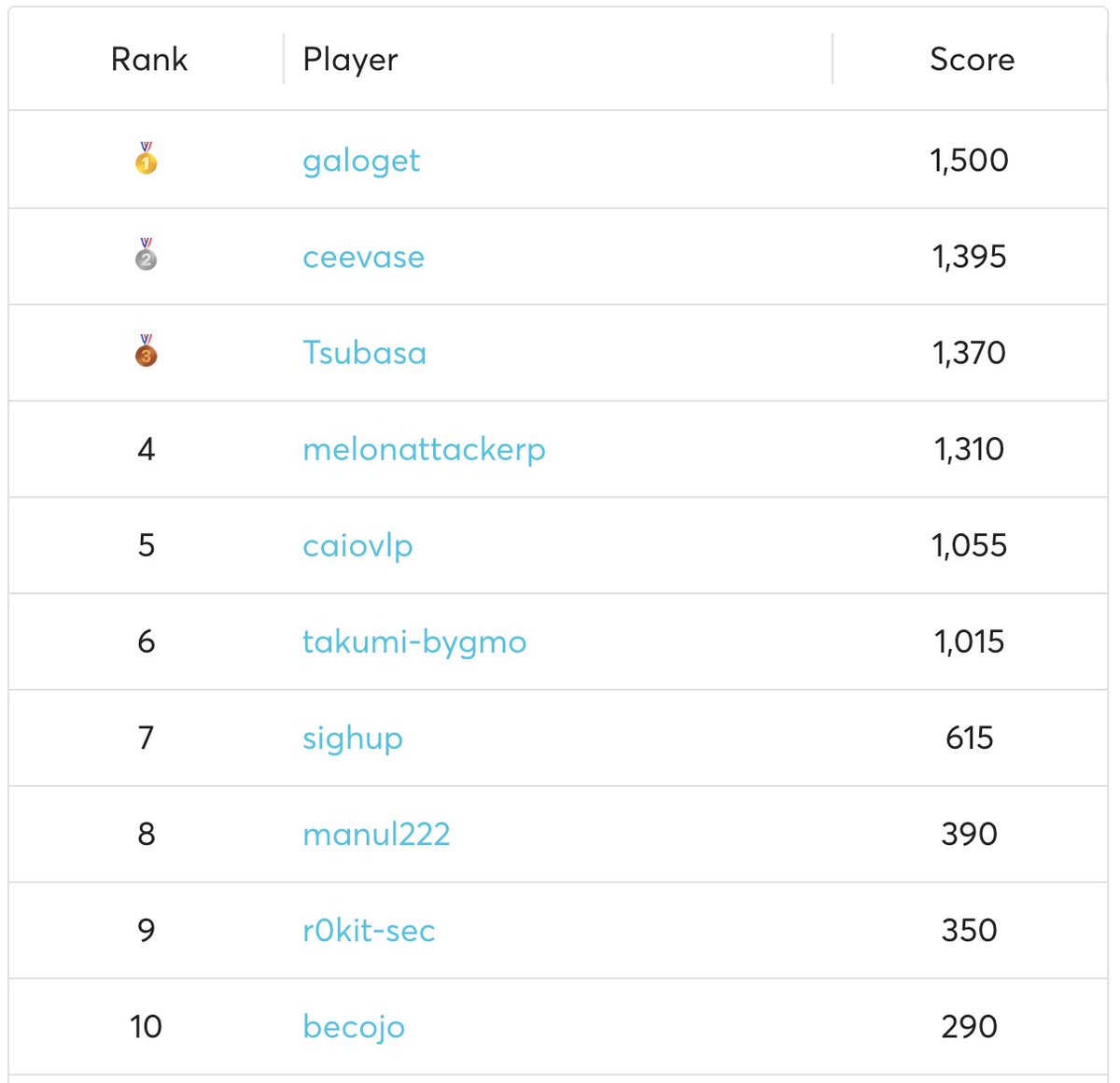
Congratulations to Galoget for a 1st place finish at AppSec Village Fix the Flag competition at DEF CON 33 🏆 Honorable mention to Ceevase for being the Runner up. Shout out to zi0Black and @[email protected] for being the Challenge Contribution Winners 🧱 #appsec #programming #ctf