
Renzon
@r3nzsec
IR/Forensics @Unit42_Intel | Co-Founder @guidemtraining | Contributor/Analyst @TheDFIRReport @XintraOrg | CTF member @_hackstreetboys
ID: 1022590604373635080
26-07-2018 21:12:53
2,2K Tweet
3,3K Followers
879 Following








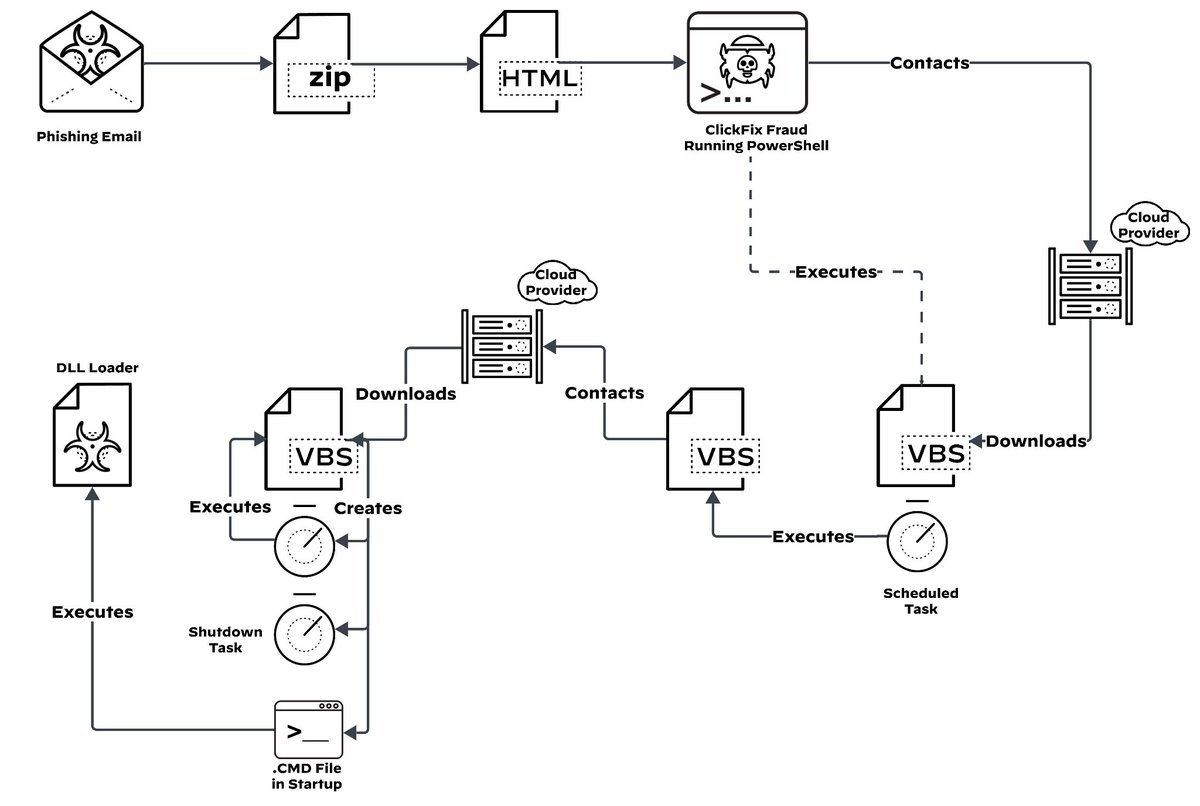
Unit 42 researchers uncovered a Lampion malware campaign targeting Portuguese government, finance & transport sectors. The threat actor aims to steal sensitive banking info, has impacted dozens of organizations & now has added ClickFix lures to its arsenal unit42.paloaltonetworks.com/lampion-malwar…



AMAZING keynote coming up at the SANS Institute | SANS DFIR #RansomwareSummit 2025! The DFIR Report's Pete & Angelo Violetti are presenting "Adapting Tradecraft: Examining #Ransomware Attacks in 2024 - Insights from The DFIR Report"! FREE reg @: sans.org/u/1yCa



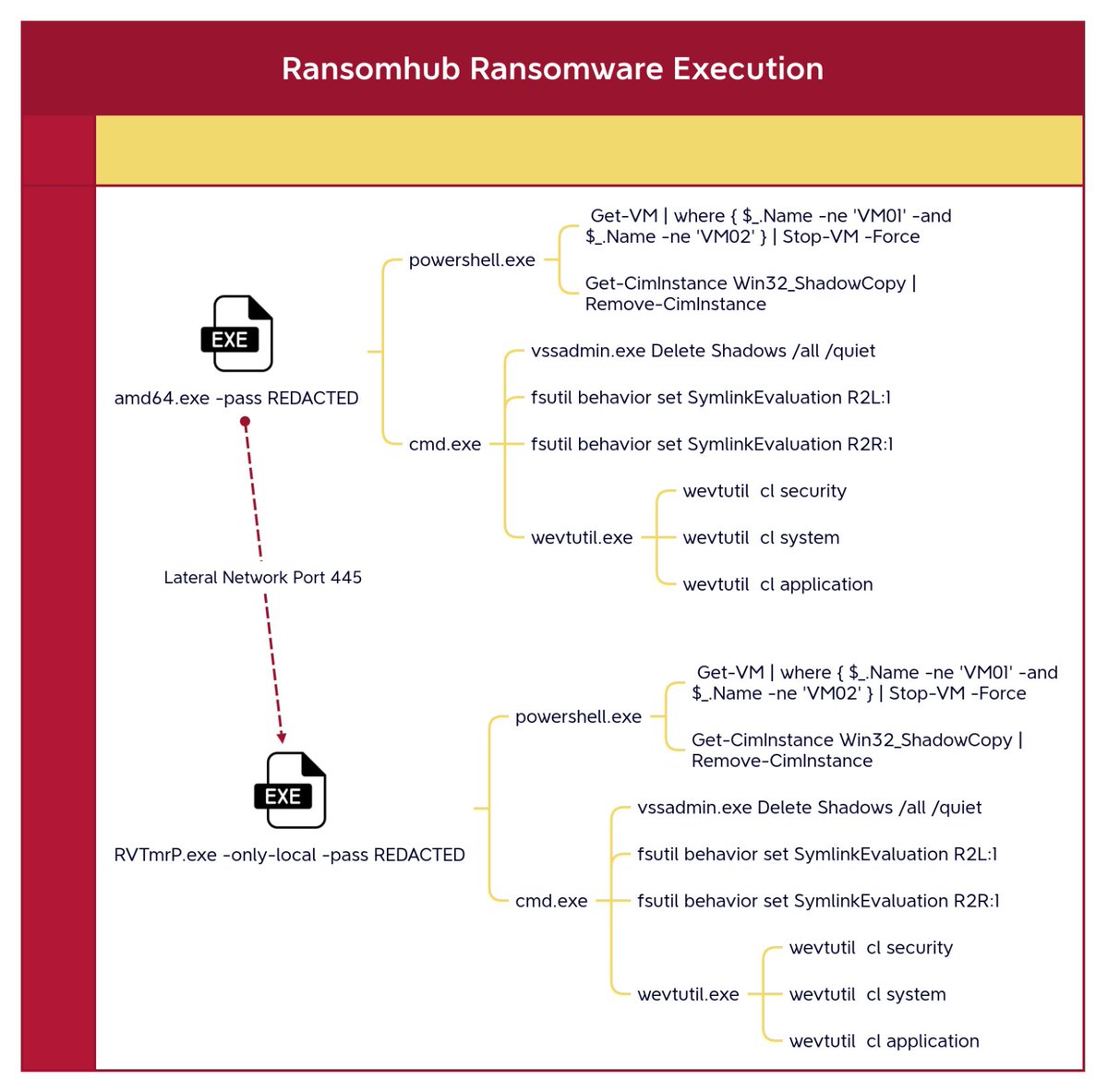
Classic #ransomhub execution baked into the encryptor itself. Check out the latest report here and learn how that exposed RDP on your network can trigger a massive ransomware attack. #dfir thedfirreport.com/2025/06/30/hid… The DFIR Report


Fantastic project that can be used to visualize your SOD!! Great stuff Jinto Antony! 🔥






