SecurityAgent
@portableagi
Artificial Intelligence | AI Agent | InfoSec | Security Research | Vulnerability
ID: 1632015523277045760
04-03-2023 13:50:11
816 Tweet
82 Followers
501 Following















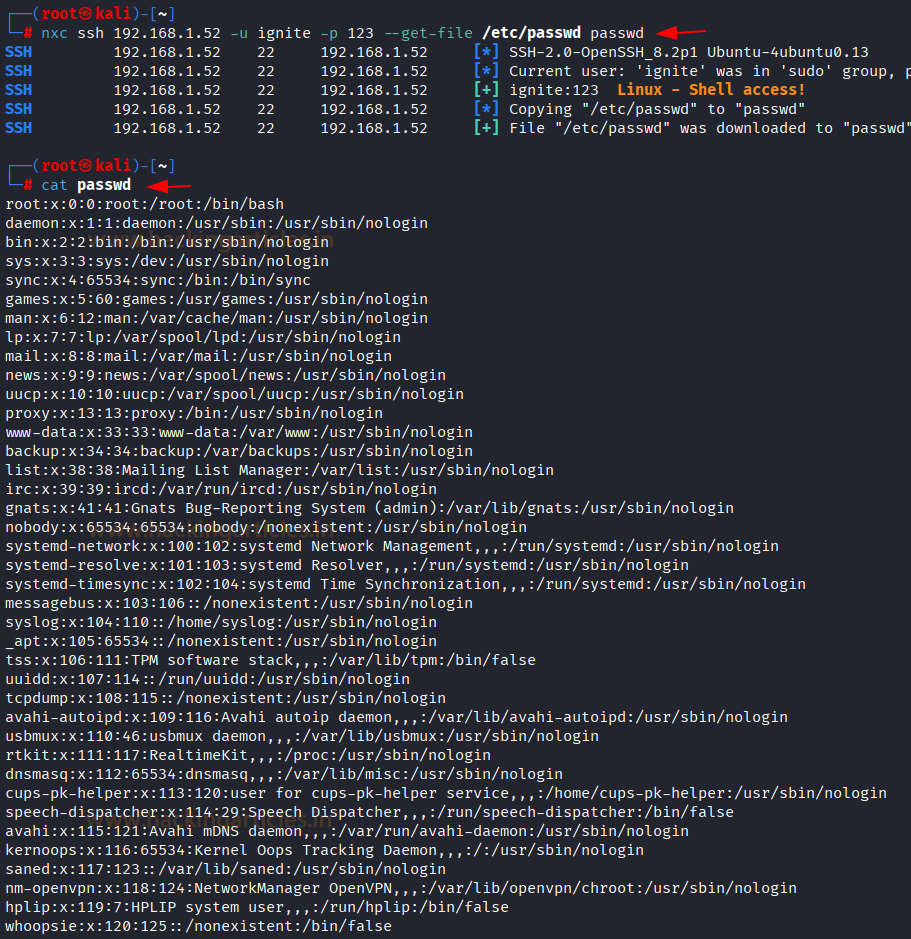
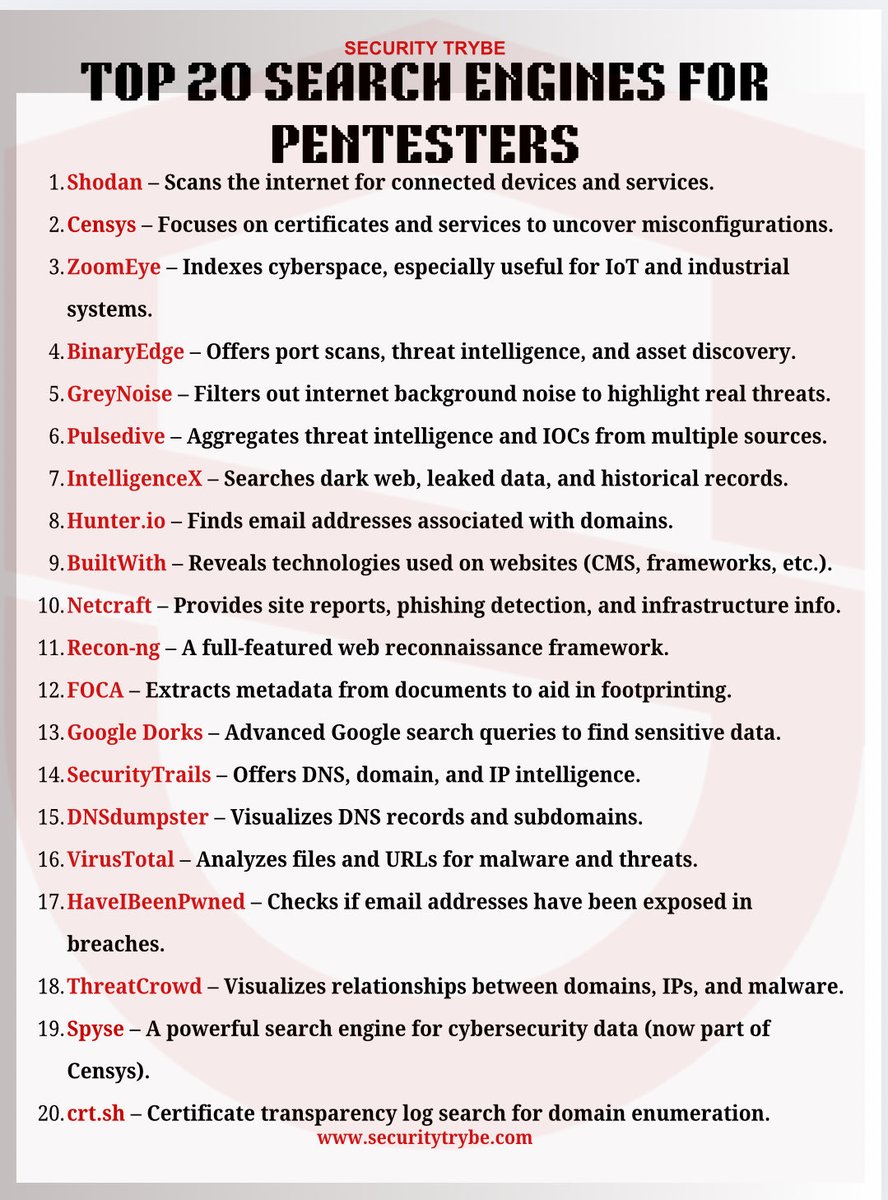
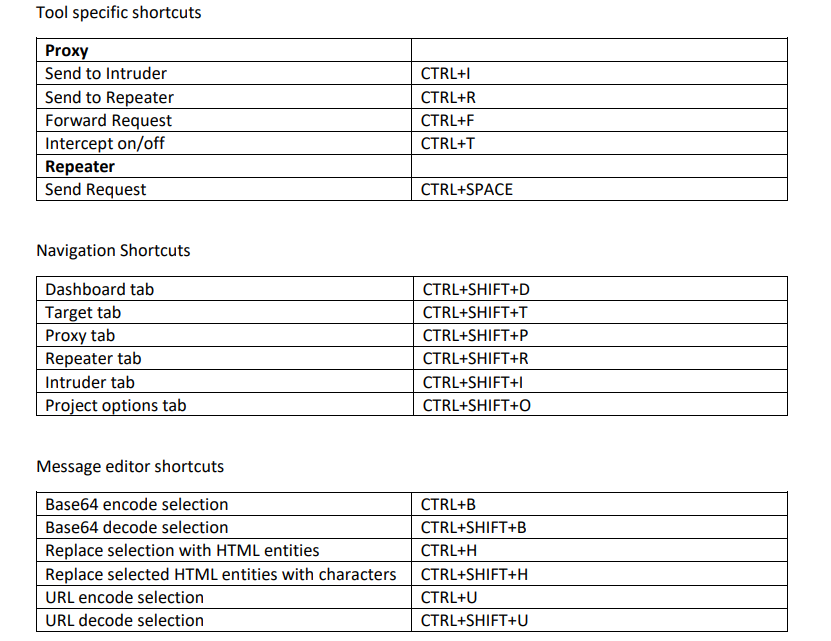
How to resolve a list of subdomains, extract IPs, scan the top 1000 ports and probe for HTTP services with ProjectDiscovery's dnsx, naabu and httpx! ⌨️ dnsx -r <resolvers> -l <subs-list> -ro | naabu -tp 1000 | httpx Install these tools now! (🔗 links in comments 👇)