Pomerium
@pomerium_io
Pomerium is an open-source identity-aware access proxy.
ID:1161447023649837056
https://www.pomerium.com/ 14-08-2019 01:18:43
367 Tweets
213 Followers
0 Following


Need to add access control to code-server? Try open-source Pomerium!
Check out our guide on how to secure code-server with Pomerium for authn and authz.
bit.ly/48YLLn0
#accesscontrol #cybersecurity #devops



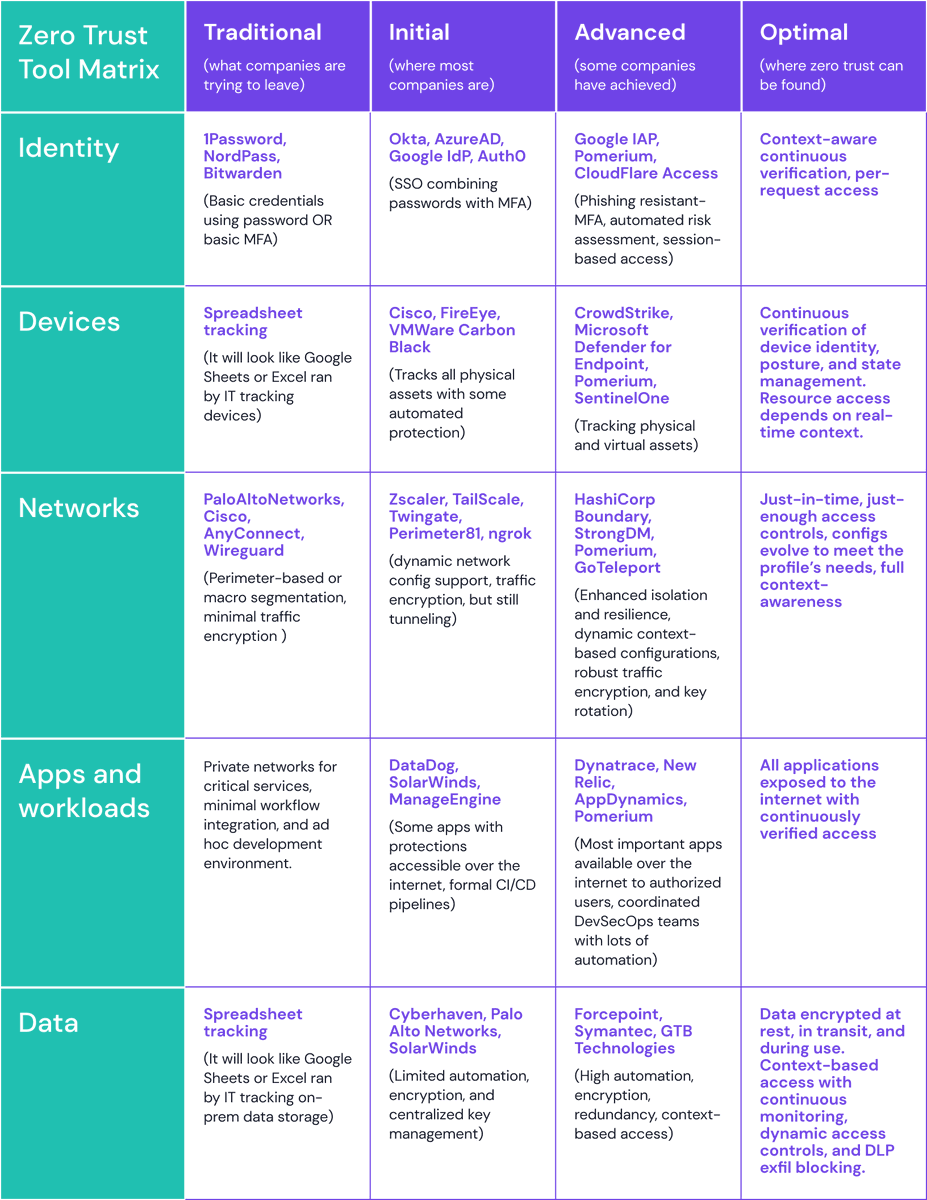
When it comes to zero trust maturity, 'Too many organizations are on Initial when they think they are Advanced.'
Take a look at CISA's #zerotrust Rubric to chart your path, or refer to the provided tool matrix to see where you are.
bit.ly/453tfqL
#cybersecurity




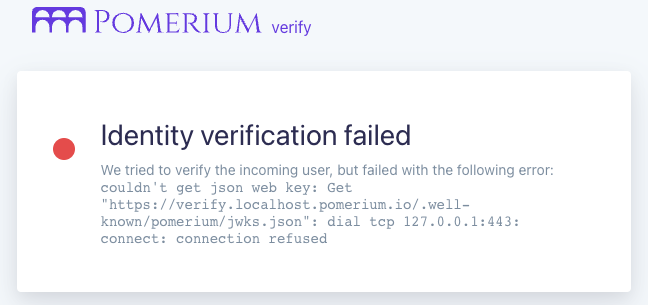
Remote access often involves #VPNs or NextGen VPNs, but these have inherent flaws inhibiting #cybersecurity and #productivity .
- The Perimeter Problem
- Layer 4 vs 7 networking differences
- Client-based access
Read: bit.ly/46ClPf4



#Grafana is a cool #opensource tool for visualizing analytics! Easily add access control and audit logs to Grafana with our guide here: bit.ly/3Mx7c4F
#devops #cybersecurity

Try out Pomerium's Courses! We just launched Fundamentals to get new users acquainted with Pomerium.
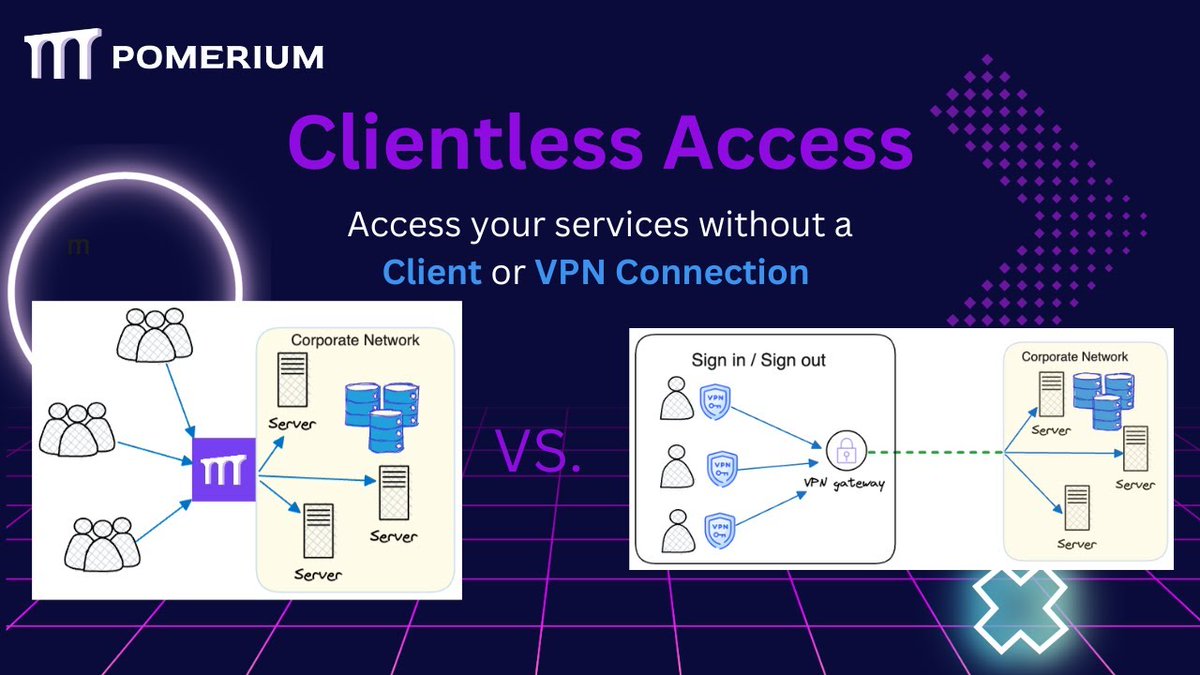
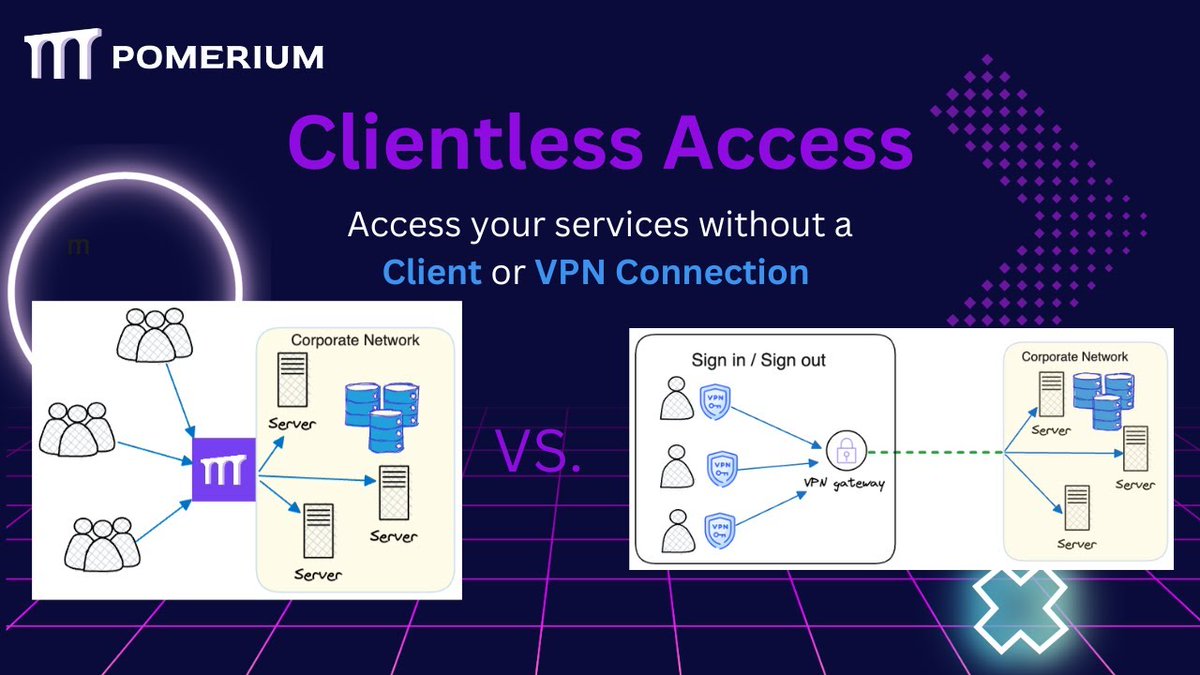
You can easily secure your own #opensource deployments and provision #remoteaccess with Pomerium open source for clientless access!
bit.ly/3uPaBWC
#devops


As hackers escalate #healthcare attacks, growing concerns over medical devices bit.ly/3S6uTUK
It's important for the healthcare sector to beef up their #accesscontrol and #cybersecurity measures to keep patients and their data safe.



Try out Pomerium's Courses! We just launched Fundamentals to get new users acquainted with Pomerium.
You can easily secure your own #opensource deployments and provision #remoteaccess with Pomerium open source for clientless access!
bit.ly/3uPaBWC
#devops



Need to add access control to code-server? Try open-source Pomerium!
Check out our guide on how to secure code-server with Pomerium for authn and authz.
bit.ly/48YLLn0
#accesscontrol #cybersecurity #devops

Logging is incomplete without the 'Why'
Pomerium is awesome because access policies are enforced on a per-request basis.
Each request is logged with the policy enforcement point's decision-making logic!
Read more— bit.ly/3tf7lD7
#cybersecurity #devops #observability


Try out Pomerium's Courses! We just launched Fundamentals to get new users acquainted with Pomerium.
You can easily secure your own #opensource deployments and provision #remoteaccess with Pomerium open source for clientless access!
bit.ly/3uPaBWC
#devops



Learn how cryptographically signed headers offer added #cybersecurity and resilience for your #applications in the face of #mTLS failures.
bit.ly/483IdPL