The Cyber Bro
@password_ng
Cyber | Security Operations & Engineering. coordinating @ngwhitehat, building @cyberplural.
ID: 287686022
25-04-2011 13:50:56
4,4K Tweet
1,1K Followers
107 Following









LLMs and Agents offer a powerful combination for driving automation. In our new #blog, ☠️ Brandon outlines how he harnesses the power of #angenticAI to autonomously map a network. Read it now! trustedsec.odoo.com/r/7d0







“The Heart of every Incident: Incident Coordination” by Moritz Oettle (@moettle.bsky.social) dfir-delight.de/p/incident-coo…



I jumped heavily into learning about SCCM tradecraft and wrote a detailed write-up with custom examples, covering the most interesting vulnerabilities that combine commonality and impact from low-privilege contexts, and what you can do to prevent them :) logan-goins.com/2025-04-25-scc…


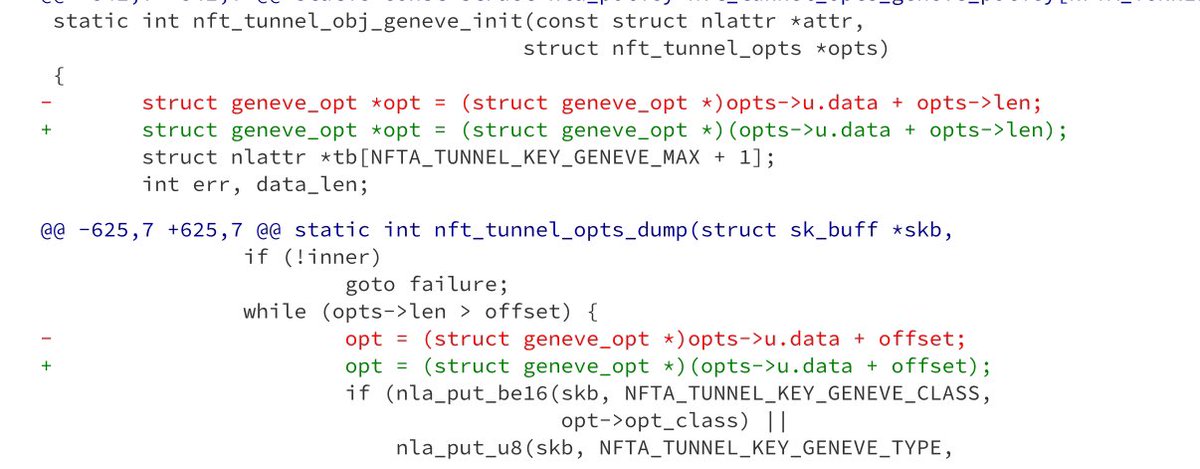
![Stephan Berger (@malmoeb) on Twitter photo We talked about infected USB sticks before [1]. The EDR on a customer site picked up malicious behavior, including the commands:
cmd.exe /c ""D:\rootdir\x943368.bat"
and
xcopy "C:\Windows\System32\printui.exe" "C:\Windows \System32" /Y
This behavior aligns with the tactics We talked about infected USB sticks before [1]. The EDR on a customer site picked up malicious behavior, including the commands:
cmd.exe /c ""D:\rootdir\x943368.bat"
and
xcopy "C:\Windows\System32\printui.exe" "C:\Windows \System32" /Y
This behavior aligns with the tactics](https://pbs.twimg.com/media/Gks-1fBWUAAMaSh.png)