Nimrod Aviram
@nimrodaviram
TAU PhD student. Recently worked on DROWN: drownattack.com
ID: 3030979488
19-02-2015 18:08:31
218 Tweet
233 Followers
398 Following


"The 9 Lives of Bleichenbacher's CAT:New Cache ATtacks on TLS Implementations ", with Robert Gillham, Daniel Genkin, Adi Shamir, David Wong and Yuval Yarom is now available at cat.eyalro.net


Reporting the OpenSSL bug would not be possible without Colm MacCárthaigh and his colleagues. We just reported an invalid behavior, they performed all the hard analyses. Unfortunately, not all security teams are so collaborative...

Together with Tibor Jäger and Kai Gellert, we propose a few mechanisms to make TLS 1.3 0-RTT more efficient in storage. Kai will also present our work at IACR Eurocrypt

My TLS CBC padding oracle scanner source code is now available: github.com/Tripwire/padch… (Dockerfile included) Full details about Zombie POODLE and GOLDENDOODLE are now on z3n hunter blog: tripwire.com/state-of-secur… Thank you for everyone who joined me at #BHASIA



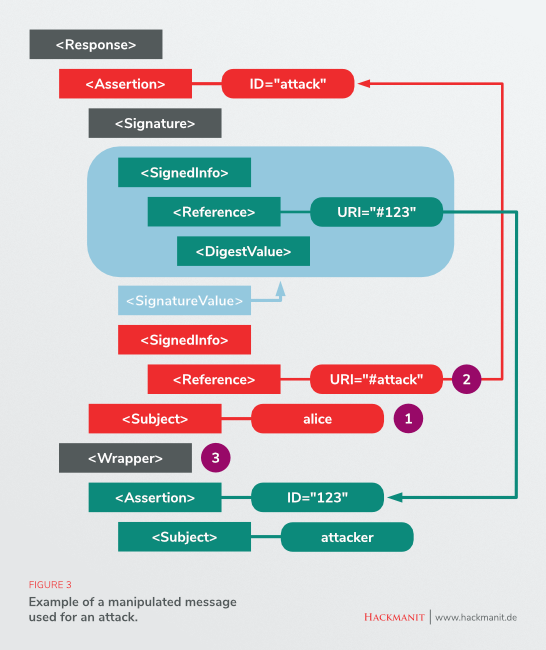
New paper: “'Johnny, you are fired!' – Spoofing OpenPGP and S/MIME Signatures in Emails" to appear USENIX Security '19. Joint work with Jens Müller - Damian Poddebniak hanno juraj somorovsky Jörg Schwenk github.com/RUB-NDS/Johnny…


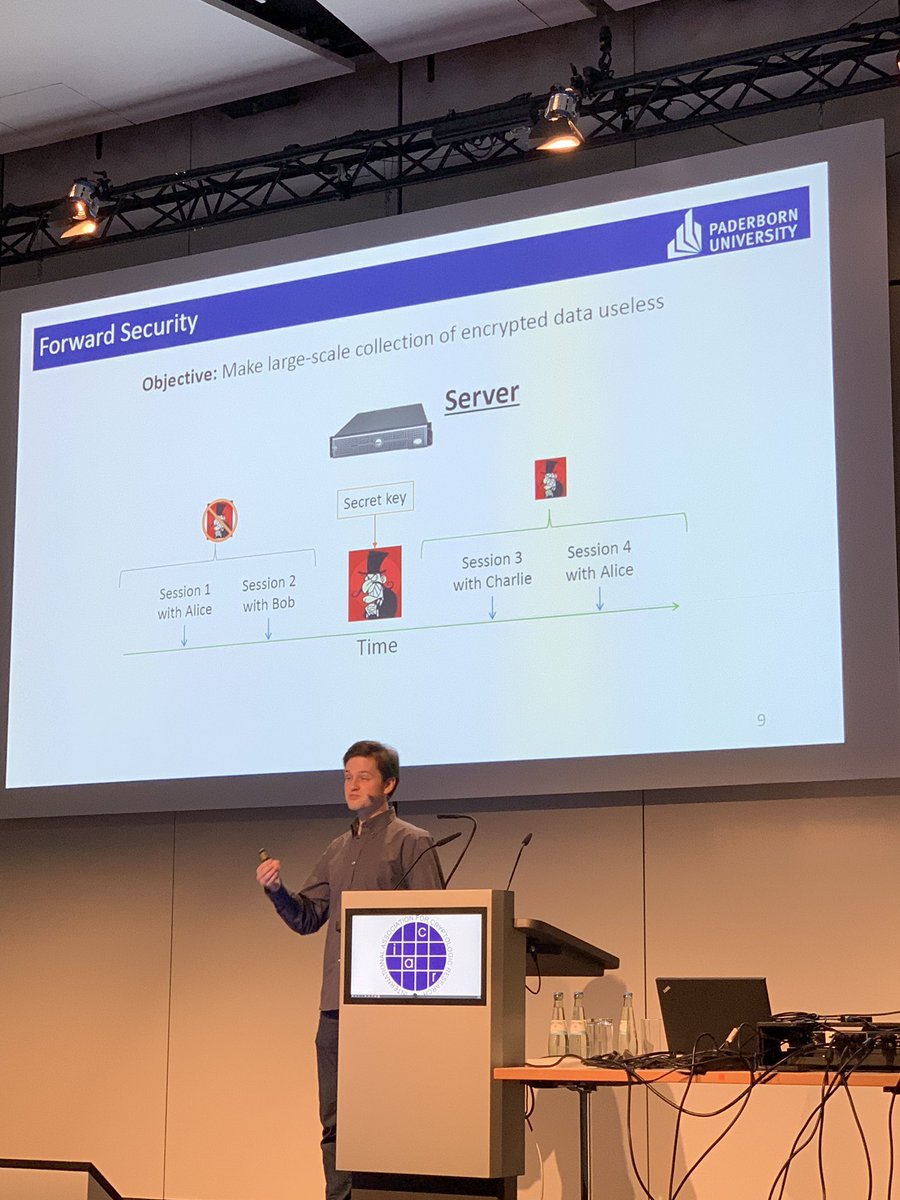
Kai Gellert talking about our results on forward security in TLS 1.3 0-RTT at #eurocrypt2019. Joint work with Nimrod Aviram

We just put our paper on Scalable Scanning and Automatic Classification of TLS Padding Oracle Vulnerabilities online: github.com/RUB-NDS/TLS-Pa… // @ic0nz1, Nimrod Aviram I will present our results in the next session of the Crypto Summer School: summerschool-croatia.cs.ru.nl/2019/program.s…

The Pwnie Awards winners for the best crypto attack this year are Mathy Vanhoef and Eyal Ronen with their Dragonblood: eprint.iacr.org/2019/383.pdf ...well deserved, congratulations :)

New Paper: “Practical Decryption exFiltration: Breaking PDF Encryption“ describing new attacks that uncover the plaintext of encrypted PDFs. To be presented at ACM CCS 2025 and joint work with Jens Müller Fabian @[email protected] vladislav mladenov Christian Jörg Schwenk. #PDFex 1/n


thaddeus e. grugq Matthew Green is on BlueSky Child exploitation is "icky" and men in suits don't feel comfortable discussing it. They don't like planning ops against it. Everybody wants to "smash the perverts," but doing it correctly would require actual time investment in a very dark world.