Saullo Carvalho
@n0ps13d
Computer Engineer, MSc | Mobile, Web and Cloud Security | Pwning and RE | GXPN OSCP eCXD OSWE OSED | Opinions are my own, not my employer's
ID: 319829802
https://github.com/saullocarvalho 18-06-2011 20:30:54
1,1K Tweet
315 Followers
444 Following

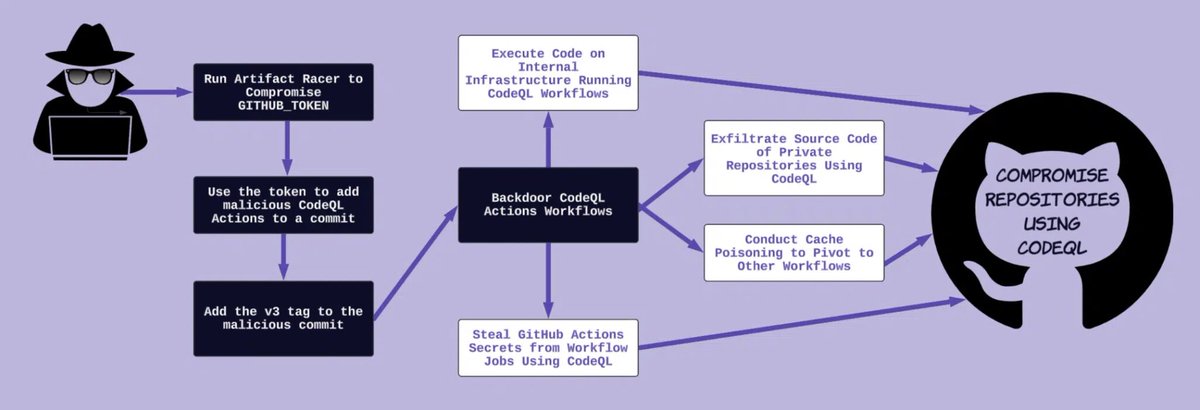
👿 Compromising (almost) every repo using CodeQL A supply chain attack on CodeQL using a publicly exposed secret valid for 1.022 seconds at a time. Praetorian’s (Praetorian) John Stawinski discovered a supply chain issue affecting GitHub CodeQL that allowed executing code






Skills can be taught. Tools change. Principles? That's what holds Praetorian together. Our culture is built on this foundation. Learn how being guardians of talent guides everything we do: rb.gy/0q5l0s #PraetorianLife