
mrglwglwgl
@mrglwglwgl
Enjoy Malware
ID: 1744161848583507968
08-01-2024 00:59:38
84 Tweet
56 Followers
90 Following






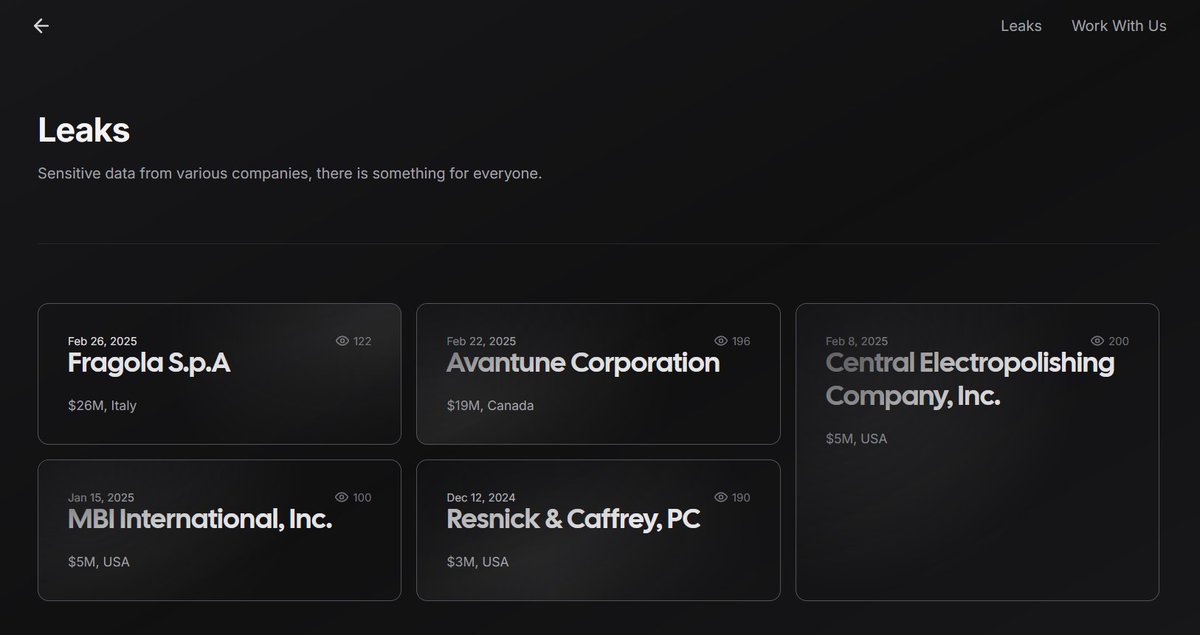
🚨FOUND REAL IPs of #Weyhro #Ransomware! DLS: …75gfvi47fptm2gftw7cn656rnfhzdqd.onion File Server: …5p7wgaegtfh4cobeqbhcq55nwt2m6yd.onion 194.87.85.168 🇳🇱 185.106.94.255 🇦🇹 More: github.com/TheRavenFile/D… #infosec #security #malware #OSINT #cybersecurity #threatintel #russia #CISA #darkweb #TOR FOFA








.3so Ransomware extension: .3so md5: 56a261f75d8470e3ab3b41ca2966894f TG: @joedecryption mail: [email protected]


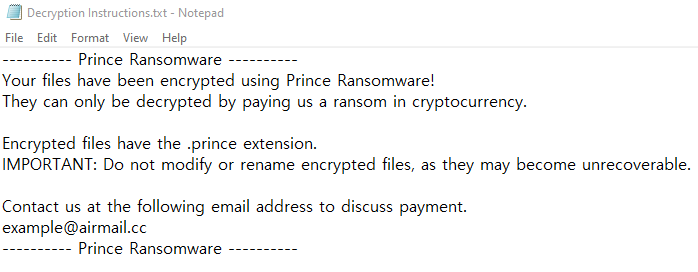
Prince Ransomware IS IT TEST SAMPLE? ext: .Rans note: Decryption Instructions.txt mail: [email protected] md5: 3e6897a84bbbe0e918006d7fc5bca849



![mrglwglwgl (@mrglwglwgl) on Twitter photo Banderas Ransomware
.crypt
instructions.txt
c0c59aadd4431da20e79a174f1bc1099f24d1b8627571e5afd43a8a4c2ea92fa
http://50.85.82[.]218:8080/Banderas.exe Banderas Ransomware
.crypt
instructions.txt
c0c59aadd4431da20e79a174f1bc1099f24d1b8627571e5afd43a8a4c2ea92fa
http://50.85.82[.]218:8080/Banderas.exe](https://pbs.twimg.com/media/Gj-QKvGaIAAQ42F.png)
![Hyuna Lee (@paducklee) on Twitter photo 185.39.18[.]56
bcfa1892e328cc8f63a45d71c739d64f
ccde96059c24675add801c44548ace17
3d816cbc13e4ad4d00ae467b2025f5d5
a29c37ff774d57230eda3a2e31777d30
3b7f6f2d95067837287941c21194bb04
d197dd2bb854f3cd9856ccdb73889efa 185.39.18[.]56
bcfa1892e328cc8f63a45d71c739d64f
ccde96059c24675add801c44548ace17
3d816cbc13e4ad4d00ae467b2025f5d5
a29c37ff774d57230eda3a2e31777d30
3b7f6f2d95067837287941c21194bb04
d197dd2bb854f3cd9856ccdb73889efa](https://pbs.twimg.com/media/GkFHrJeaAAIscpz.jpg)
![Hyuna Lee (@paducklee) on Twitter photo J #Ransomware
md5 : d69ebd183b2e0072c396e55503d5ede7
onion : w4d5aqmdxkcsc2xwcz7w7jo6wdmvmakgy3y6mfmdtzmyvxe77cjkfbad[.]onion J #Ransomware
md5 : d69ebd183b2e0072c396e55503d5ede7
onion : w4d5aqmdxkcsc2xwcz7w7jo6wdmvmakgy3y6mfmdtzmyvxe77cjkfbad[.]onion](https://pbs.twimg.com/media/GlMuqjha8AAZiYp.png)

![mrglwglwgl (@mrglwglwgl) on Twitter photo DATACARRY DLS
dcarryhaih5oldidg3tbqwnde4lxljytnpvberrwgj2vlvunopd46dad[.]onion DATACARRY DLS
dcarryhaih5oldidg3tbqwnde4lxljytnpvberrwgj2vlvunopd46dad[.]onion](https://pbs.twimg.com/media/Grl0UcaWQAAXIbM.jpg)

![mrglwglwgl (@mrglwglwgl) on Twitter photo W.A. Locker
or..
W.A. Ransomware
README_iwzhu.txt
DLS: weepangrbqjfsxd2noz4bmolztnqsma3vw4c6qfnbfusadzd2m26emqd[.]onion W.A. Locker
or..
W.A. Ransomware
README_iwzhu.txt
DLS: weepangrbqjfsxd2noz4bmolztnqsma3vw4c6qfnbfusadzd2m26emqd[.]onion](https://pbs.twimg.com/media/GtCrTv0acAAPASV.png)


