Miroslav Legen
@mlegen
Malware Researcher @ ESET
ID: 87197485
03-11-2009 14:08:01
426 Tweet
578 Followers
681 Following


We have received a lot questions about the Silver Sparrow malware for macOS after a publication by Red Canary, a Zscaler company. #ESETresearch has investigated and found that, far from speculations about nation-state malware, it is likely related to adware and pay-per-install schemes. 1/10


... it against their spouses - not only is it unethical, it might also leak the victim’s private information and leave them at risk of #cyberattacks and #fraud. Join the talk of Lukas Stefanko today at #RSA2021 #ESETresearch 5/5




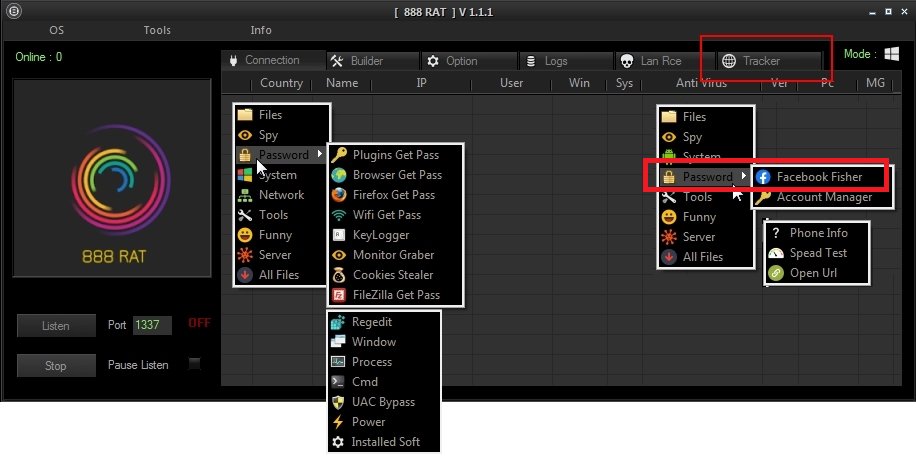
Analysis of Android espionage against Kurdish ethnic group using commercial 888 RAT that was distributed via dedicated Facebook profiles welivesecurity.com/2021/09/07/bla… ESET Research





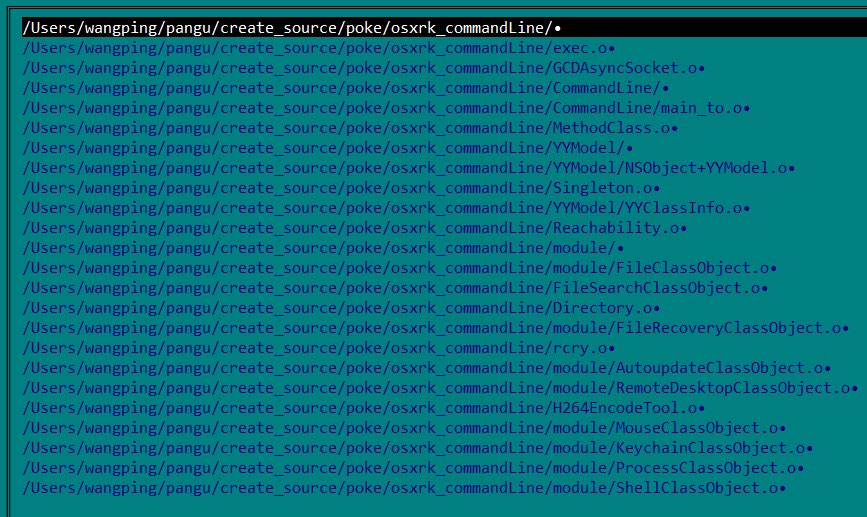
Short thread on "CloudMensis" (discovered by ESET Research / Marc-Etienne M.Léveillé) ...includes samples (☣️) & how Objective-See Foundation's free/open-source tools fair against this new threat!🛡





#Breaking #ESETresearch releases a paper about Ebury, among the most advanced server-side Linux malware, which was deployed to 400,000 servers over the course of 15 years, primarily for financial gain. Marc-Etienne M.Léveillé welivesecurity.com/en/eset-resear… 1/8