
markus neis
@markus_neis
Principal Threat Intelligence Researcher at Arctic Wolf Labs | Opinions are my own
ID:828625039864057856
06-02-2017 15:22:59
2,9K Tweets
2,8K Followers
1,3K Following

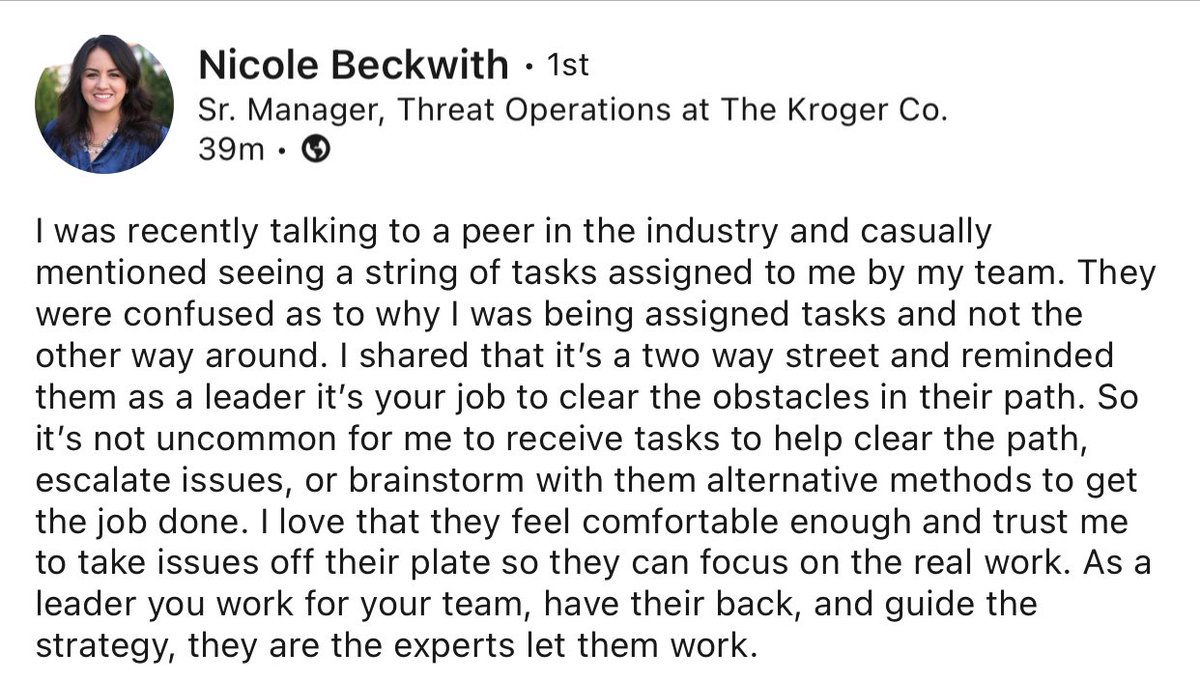
Banger from Just Another Nerd. I assign tasks to my leaders, and I encourage my team to assign tasks to me. It's actually a blessing, because that's one less thing I didn't have to write down. Also, management, leadership, and obstacle clearing is real work. 🫶🏼
Link to original




#100DaysofYARA
I created a web service that allows you to verify on which yara versions your rule compiles.
In the past, shipping rules to customers, I wondered if there were limitations but couldn't find out easily. Now I can.
yaravalidator.manalyzer.org





Frank Frank Boldewin created a neat #Yara workshop some time ago and released the materials this weekend. If you want to learn Yara (or know someone who does) - this is a very good place to start.
#threatintel #detectionengineering


In the blog, we detail malware dubbed 'SnappyTCP', a simple reverse shell for Linux/Unix systems:
pwc.com/gx/en/issues/c…
#threatintel #seaturtle #marbleddust #snappytcp



Interesting SANS post by @[email protected]: Exploiting #SharePoint CVE-2023-29357.
June MS releases patch▶️late Sept exploit released▶️via CVE-2023-24955 (patched in May).
Honeypots identify low threshold scanning 30th Sept but recent spike in activity...


Ongoing investigation into Qlik Sense Exploitation in Cactus Ransomware Campaign
arcticwolf.com/resources/blog…
Currently assessed to be related to CVE-2023-41266, CVE-2023-41265, and CVE-2023-48365 identified by Praetorian


MemProcFS-Analyzer v1.0 released with various enhancements. New checkboxes, 318 YARA rules for malware detection, improved hunting for suspicious scheduled tasks, Kroll RECmd Batch File v1.22, and much more. #MemProcFS #MemoryAnalysis #DFIR
github.com/evild3ad/MemPr…

Yara rules too slow? Not finding the needle in the APT haystack? Too many warnings or too many false positives? Turkey in the oven, got spare time? Join Vicente Diaz and myself tomorrow for cool yara tips and tricks, #Thanksgiving edition! brighttalk.com/webcast/18282/…



