Joshua Penny
@josh_penny
Senior Threat Intelligence Analyst @Bridewellsec
ID:469613879
http://bridewell.com 20-01-2012 19:57:21
539 Tweets
1,8K Followers
886 Following



YARA rule for Python #UPSTYLE Backdoor used in #0Day against Palo Alto Networks GlobalProtect VPNs
github.com/RustyNoob-619/…
Thanks to Germán Fernández for uploading sample to malware bazaar which enabled rule creation 🐧
Also, checkout YARA rules by Volexity here:
github.com/volexity/threa…


#100DaysofYARA Day85: Detecting Strela Stealer
github.com/RustyNoob-619/…
While I covered StrelaStealer in my previous YARA rule, this variant has a different Import Hash along with a couple of other properties
Link to previous rule: github.com/RustyNoob-619/…



Russian threat actor COLDRIVER/Callisto has recently been identified employing a new family of backdoor.
Here's some KQL to conducting proactive hunting for SPICA malware.
github.com/BloodshotCTI/K…
Bridewell
Joshua Penny
Yashraj Solanki
#SPICA #malware #threathunting


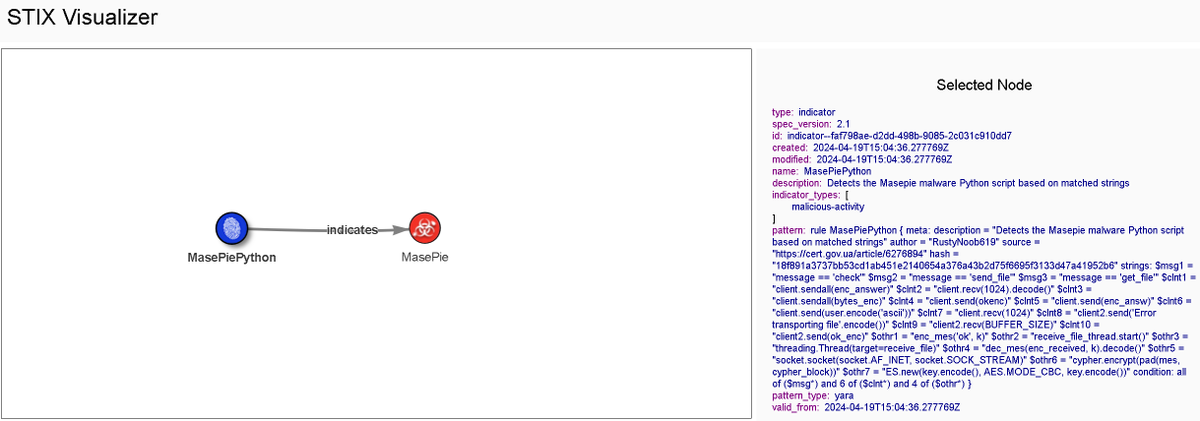
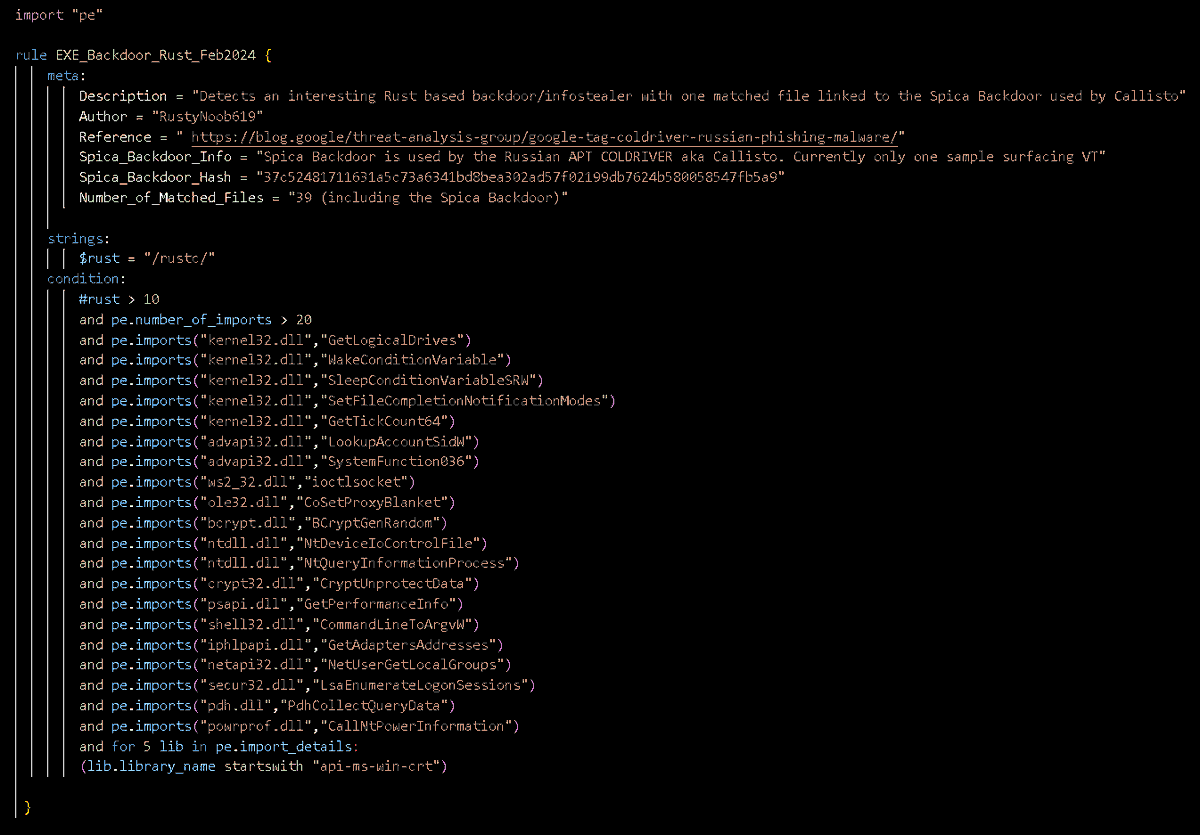
#100DaysofYARA Day79: An Interesting Rust Backdoor/Stealer
YARA rule matches on 39 files with one being Spica Backdoor Used by Russian APT COLDRIVER aka Callisto
Currently only one sample surfacing on VT🐧
Bridewell
Joshua Penny
Bloodshot_CTI
github.com/RustyNoob-619/…


Interesting loader disguised as CreateStudio Pro, dropping an obfuscated Python payload via PythonAnywhere 🐳
/download-createstudioo.com
/kingkh.pythonanywhere.com
↪️/kingkh.pythonanywhere.com/SRC/test.zip


Thrilled to share our latest CSIRT KNF report on #HookBot & #HookBuilder , where I contributed as a co-author!
📊 Diving deeper into the infrastructure and tools behind this Android malware.
📖A must-read for #cybersecurity enthusiasts: cebrf.knf.gov.pl/images/Hookbot…


🎯 Hunting #Grandoreiro Infrastructure (1st stage):
▪ Shodan: http.html_hash:1528083672 port:443 org:'Microsoft Corporation''
▪ Censys: services.http.response.body_hash='sha1:b6306fe94c164053882259f3d3105e6c4519bf81' and services.port=`443` and…



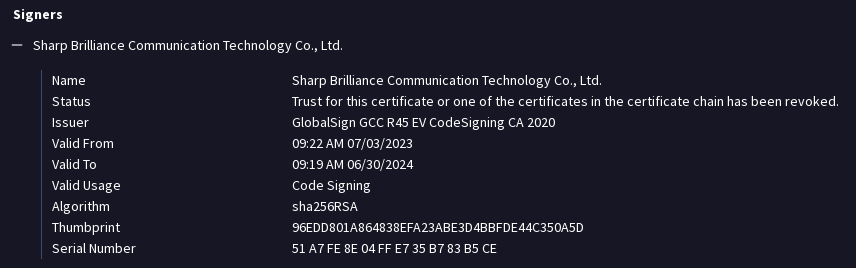
#100DaysofYARA Day34: Suspicious AnyDesk Impersonating software
Downloaded the latest AnyDesk software which has the latest code sign certificate. The loose rule detects software with any other cert thumbprint.
github.com/RustyNoob-619/…
Inspired by Florian Roth's YARA rule 🐧