Jack
@malwareforme
Security researcher
ID:3104962489
23-03-2015 14:28:29
1,1K Tweets
6,4K Followers
899 Following










How to become/continue to be a security researcher?
hexacorn.com/blog/2024/01/2…
h/t Dominik Penner


Microsoft researchers Jeremy Dallman, Steve Ginty, and Kimberly Ortiz discuss with Microsoft Threat Intelligence podcast host Sherrod DeGrippo 🦓 their insights on providing timely, accurate, and actionable threat intelligence. Listen to the episode here: msft.it/6011iqlUF

Steve YARA Synapse Miller If you’re into more historical stuff check out Zeus museum by tildedennis
zeusmuseum.com
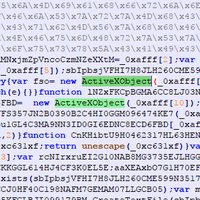

[1/5] In the spirit of #100DaysOfYara (Likely only posting today, as newborn should arrive any day now) and inspired from this post; I created a rule for one of my favorite Anti-Debug methods