Maldatabase
@maldatabase
Malware analysis. Threat intelligence. Data science.
Contact: [email protected]
ID: 947114278657712128
https://maldatabase.com 30-12-2017 14:36:55
2,2K Tweet
1,1K Takipçi
795 Takip Edilen








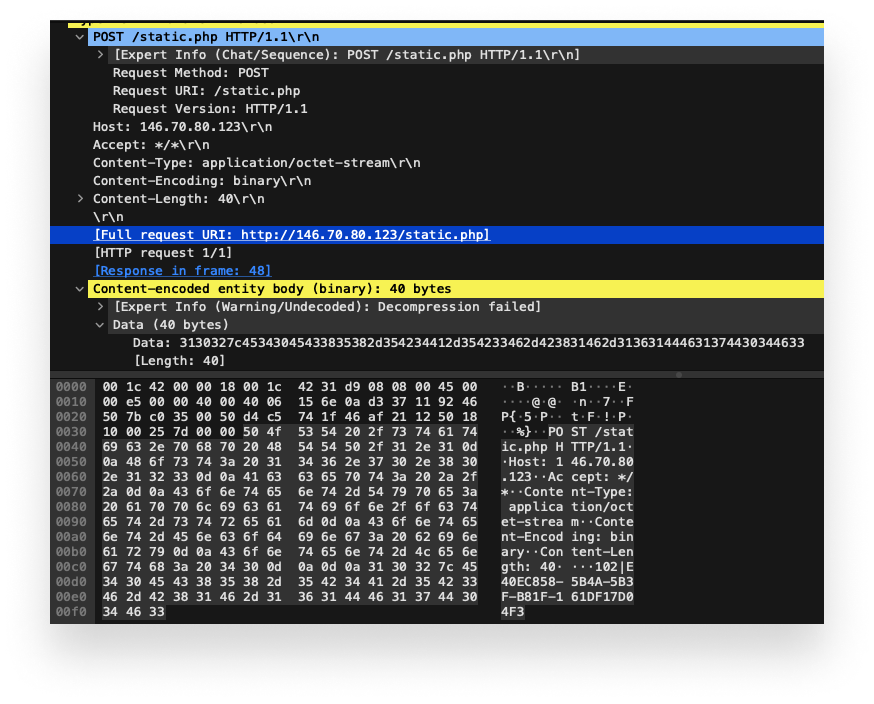
#Pikabot ddef0c551d3e5c1ec331bc4239db316a-Loader 56f1a42100754f98594ad8a282e8b648-injector #antidebug & geography region check etc. #malware #reversing #Cybersecurity #MaaS #ThreatIntelligence MalwareHunterTeam JAMESWT_MHT James Florian Roth ⚡️ bohops Michael Gillespie













![Leonid Bezvershenko (@bzvr_) on Twitter photo Magic is here! We have discovered a previously unknown #APT that has been attacking organizations in the area affected by the conflict between Russia and Ukraine. Observed victims were compromised with previously unknown implants that we dubbed #PowerMagic and #CommonMagic. [1/4] Magic is here! We have discovered a previously unknown #APT that has been attacking organizations in the area affected by the conflict between Russia and Ukraine. Observed victims were compromised with previously unknown implants that we dubbed #PowerMagic and #CommonMagic. [1/4]](https://pbs.twimg.com/media/FrupfUcXoAA2Vix.jpg)

![Unit 42 (@unit42_intel) on Twitter photo 2023-04-03 (Monday) - IoC update: A consistently reliable indicator of #Qakbot (#Qbot) over the past few years has been C2 traffic using TCP port 65400. Since 2021-09-20, this has occurred on 23.111.114[.]52. However, today Qakbot TCP port 65400 traffic switched to 172.107.98[.]3 2023-04-03 (Monday) - IoC update: A consistently reliable indicator of #Qakbot (#Qbot) over the past few years has been C2 traffic using TCP port 65400. Since 2021-09-20, this has occurred on 23.111.114[.]52. However, today Qakbot TCP port 65400 traffic switched to 172.107.98[.]3](https://pbs.twimg.com/media/Fs0mCoIWcAU-BTE.jpg)

![Unit 42 (@unit42_intel) on Twitter photo The Unit 42 Managed Threat Hunting team observed #Mythic being delivered by #Blister and #Socgholish (Socgholish → Blister → Mythic). Mythic using makethumbmoney[.]com on 104.243.33[.]129:443 for its C2 traffic. The Unit 42 Managed Threat Hunting team observed #Mythic being delivered by #Blister and #Socgholish (Socgholish → Blister → Mythic). Mythic using makethumbmoney[.]com on 104.243.33[.]129:443 for its C2 traffic.](https://pbs.twimg.com/media/F2DXhHaX0AEdVPV.png)