Lukas Stefanko
@lukasstefanko
Malware Researcher at @ESET
Android security, malware analysis, app vulnerability research
t.me/androidMalware
ID: 2936786110
http://welivesecurity.com/author/lstefanko 22-12-2014 10:23:40
3,3K Tweet
23,23K Followers
691 Following

Listen the latest #podcast hosted by Aryeh Goretsky {@infosec.exchange} where we talk about #EvilVideo vulnerability (CVE-2024-7014) that affected #Telegram for Android app and allowed attackers to send malicious files posing as videos Info: welivesecurity.com/en/podcasts/es… Podcast: esetresearch.podbean.com/e/evilvideo/

Check out the latest ESET Research podcast as Lukas Stefanko delves into EvilVideo exploit targeting Telegram’s Android users. Stay informed and protected. Listen now! 🎧 #ESET #ProgressProtected #CyberSecurity #ESETResearch #Telegram #Podcast #Android





It was great meeting some really cool folks like Lukas Stefanko , Joseliyo JaromirHorejsi and many others at AVAR Asia and presenting my research on "Rise & Fall of Golang Malware" !

Cybercriminals Use NFC Relay to Turn Stolen Credit Cards into Cash without a PIN : mobile-hacker.com/2024/12/02/cyb… credits Lukas Stefanko


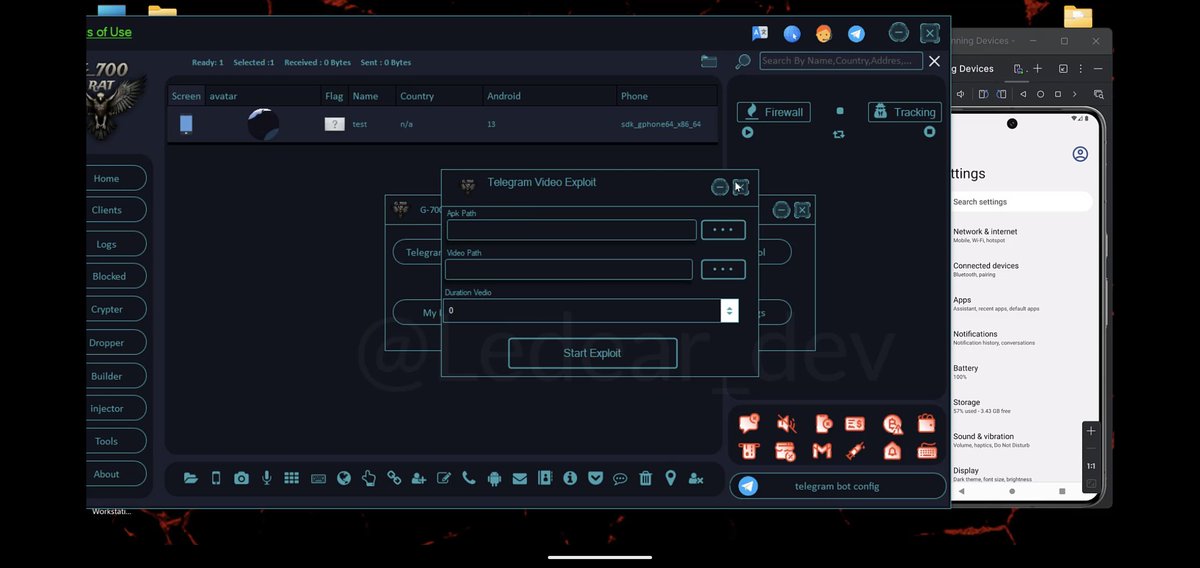
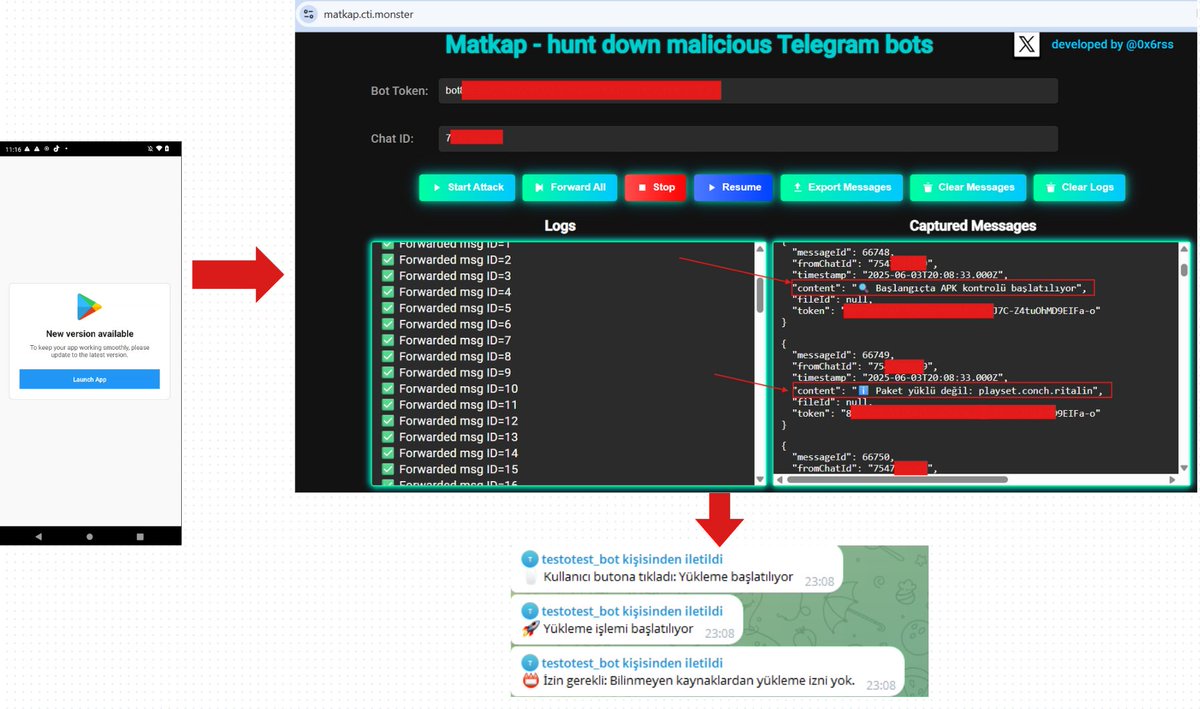
I hacked into the Telegram bot and retrieved all the logs😃. It seems that Spain🇪🇸 is being targeted. Who said what? 🫣 threat actor: ledear_dev sample: 9dc524efab35e8d79108fa8920119c6e Additionally, telegram vulnerability CVE-2024-7014 has already been fixed.


#BREAKING #ESETresearch NFC Android malware impersonates banking app in 🇵🇱 Poland. #NGate malware impersonates a banking verification application to steal NFC data and PIN from victims’ physical payment card. Lukas Stefanko 1/3





Lukas Stefanko explains why smartphones are the perfect target for digital spies. 🎙️ Listen to Unlocked 403 Podcast now on Spotify, or Apple Podcasts, and stay one step ahead of digital threats. ESET Research #Unlocked403

🔍 True or False? #AndroidMalware myths – busted! Cybersecurity expert Lukas Stefanko tackles rapid-fire questions to separate fact from fiction. Think you’re malware-savvy? Find out. Watch #Unlocked403 on YouTube, and listen on Spotify & Apple Podcasts. ESET Research