Kunal Mehta
@kmgkv1
System software and security engineer working @Intel, passionate for cyber security and platform security. Views expressed are my own, not my employer’s.
ID: 1041186962290302976
16-09-2018 04:48:10
313 Tweet
221 Takipçi
452 Takip Edilen


...Glad to see that my tool is used by PRO like David Weston (DWIZZZLE) ... and glad to see that we can introduce HVPT publicly finally :-)




Write up of the HVCI bypass vuln (CVE-2024-21305) with Andrea Allievi ! tandasat.github.io/blog/2024/01/1…
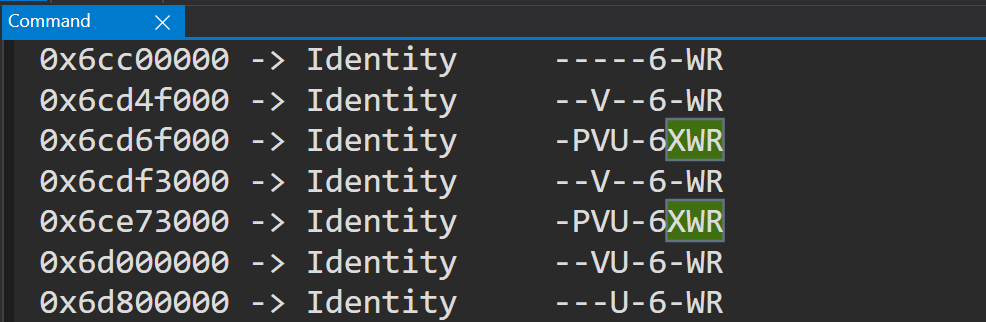


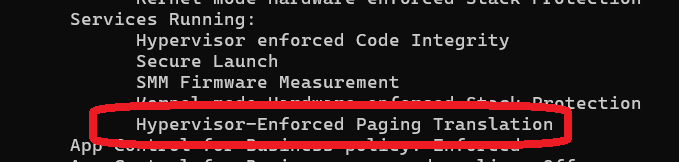
24H2 enables HVPT (VT-rp / HLAT) to prevent remapping attacks. You can check if it is enabled with msinfo32, systeminfo, or Andrea Allievi 's sktool v1.2+. Here is also sample code for that to save your time with reversing. gist.github.com/tandasat/890d4…





I created a hypervisor-based emulator for Windows x64 binaries. This project uses Windows Hypervisor Platform to build a virtualized user-mode environment, allowing syscalls and memory accesses to be logged or intercepted. elastic.co/security-labs/… Project: github.com/x86matthew/Win…