J Wolfgang Goerlich
@jwgoerlich
Advisory CISO with Cisco. I’m an unflinchingly optimistic greybeard in this cyber dystopia. Views expressed are my own. Reach me with my website’s contact form.
ID:35797450
https://jwgoerlich.com 27-04-2009 17:14:44
39,7K Tweets
50,1K Followers
37,6K Following
Follow People


We are thrilled to reveal that the keynote speakers at the 2024 Blue Hat IL are none other than — drumroll, please — the wonderful Sherrod DeGrippo 🦓 & J Wolfgang Goerlich!
Register now to hear them speak > microsoftrnd.co.il/bluehatil/home


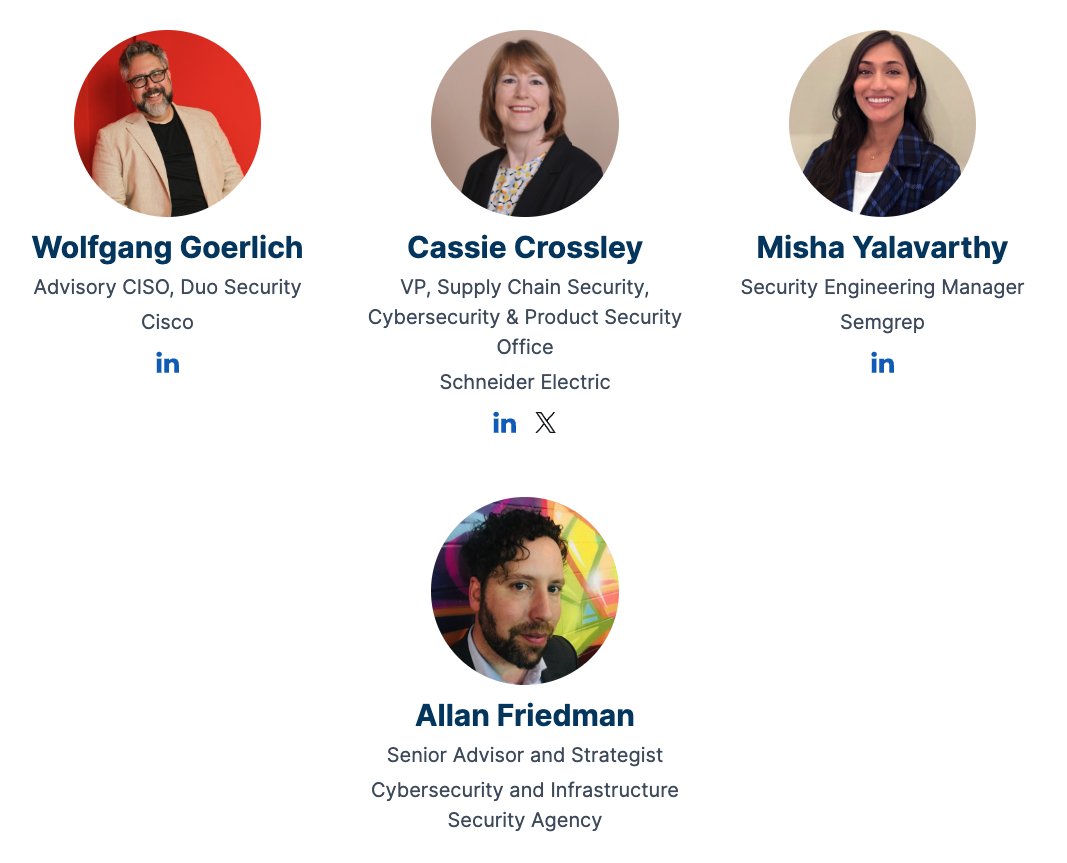
MUST-ATTEND: 'Software Supply Chain Security: More Than Just Dependencies' hosted by @Semgrep Community. 🚀 With guests: Cassie Crossley, Allan is @allanfriedman on bsky & infosec.exchange, J Wolfgang Goerlich, & host Misha Yalavarthy!
📅 April 25, 9:00 am Pacific
📍 ow.ly/VIep50QBrN8
#SupplyChainSecurity #AppSec

I don't know what reminded me of this but here it is. I am pretty sure it wasn't the Zero Trust webinar I just watched. J Wolfgang Goerlich said app authz was hard. The only authz we had for this was the door.



“We know that the password has long been the weakest factor — the easiest to crack, forget and lose.” Learn how #passwordless authentication supports #ZeroTrust from Duo Security advisory #CISO of J Wolfgang Goerlich ➡️ cs.co/6013nElYT

Just heard Dr. Stefani Goerlich, LMSW (she/her) ✡️ and Wolf on the Securing Sexuality podcast, discussing keyword-based controls to avoid use of #genAI to make non-consensual deepfakes. Filtering keywords is far too late: split training datasets and make separate models. 🧵
twitter.com/deFractal/stat…

I was thrilled to be on the Securing Sexuality Podcast with J Wolfgang Goerlich and Stefani Goerlich, LMSW (she/her) ✡️. We had a pile of fun talking about the types of challenges security practitioners and therapists share when it comes to protecting their clients. Check it out here!
securingsexuality.com/the-podcast/ep…

Authentication is more complicated than ever. Learn 4️⃣ ways to improve your #cybersecurity defenses from Duo Security advisory #CISO J Wolfgang Goerlich via ZDNET 💪 cs.co/6012TRzcy

Happening now! Excellent meeting with Wolf who is talking about Zero Trust in the real world.
J Wolfgang Goerlich

Dive into the world of #authentication with J Wolfgang Goerlich, Cisco advisory CISO. 🔐
Check out this ZDNET article to learn 4 tactical steps to boost your defenses and keep the #cyber tricksters at bay: cs.co/6013rcf9z.

clubhouse.com/room/6doSWNVYz…. Join us for an interview of J Wolfgang Goerlich at 2pm ET /11am CT (NOW)

Unlocking the Power of Zero Trust: Dive into the Security Outcomes Report by @JWGoerlich for a closer look at the evolving landscape. Discover the courage to forge ahead in cybersecurity.
oal.lu/668SL
#ZeroTrust #CybersecurityJourney #SecurityOutcomes

Without data, we’re just another CISO with an opinion. So I’m excited to share insights on Zero Trust, grounded in extensive data by Cyentia Institute .
Wondering where to start with Zero Trust? We’ve got you. Wondering what’s new? Yep, we got you too.
blogs.cisco.com/security/findi…

What happens when a group of hackers, cybersecurity professionals, and sexuality experts get together? sexandpsychology.com/blog/2023/11/1… Stefani Goerlich, LMSW (she/her) ✡️ Securing Sexuality

Talk title developed on the spot with J Wolfgang Goerlich and Michael Wareman - “Finding Satisfaction in a World of Proving Negatives”.
Abstract: How to find satisfaction in cybersecurity (or any job) where you only see and hear the failures and take for granted the successes.