JohnDCyber
@johndcyber
Senior Pentester, Cyber Security Instructor, Cloud Security Researcher and Blogger.
ID: 1394071433295417346
http://johndcyber.com 16-05-2021 23:25:19
59 Tweet
38 Followers
387 Following


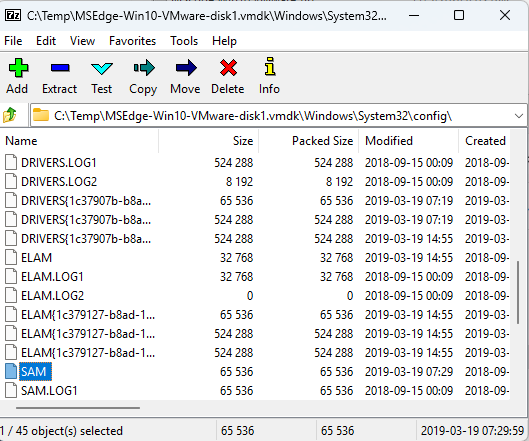
Malware Analysis series by zhassulan zhussupov Part 1 : cocomelonc.github.io/tutorial/2021/… Part 2 : cocomelonc.github.io/tutorial/2021/… Part 3 : cocomelonc.github.io/tutorial/2022/… Part 4 : cocomelonc.github.io/tutorial/2022/… Part 6 : cocomelonc.github.io/malware/2022/1… Part 7 : cocomelonc.github.io/malware/2023/0… Part 8 : cocomelonc.github.io/malware/2023/0…
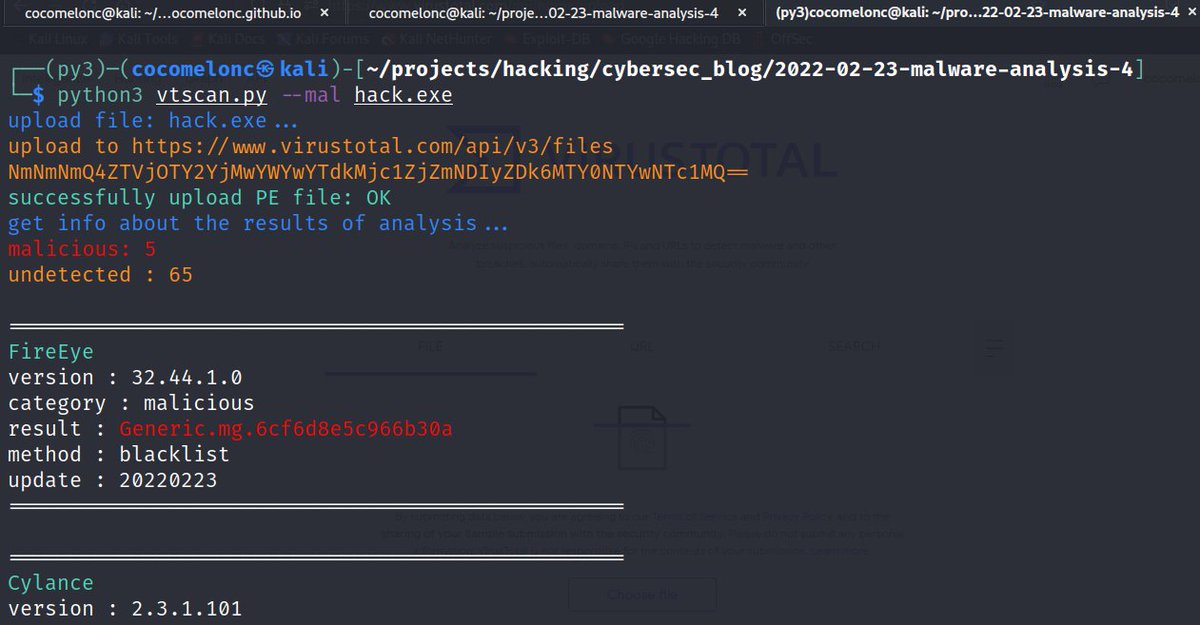



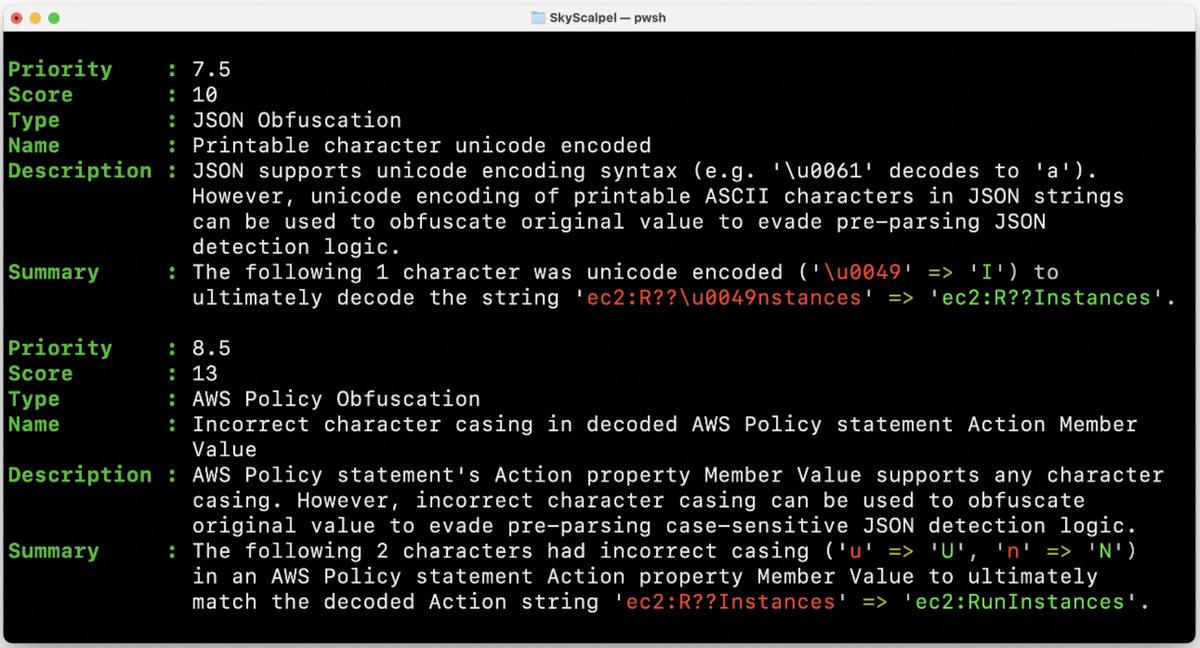
Two new open source cloud security tools from Permiso Security 🔪 SkyScalpel: Combat Policy Obfuscation in Cloud Environments permiso.io/blog/introduci… ☁️ CloudTail: Long-term Cloud Log Retention and Searchability permiso.io/blog/introduci…


Email Verification Bypasses ? Here are 10 Blogs about Email Verification Vulnerabilites ! 1. medium.com/@mohamed.yasse… 2. medium.com/@akrachliy/ema… 3. shrirangdiwakar.medium.com/how-i-turned-0… 4. mo9khu93r.medium.com/discovered-a-u… 5. medium.com/@mo9khu93r/how… 6. bevijaygupta.medium.com/email-verifica… 7.