John U
@jdu2600
He/him. Security Research Engineer @elasticseclabs
ID: 892839729884004352
https://github.com/jdu2600 02-08-2017 20:09:14
845 Tweet
617 Followers
346 Following

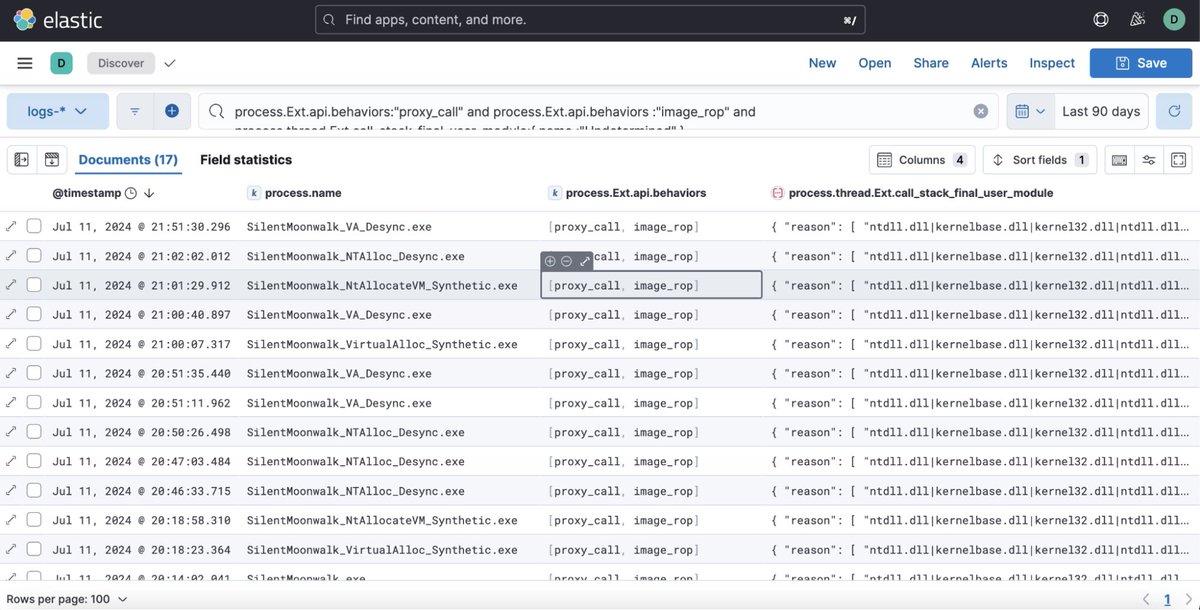
Quick question - Other than Sysmon and Elastic, which security products include call stacks in the telemetry they generate? William Burgess namazso mgeeky | Mariusz Banach klez Peter Winter-Smith thefLink 5pider Kyle Avery


It’s wonderful to see what Xeno Kovah and his collaborators have built for the community. I always recommend OST2 for my new hires and other juniors, or just anyone trying to get started on a new topic. The courses are excellent. It’s an honor to sponsor the Windows Security Path



Exciting news! I’m starting X-Force’s new offensive research team (XOR) and hiring a security researcher. Want to work with researchers (like b33f | 🇺🇦✊ and I) to find bugs, exploit popular targets, and share your work? Apply for this unique (remote) role 😊careers.ibm.com/job/21219320/s…




New blog from me on using CLR customizations to improve the OPSEC of your .NET execution harness. This includes a novel AMSI bypass that I identified in 2023. By taking control of CLR assembly loads, we can load assemblies from memory with no AMSI scan. securityintelligence.com/x-force/being-…

The Women In Security and Privacy (WISP) board is coming together to determine our top priorities for 2025 - YOU get to instruct us on what you would like those priorities to be! Need more scholarships, cons, exams/certs, mentors, events, or something else? Tell us your needs! docs.google.com/forms/u/4/d/e/…

Yarden Shafir (Yarden Shafir) is back for Offensivecon 2025 🤩 Sign up now to the Windows Internals Training. *Training tickets also guarantee first slots in the waiting list for conference tickets. offensivecon.org/trainings/2025…



ATT&CK never felt quite right to me. I originally thought it was just that the taxonomy was incomplete. Then Jared Atkinson framed my misgivings as a missing dimension and it just clicked.


David Weston (DWIZZZLE) Greg Linares (Laughing Mantis) Huntress We’ve been trying to join MVI for years, but don’t get accepted because we don’t delete malware from endpoints. Super frustrating. We’re deployed on over a million endpoints and want to stick to best practices.

An increased visibility into threads' call stacks helps with more reliable malware detection. The approach is based on ETW telemetry and module's Export Directory data for information enrichment. A post by John Uhlmann of Elastic Security Labs. Great read! #redteam #blueteam #maldev