👩🏻💻 Jane Scott 🇦🇺
@janescott
cybersecurity geek • python herder • vuln hunter • infosec sprite • molgen/biotech nerd • ex-sysadmin • she/her • opinions (most certainly) my own • ☕️🏃♀️🔑
ID: 466390179
https://twitter.com/JaneScott/timelines/1178607827931324417 17-01-2012 10:45:00
4,4K Tweet
3,3K Takipçi
366 Takip Edilen








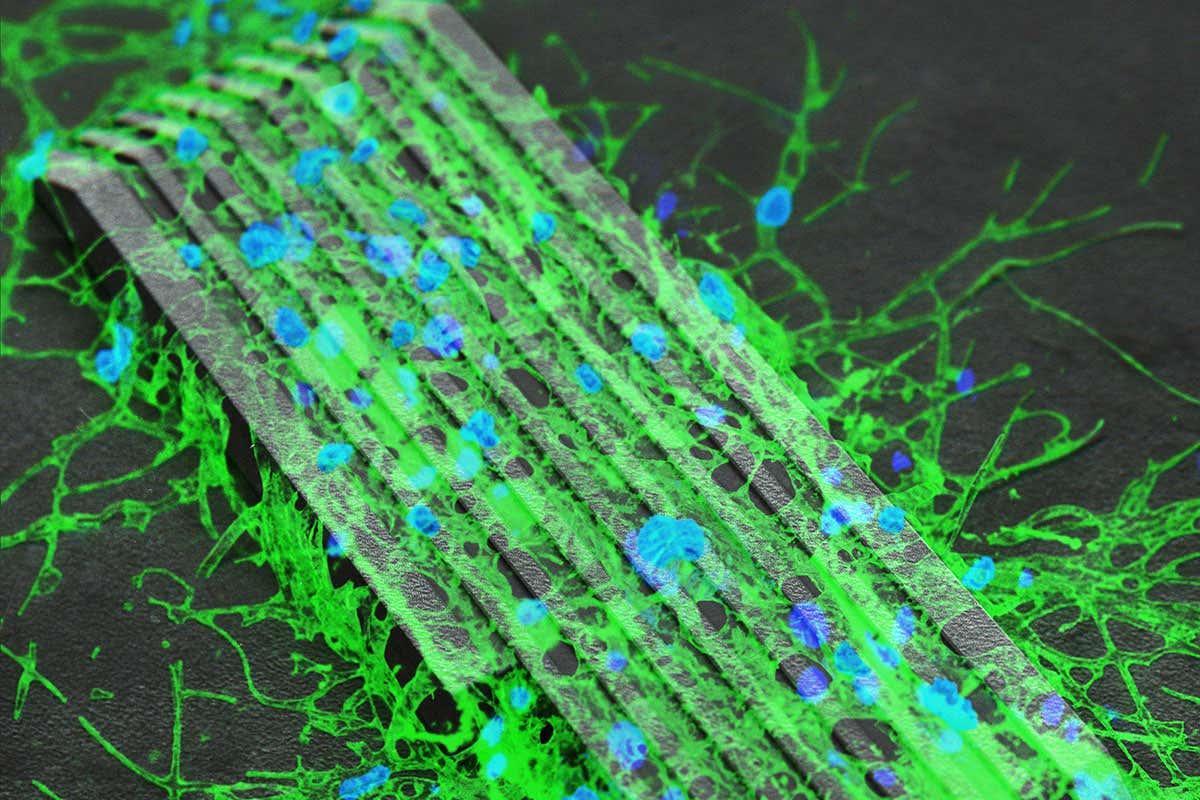
Here’s part of my PhD work on the synthesis of calix[4]arenes for testing against Human Papillomavirus pentamer formation @ISMSC2020 #ISMSCPoster #macrocycles12 Mauro Mocerino There is an image in the comments if you want to zoom in 😊

👩🏻💻 Jane Scott 🇦🇺 Pinaki ❄️ Binni Shah pentestmonkey FYI, I have updated the reverse shell cheat sheet: highon.coffee/blog/reverse-s…